Sponsored by Palo Alto Networks
Sponsored by Symantec, a Division of Broadcom
Tech Spotlight: Endpoint Security
Sponsored by BeyondTrust
Enable & Secure Your Remote Workforce
Sponsored by BeyondTrust
5 Critical Steps in Your Endpoint Security Strategy
Sponsored by Sotero
Data Security Advances Help Companies Drive Business Innovation
Sponsored by Red Canary
2021 EDR Buyer’s Guide
Sponsored by Eclypsium
The 2021 Cybersecurity Executive Order
Sponsored by Splunk
The Essential Guide to Container Monitoring
Sponsored by Splunk
Monitoring Microservices on Kubernetes
Sponsored by Splunk
A Beginner's Guide to Kubernetes Monitoring
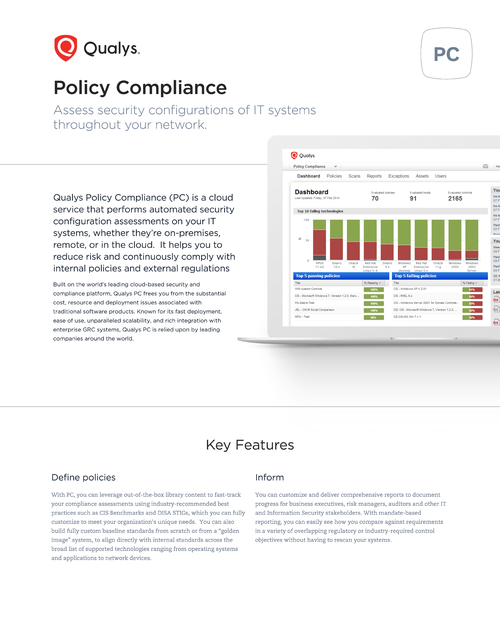
Sponsored by Qualys Inc.
Cloud Based Security & Policy Compliance
Sponsored by FireEye
The Definitive Guide to Security Validation
Sponsored by Silicon Labs
Preparing for Next-Generation Cyber Attacks on IoT
Sponsored by VMware
Modernize Endpoint Protection and Leave Your Legacy Challenges Behind
Sponsored by VMware