Sponsored by HelpSystems
Sponsored by Veeam
2020 Data Protection Trends for Financial Services
Sponsored by Imperva
The Three Keys to Secure and Successful Cloud Migrations
Sponsored by CyberArk
Top 10 Considerations When Choosing a Privileged Access Management Solution
Sponsored by Splunk
Nucleus Research: The Unexpected Challenges of Cloud Transformation
Sponsored by Auth0
Fixing Broken Authentication
Sponsored by CrowdStrike
2020 Threat Hunting Report: Insights from the CrowdStrike Overwatch Team
Sponsored by Zscaler
Powerco energises remote working in record time with Zscaler
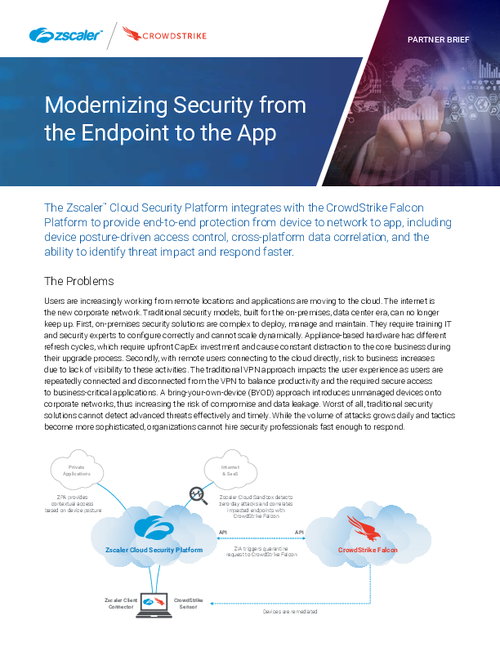
Sponsored by CrowdStrike & Zscaler
Modernizing Security from the Endpoint to the App
Sponsored by IBM
QRadar: Detecting Threats As Your Business Grows
Sponsored by Okta
One-minute Webinar: Zero Trust in Practice
Sponsored by CybelAngel
Evolution of Ransomware Gangs
Sponsored by IBM
Securing the Journey to Cloud
Sponsored by CybelAngel