Sponsored by Splunk
Sponsored by Splunk
The Guide to Modern APM: Essentials for Your Cloud-native Journey
Sponsored by Splunk
5 Things to Consider When Choosing an APM Tool
Sponsored by Splunk
GigaOm Cloud Observability Report
Sponsored by Splunk
A Beginner's Guide to Kubernetes Monitoring
Sponsored by F5 Networks
Apps are Essential so your WAF must be effective
Sponsored by F5 Networks
WAF for Dummies Digital Book
Sponsored by F5 Networks
Choosing the WAF that's Right for You
Sponsored by Okta
Kingsborough Community College
Sponsored by Okta
Enhance Security Posture for State and Local Agencies
Sponsored by Okta
Kingsborough Community College
Sponsored by Prove
Get Smarter About Fortifying your Multi-Factor Authentication
Sponsored by Qualys Inc.
An All-in-One Vulnerability Management, Detection, and Response Solution
Sponsored by Qualys Inc.
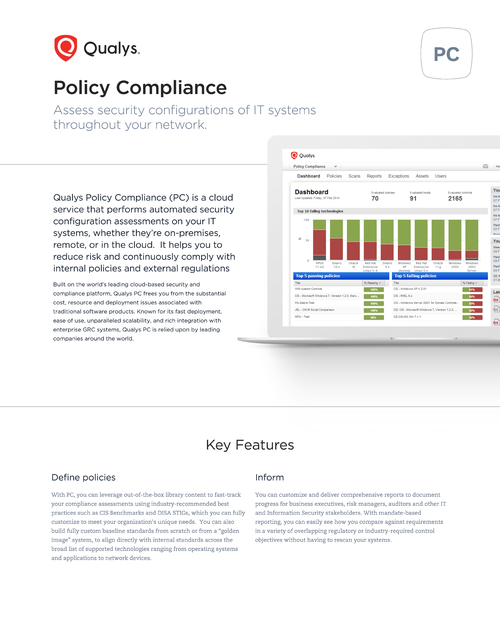
Cloud Based Security & Policy Compliance
Sponsored by Cisco