Yahoo Spotted Mega Breach in 2014
As Breach Bill Hits $1 Million, Search Giant Investigates Who Knew What - and When
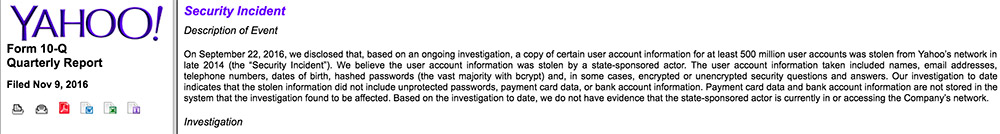
Yahoo's postmortem into one of the largest data breaches of all time continues to reveal damning information. In a Nov. 9 filing to the Securities and Exchange Commission, Yahoo says it believes that a state-sponsored attacker - which it has blamed for the compromise of at least 500 million accounts - was in its network in 2014, and reports that it detected the related intrusion at the time.
See Also: HIPAA Compliance: What The Healthcare Industry Needs To Know
The disclosure complicates Yahoo's recovery from the breach, which according to the SEC filing has cost the company $1 million so far. It also casts doubts about whether Verizon will stick with its $4.8 billion bid to buy Yahoo, which it made prior to the breach details becoming public.
Yahoo tells the SEC that an independent committee is investigating how much company officials knew in 2014 about the intrusion, after it was detected. The committee is being advised by an independent counsel and a forensic expert, the filing adds. The broader investigation, which includes cooperation with law enforcement officials, also continues.
The $1 million spent so far on breach recovery has not had a material impact on its finances, according to Yahoo's filing, but the company also notes that it does not carry cybersecurity insurance, and its related costs are likely to rise. Notably, the company is facing 23 putative consumer class-action suits in U.S. federal and state courts by people who claim to have been harmed by the breach, the filing says.
Yahoo says it is not possible to estimate the potential losses from those lawsuits, since the proceedings are in early stages (see Why So Many Data Breach Lawsuits Fail).
Scrutiny Mounts
Regulators and prosecutors are watching Yahoo's breach investigation closely. Yahoo says it is providing information to the Federal Trade Commission, SEC, various state attorneys general and the U.S. Attorney's office for the Southern District of New York.
In Europe, meanwhile, data privacy officials have also expressed their concerns to Yahoo. In a letter to the search giant, Isabelle Falque-Pierrotin, chair of the Article 29 Working Party - the WP29 is composed of the EU's data protection officers - says that Yahoo must inform Europeans whose personal information was compromised "in a quick, comprehensive and easily understood manner so that Yahoo users across Europe will understand any action they need to take as a result of the breach."
In its SEC filing, Yahoo notes that actions by those organizations could result in "civil or criminal penalties which could, among other things, materially increase our data security costs, and affect how we operate our systems and collect and use customer and user information."
'State-Sponsored Actor' Claim Questioned
The filing is revealing because it's the company's first acknowledgement that it may have detected the 2014 breach shortly after it happened.
Yahoo explains that in July 2016 it investigated a purported breach but could not substantiate a hacker's claim of having obtained Yahoo user data. It then launched a broader security review, which included "a review of prior access to the company's network by a state-sponsored actor that the company had identified in late 2014." The company now believes that attacker is the same one who compromised 500 million accounts.
But one private security company, InfoArmor, has disputed Yahoo's claim that it was hacked by a state-sponsored actor, arguing instead that the attack was launched by a group of professional cybercriminals from Eastern Europe (see Yahoo Hacked by Cybercrime Gang, Security Firm Reports).
Breach Details
On Sept. 22, Yahoo began notifying regulators and users of a massive breach. It was the latest in a spate of mega-breaches to come to light - some historical - involving such companies as LinkedIn, MySpace, Dropbox and Tumblr (see Dropbox's Big, Bad, Belated Breach Notification).
Yahoo also provided technical details relating to how hackers accessed accounts, writing that an intruder "created cookies that could have enabled such intruder to bypass the need for a password to access certain users' accounts or account information."
Cookies are small data files that websites or services place on users' devices. After someone logs into a web service, a cookie will allow someone to repeatedly access a service without requiring login details again. Those types of cookies are usually short-lived and set with an expiration time.
The breach included the compromise of encrypted passwords, names, email addresses, phone numbers and birthdates. Also stolen were the security questions and answers users had selected to verify their accounts, only some of which were encrypted. No payment card or bank account information was compromised, Yahoo said.
How Will Breach Impact Verizon Deal?
With the breach having occurred in 2014 and been detected by the search giant, Yahoo may now face a backlash if regulators conclude that the company waited two years to warn affected users. Many regulators have been moving to make technology companies more accountable for computer security incidents that threaten user data.
The data breach has already complicated Yahoo's acquisition by Verizon, which agreed on July 23 to buy the once-hot internet giant for $4.8 billion. Yahoo warns in its filing that the deal may now not be completed quickly or at all (see Verizon Reportedly Demands $1B Yahoo Discount After Breach).
Either Yahoo or Verizon could back out of the deal. According to the filing, if the stock-purchase agreement is nixed, Yahoo may also have to pay Verizon a termination fee close to $145 million.
It also warned that the ongoing investigation into the data breach, combined with civil litigation and regulatory scrutiny, could have a "material" effect on the business, meaning a significant impact on its finances or operations.