Sponsored by Cyberark
Sponsored by CyberGRX
Critical Capabilities for IT Vendor Risk Management Tools
Sponsored by BeyondTrust
The Top 5 Remote Access Problems
Sponsored by CyberGRX
The Elements of a Holistic Third-Party Risk Strategy
Sponsored by IronNet
6 Misconceptions About Collective Defense for Cybersecurity
Sponsored by CyberGRX
Third-Party Cyber Risks in the Financial Industry
Sponsored by CyberGRX
Third-Party Cyber Risks in the Oil & Gas Industry
Sponsored by CyberGRX
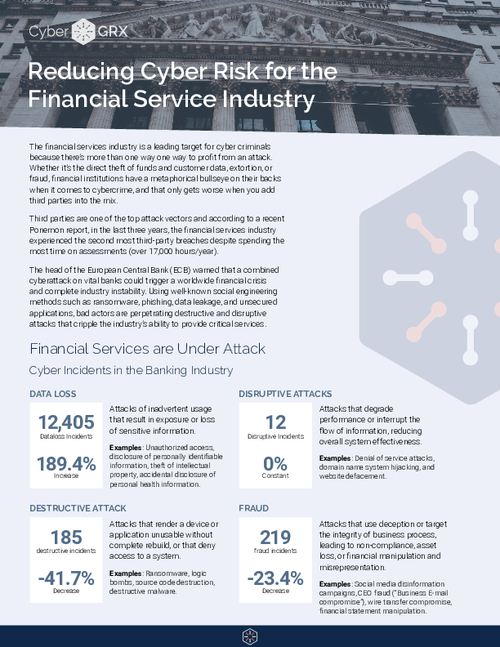
Reducing Cyber Risk for the Financial Service Industry
Sponsored by CyberGRX
CyberGRX Exchange Insights
Sponsored by IronNet
Dynamic Detection for Dynamic Threats
Sponsored by Secure Code Warrior
Why empowering developers to write secure code is the next wave of application security
Sponsored by CybelAngel
Flying Blind in Third-party Ecosystems
Sponsored by IronNet
A Web of Weak Spots: Securing Your Supply Chain with NDR and Collective Defense
Sponsored by Nominet
The Risks, Threats and Solutions That Matter Most to Federal Government Agencies
Sponsored by CyberGRX