Sponsored by Tata Communicatiions
The State of Organizations' Security Posture as of Q1 2018
Sponsored by VMware and Intel
Protecting Data, Improving Agility, and Staying Compliant in the Mobile Cloud Era
Sponsored by NICE Actimize
The Sound of Secure Transactions: Voice Biometrics and PSD2 Compliance
Sponsored by Bugcrowd
How the Financial Services Industry is Staying a Step Ahead of Cyberattacks in 2018
Sponsored by Bugcrowd
What Motivates a Bug Hunter: What's In It For Them?
Sponsored by IBM
A New Generation of Fraud Defenses
Sponsored by Red Canary
PowerShell Deep Dive: A United Threat Research Report
Sponsored by Red Canary
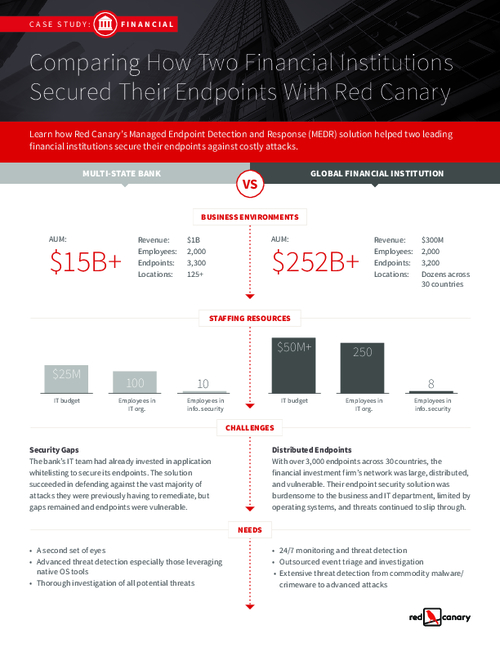
Case Study: How Two Financial Institutions Secured Their Endpoints
Sponsored by Red Canary
Case Study: How an Investment Firm Uses Multiple MSSPs
Sponsored by Illumio
Micro-Segmentation: Fast Becoming a Foundational Layer of Security Architecture
Sponsored by iovation
10 Multi-Factor Authentication (MFA) Platform Buying Criteria
Sponsored by IBM