Application Security , Governance & Risk Management , Next-Generation Technologies & Secure Development
Zoom Reverses Course, Removes Local Web Server
Controversial Design Decision Could Allow for an Ambush Video Call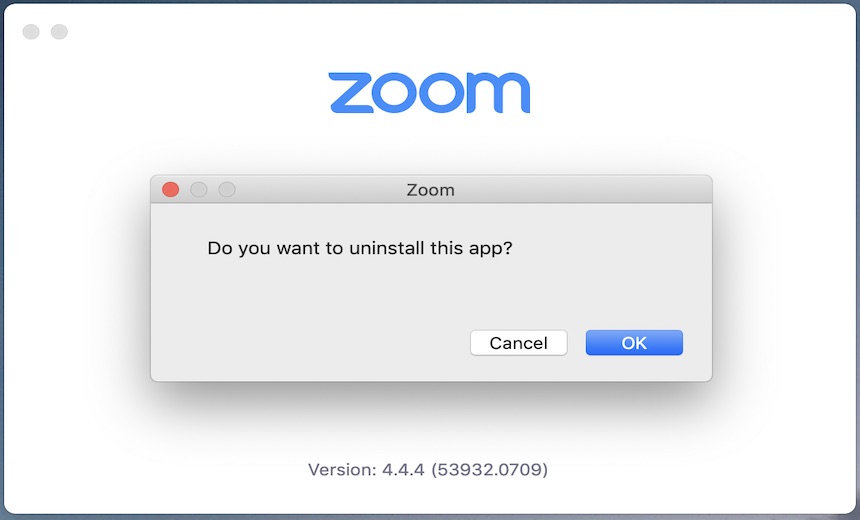
Editor’s Note: See latest update on this story.
See Also: A proactive approach to your agency's security
Video conferencing vendor Zoom has opted to make major changes to its Mac application after a security researcher found several weaknesses in it.
Jonathan Leitschuh, 25, a software engineer at Gradle in the Boston area, investigated how Zoom’s client software automatically opens on a Mac after someone clicks a meeting link in a browser window.

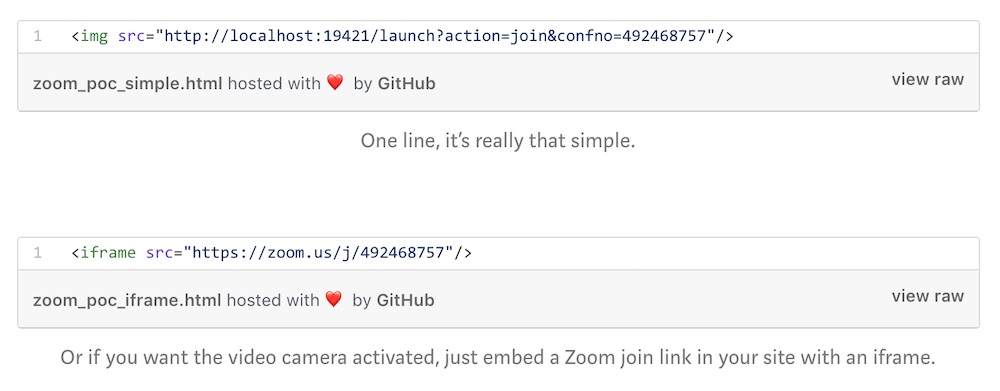
He found it would be possible with one line of code planted within an iframe on a web page to trigger the launch of Zoom’s client. Visiting that page would thrust a person into a conference call - and, depending on how a person had their Zoom settings configured, with their video camera on.
Zoom, which had 40 million users as of 2015, became a public company on April 18.
Leitschuh reported security issues to Zoom on March 26. He and the company had been communicating regularly since then but disagreed over the severity of some of his findings. The two sides appear to have reached a truce, with Zoom committing to Leitschuh’s security recommendations.
“There was certainly some friction in terms of his characterization of the vulnerability,” Zoom’s CISO, Richard Farley, tells Information Security Media Group.
Public Disclosure Creates Pressure
Leitschuh opted out of participating in Zoom’s private bug bounty program. The terms of the agreement would have required him not to disclose the bugs even after Zoom fixed them.
Instead, the researcher went public with his findings in a blog on Monday, which put public pressure on Zoom to make changes. Leitschuh says he told Zoom he planned on going public after a 90-day disclosure period, warning that consequences of taking his findings public could be painful for the company.
Public disclosure of vulnerabilities, however, can drive change that might not otherwise have happened, Leitschuh tells ISMG. “Some security teams just don’t have the power to effect change inside,” he says.
One of Leitschuh’s most alarming findings is that Zoom installs a local web server as part of its application. Even if Zoom is uninstalled, that local web server stays behind listening on port 19421. If someone then clicks on a Zoom meeting link, the local web server reinstalls Zoom, the researcher says.
That revelation drew surprise and criticism, including from Jake Williams, a former operator with the National Security Agency's Tailored Access Operations unit and founder of Rendition Infosec, a security consultancy in Atlanta. He tweeted:
Yesterday, I said it appeared Zoom has no SDLC. Part of SDLC is threat modeling. Zoom had 90 days to reevaluate whether an unauthenticated web server was a good idea. They held that line. Now they're backing away. Nobody in security said "this is good" - hence no SDLC. 1/3 https://t.co/wt9Tn0idgQ
— Jake Williams (@MalwareJake) July 9, 2019
Controversial Design: A Local Server
The reason Zoom installed a local web server was to get around a protection built into Safari 12 called cross-origin resource sharing policy, or CORS. That prevents a web page from launching a local application without an explicit permission window.
Zoom did this to streamline the video conferencing flow so users would not have to click another window to launch Zoom. But the workaround is considered questionable even though software vendors other than Zoom have implemented it.
It also meant that users who’d thought they’d uninstalled Zoom could still be forced into a video call if Leitschuh’s code was planted on a web page. The Zoom application would launch, so presumably the user would know they are in a conference, but the behaviour would be unexpected.

After Leitschuh published his blog post, Zoom doubled down on the local web server design decision. But it fell under heavy criticism, and Zoom reversed the decision on Tuesday. It issued an update for Zoom for Mac on Tuesday - version 4.4.53932.0709 - that removes the local web server.
Farley says “the consensus seems to be we’d rather have our users have to make an extra click to join a meeting than have this extra piece of code listening in on a port on a Mac.”
Leitschuh also reported a denial-of-service vulnerability, which Zoom patched in May.
Zoom: We’re Gonna Change
In addition to removing the local web server, Zoom says it now plans other changes.
This weekend, it will release another patch that will change the default preference on whether a person’s video camera is on. Zoom tends to default to having video on even if a person flicked it off at a previous time.
The patch will keep a video camera off for future meetings if someone has selected that preference once, Zoom says. Leitschuh pointed out in his blog that it's possible to ambush call someone and force the recipient’s camera to be turned on via settings in Zoom’s call interface.
Zoom says that behavior was only possible if the call recipient had not turned video off. But as pointed out before, Zoom defaulted to having video on.
Zoom also plans to add a feature to allow users to manually uninstall the application. “Once the patch is deployed, a new menu option will appear that says ‘Uninstall Zoom.’ By clicking that button, Zoom will be completely removed from the user’s device along with the user’s saved settings,” it writes.