Cybercrime as-a-service , Endpoint Security , Fraud Management & Cybercrime
Toolkit Generates Malicious Office Macro Malware
'Rubella Macro Builder' Available on Cybercrime Underground for $40 Per Month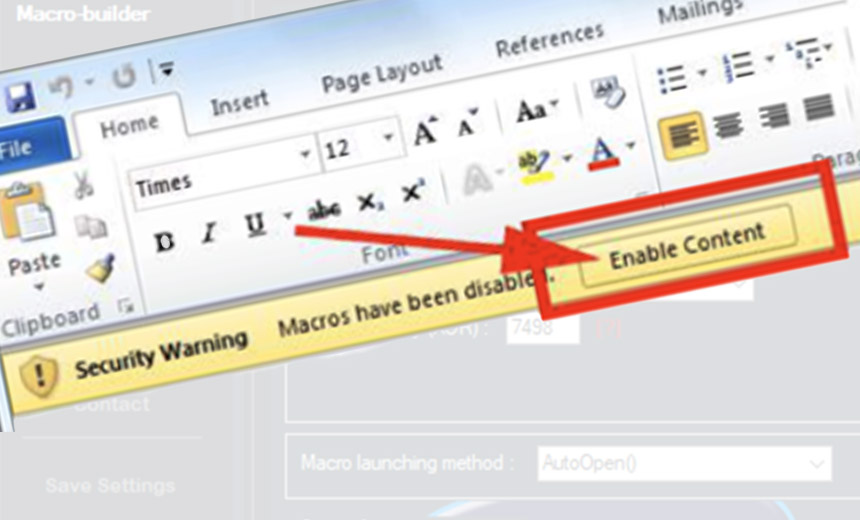
Are you a fraudster craving an easy way to generate Microsoft Office documents with embedded malicious macros designed to serve as droppers that install banking Trojans onto a victim's PC?
See Also: An Assume-Breach Mindset: 4 Steps to Protect What Attackers are After
As always, the cybercrime ecosystem is happy help support such illegal - albeit potentially lucrative - pursuits (see Cybercrime-as-a-Service Economy: Stronger Than Ever).
One recent option comes in the form of a toolkit called Rubella Macro Builder, which is "cheap, fast and can defeat basic static anti-virus detection," Flashpoint researchers Vitali Kremez, Amina Bashir and Paul Burbage say in a new report.
"Typically distributed to its intended victims via Microsoft Word or Excel email attachments, the Rubella-generated malware acts as a first-stage loader for other subsequent malware downloads and installations on targeted machines," the researchers say.
So far it's been spotted for sale on at least one "top-tier Russian hacking forum" where it first appeared in late February for $500 per month before being discounted in April to $120 for a three-month subscription, the researchers say. While the forum appears to be Russian, many posts are in English as well (see What Drives Eastern European Cybercriminals?).
"The actor marketing Rubella Macro Builder is likely operating in the western hemisphere, based on their good command of writing English in their forum posts," Paul Burbage, a senior malware researcher at Flashpoint, tells Information Security Media Group.
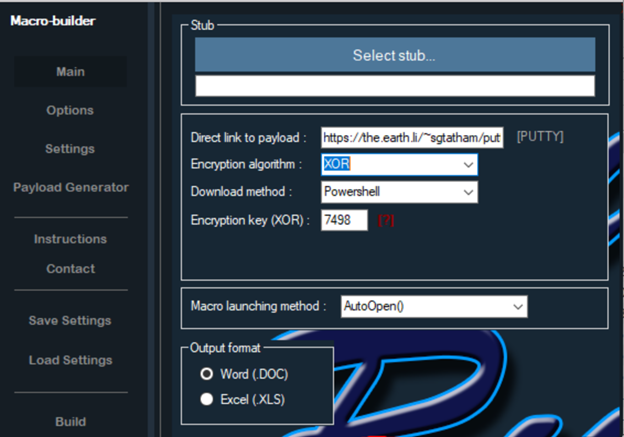
The toolkit provides various encryption algorithms and methods for downloading and executing additional attack code and can also be skinned with a variety of "social engineering decoy themes," according to Flashpoint. It's designed to simplify the process of infecting PCs via macros - a down-and-dirty and very popular technique. Macros offer a relatively simple attack, technologically speaking, that succeeds if attackers can trick the recipient into enabling macros in Microsoft Office, which are disabled by default because they pose a significant risk to users (see Hello! Can You Please Enable Macros?).
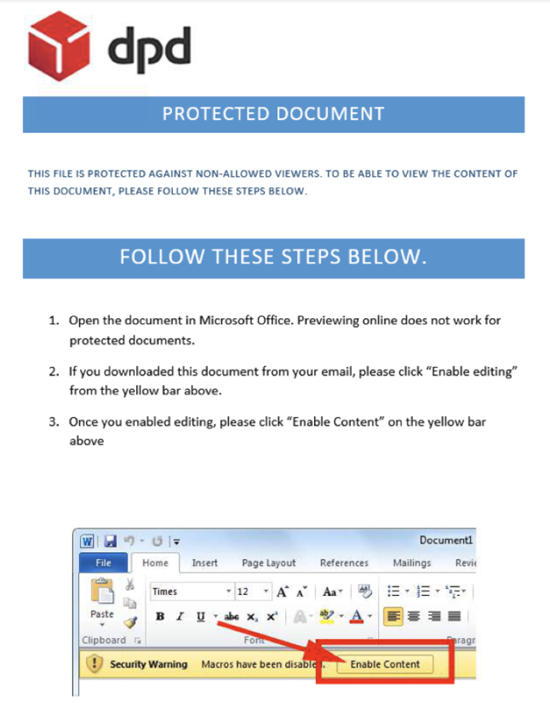
"The malicious documents that are generated using the Rubella Macro Builder are typically attached to emails and blasted out in massive spam campaigns," Burbage says. "There is not any particular country or organization being particularly targeted."
Users: Panda and Gootkit Gangs
So far, Flashpoint has tied Rubella-generated Office documents with malicious macros embedded to two gangs. Some Rubella malware has installed version 2.6.6 of the Panda banking Trojan, which is yet another variant of the venerable Zeus banking Trojan, for which the source code leaked in 2011 (see Zeus Banking Trojan Spawn: Alive and Kicking).
Other Rubella malware infections, meanwhile, have installed Gootkit banking malware.
"It is likely that the gangs are customers of the actor offering Rubella on the underground," the Flashpoint researchers say. "Specifically, the gangs behind the Panda malware distribution appear to have targeted customers through various social media platforms, as well as an Australian financial institution, through Panda's webinject functionality," the researchers say.
Webinject - aka Web injection - capabilities in malware refers to the ability to display real-looking but fake versions of banking websites, enabling attackers to not only intercept users' credentials, but also hide malevolent activity, such as draining bank accounts (see Zeus-Derived Malware Continues to Pwn POS Devices).
Macro Madness Continues
Rubella isn't the first toolkit that promises to take the hassle out of generating malicious macros.
"Historically there have been some malicious document builders used to generate macros and embed them in Office documents," Burbage says. "One example is the Microsoft Word Intruder [MWI] toolkit. There are also functionally similar toolkits that are used in authorized penetration testing scenarios such as the open source application SET [Social Engineer's Toolkit] or the commercial penetration testing platform Cobalt Strike."
Beyond macros in Office documents, attackers also continue to rely on numerous other techniques for attempting to execute arbitrary code on PCs. Other top options, Burbage says, include using malicious JavaScript and Visual Basic scripts to serve as stage-one loaders for installing subsequent waves of more malicious code onto PCs.





















