Endpoint Security , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development
Threats: Social Engineering and Malicious Spam Dominate
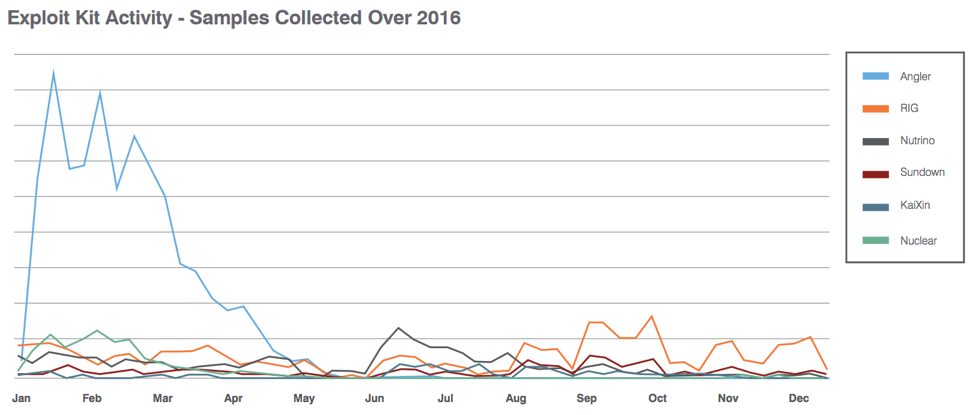
Exploits Kits, Once Formidable, Continue to Decline
Good news: Exploits kits remain in decline, thanks in large part to concerted efforts to disrupt their efficacy.
See Also: Break the Attack Chain with XDR
Unfortunately, criminals are focusing instead on social engineering attacks - including tech-support scams - and malicious spam campaigns as malware distribution mechanisms, as noted by Brad Duncan, a threat intelligence analyst for the Unit 42 security research group at Palo Alto Networks, in a Wednesday blog post.
The decline and fall of exploits kits is significant. Such toolkits made it easy for criminals with scant technical skills to infect legitimate websites and use them to launch drive-by attacks at visitors, often via a malicious inline frame - iframe - added to web pages. Exploit kits typically target known vulnerabilities in Internet Explorer as well as outdated and vulnerable browser plug-ins such as Adobe Flash Player, Oracle's Java Plugin Runtime Environment and Microsoft Silverlight.
Several factors appear to be contributing to exploit kits' fall from grace:
- Smaller attack surface: Fewer users today run IE or Edge as their browser of choice. In the past, outdated IE - and a host of outdated plug-ins - remained a top attack vector for exploit-kit builders. But such attack toolkits have been much less effective against the likes of Google Chrome, Duncan says, thanks to rapid code-update cycles designed to eliminate older versions with known flaws from users' PCs. Today, nearly half of all browsers are Chrome, compared with IE 11 at 14 percent and Edge at 5 percent, Duncan reports.
- Zero-day famine: The best exploit kits, historically speaking, were the ones that had exploits for the greatest number of zero-day flaws, since that would allow attacks to spread as fast and furiously as possible. But no exploit kit has included exploits for a new zero-day flaw for more than a year, say researchers at security firm Proofpoint.
- Domain shadowing blocks: Attackers since 2010 have been using what's now referred to as domain shadowing - "compromising existing domains and using their DNS as a piece of attack infrastructure," as defined by William MacArthur, a threat researcher at RiskIQ. By "hijacking access to the domain management system and injecting rogue records alongside the domain holder's own legitimate resolution records," attackers could create malicious pages that look legitimate, thus bypassing many types of security defenses. But Duncan notes that researchers at security firms - including Cisco Talos and RSA - have been working with hosting providers to successfully block many domain-shadowing attacks.
Exploit Kit Graveyard
Cybercrime is a business. As exploit kits' efficacy has decreased, fewer criminals appear to be subscribing to the services, and that's apparently driven many providers out of business. In 2015, for example, once-dominant players such as Sweet Orange and Fiesta vanished. In 2016, Angler and Nuclear closed up shop. And this year, Neutrino has exited the market, with its developers reportedly blaming poor profits.
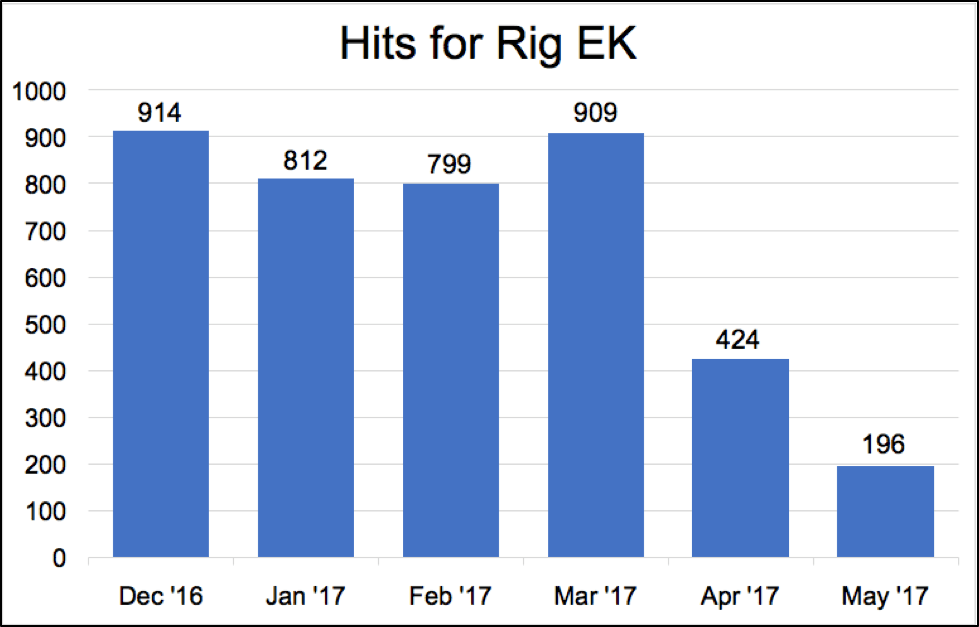
Whereas exploit kits charge a subscription fee, attackers today can also access an array of free and powerful attack tools, including keyloggers and remote-access Trojans, or RATs. As anti-malware site Bleeping Computer recently reported, many attackers - including Nigerian crime gangs - distribute these attack tools via phishing emails or spam to help them gather information on targets and run lucrative business email compromise scams. One judge in New York state, for example, reported Friday to police that she lost $1 million to a BEC scam.
Attackers Diversify
Some exploit kits remain. But Palo Alto reports that two big cybercrime operations - EITest and pseudo-Darkleech - ceased using Rig exploit kit, one of the dominant players, for distribution, as of April.
Security researchers say some recent attack campaigns by groups that relied heavily on exploit kits are now trying to trick U.K. and U.S. users into calling a fake tech-support phone number. Victims in other countries may get hit with banking malware or ransomware instead.
Sometimes, such attacks eventually end up using exploit kits. According to "Brad," aka @malware_traffic, the researcher behind Malware-Traffic-Analysis.net, some recent EITest campaigns target U.S. and British victims with tech-support scams, while directing users in other countries to sites infected with Rig, to try and infect their system with Mole ransomware. The Mole variant that's been seen used in attacks - as recently as June 15 - crypto-locks PCs and demands 0.5 bitcoins, currently worth $1,333, from victims for a decryption key.
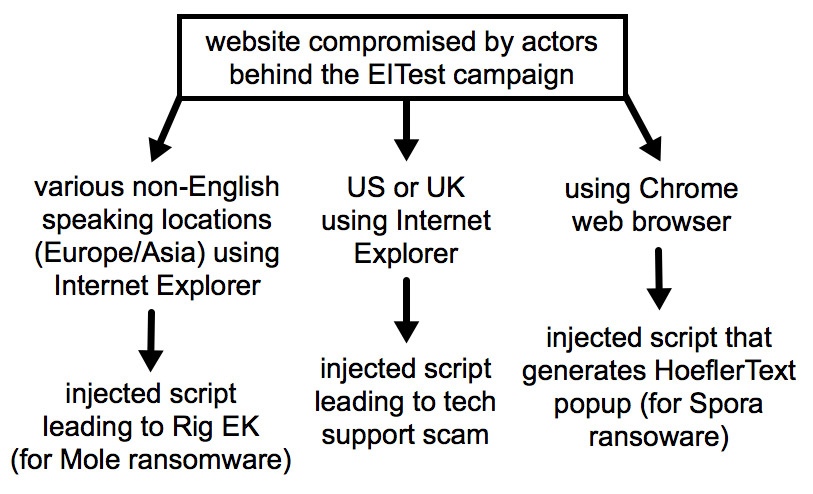
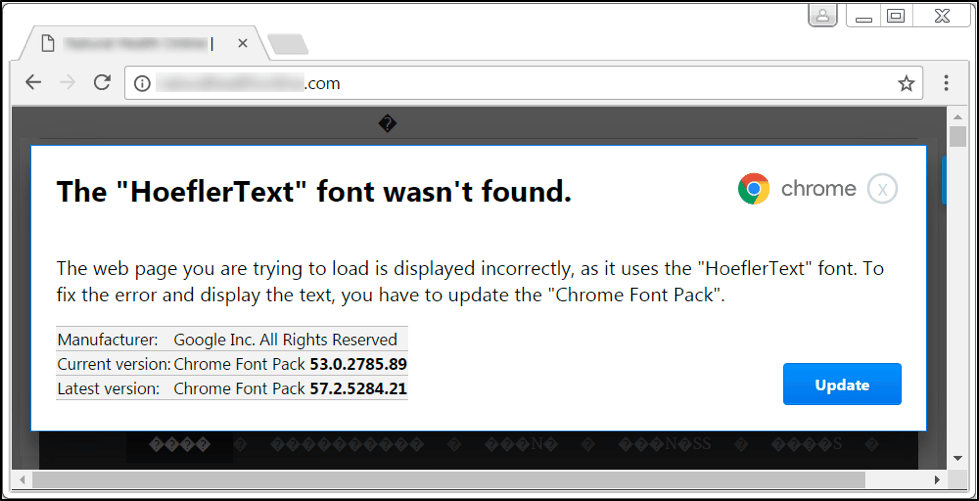
The researcher also reports that attackers continue to target Chrome users, in some cases using a fake "font not found" popup that tries to infect a system with Spora ransomware. Such scams typically claim that a font, such as Hoefler Text, must be downloaded.
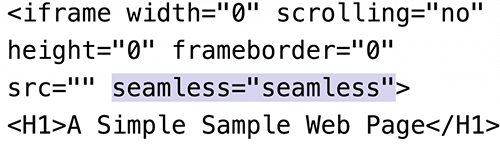
The developers behind Rig, meanwhile, continue to experiment with alternate infection mechanisms, including so-called seamless attacks, which make use of deprecated HTML designed to make an iframe look like it's part of a document.
Some recent seamless attacks, according to Cisco Talos, have been serving the venerable Ramnit banking Trojan.
Malvertising Still a Threat
Some malvertising - malicious advertising - campaigns continue to tap exploit kits. One recent ransomware attack that snared several British universities, including University College London, appears to have been distributed via malvertising that led victims to sites infected with the Astrum, aka Stegano, exploit kit. The Proofpoint security researcher known as Kafeine traced the attacks to a malvertising group known as AdGholas.
Another malvertising campaign, discovered earlier this month and potentially tied to the RoughTed operation that's been running for over a year, also led to Rig.
As that suggests, exploit kits may be diminished, but they are not extinct and remain a component in many attackers' campaigns. Duncan at Palo Alto Networks says exploit kits are now only a "relatively minor factor in today's threat landscape compared to social engineering schemes and malspam." Even so, he adds, security researchers continue to log fresh attacks - launched by the likes of the Rig and Magnitude exploit kits - almost daily.




















