Sponsored by Duo Security
Sponsored by Perimeter 81
ZTNA vs On-Premises Firewall VPN: The Ultimate Guide
Sponsored by Duo Security
How to Guide on Evaluating Two-Factor Authentication
Sponsored by Abnormal Security
Insights on Financial Supply Chain Compromise
Sponsored by HCL BigFix
Ransomware Preparedness: The Critical Roles of Endpoint Management & NIST Framework
Sponsored by HCL BigFix
The 5 Step Approach to Alleviate Endpoint Management Tool Sprawl
Sponsored by Elastic Security
Cybersecurity solutions for a riskier world
Sponsored by Elastic Security
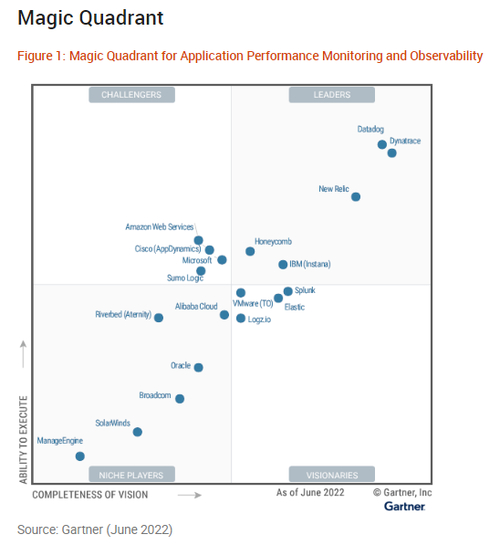
Elastic named a Visionary in the 2022 Gartner® Magic Quadrant™ for APM and Observability
Sponsored by GoTo
Small IT Department Structure: Meeting The Needs of Business
Sponsored by GoTo
Small IT Department Structure: Meeting The Needs of Business
Sponsored by GoTo
IT Service Management for SMBs in a Remote-First World
Sponsored by GoTo
5 Tips for Easing Common IT Frustrations
Sponsored by IBM
Forrester: Total Economic Impact Of IBM Spectrum Scale
Sponsored by IBM
Multicloud Data Integration for Data Leaders
Sponsored by IBM