Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management
TA505 Group Hides Malware in Legitimate Certificates
APT Group Targets Banks With Backdoor Malware to Penetrate Networks
(This story has been updated.)
See Also: Cybersecurity for the SMB
TA505, a sophisticated advanced persistent threat group, is now using legitimately signed certificates to disguise malware that can penetrate banking networks, security researchers warn in a new report.
The signed and verified certificates hide relatively new malware called ServHelper, which acts as a backdoor into the target network that allows for a host of activities, including reconnaissance, information stealing as well as communicating with command-and-control servers, according to Cybereason, which published its findings on Thursday.
In operation for at least five years, TA505 mainly targets banks and financial institutions, but it has also attacked retailers and other businesses. Over the years, the group has been implicated in large-scale spam campaigns, and it has distributed Trojans such as Dridex and The Trick as well as Locky and Jaff ransomware, according to Proofpoint, which published a detailed analysis of the group in 2017.
The group is known to have carried out attacks in North America, Asia, Africa and South America, researchers say.
The use of legitimate certificates to hide malware takes the group's activity up a notch in terms of sophistication and stealth, says Eli Salem the lead researcher on the Cybereason report.
"Signed and verified files are considered 'safe' because some authorized entity signed and certified them," Salem tells Information Security Media Group. "So there is a possibility that security analysts could lapse into a false sense of security when they encounter such files and will not wonder about their true nature and thus miss the malicious activity."
Troubling Trends With Certificates
The TA505 attack strategy using new malware was spotted by Cybereason when the group targeted one of the company's clients - a financial institution that the researchers did not identify in Thursday's report. The security firm says it managed to stop the incident before the group committed extensive damage.
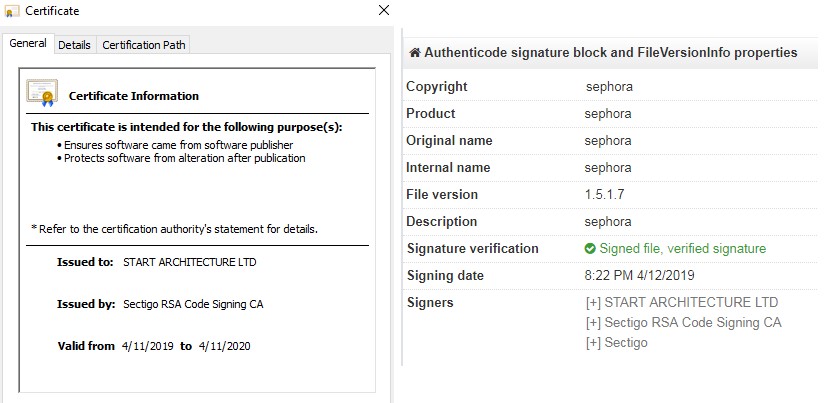
"This particular research focuses on one of our customers, but TA505's activity is pervasive in many regions around the world," Salem says. "From previous analysis of the malware they distribute and the way they operated in the past, financial motivation is most likely one of their main goals."
The latest TA505 operations started in early April with a spear-phishing campaign aimed at several businesses. In the target company that Cybereason examined, the malicious emails honed in on a small number of accounts, meaning the group likely did reconnaissance before the attack to find specific employees.
When researchers dissected the attack, they found malware hiding in a signed and verified certificate from Sectigo RSA Code Signing CA. This same type of certificate was used to spread a version of the LockerGoga ransomware earlier this year, according to security reports.
Earlier this week, Kaspersky Lab published an update on "Operation Shadowhammer," which also involved manipulating certificates to hide malware (see: 'ShadowHammer' Spreads Across Online Gaming Supply Chain).
The use of certificates, Cybereason says in its new report on TA505, "gives the malware the appearance of legitimacy when dealing with various defense mechanisms. Furthermore, the malware was signed mere hours prior to the attack - an indication of the operation's deliberate timeline and nature."
In a statement sent to ISMG, Tim Callan, a senior fellow at Sectigo, says the company "revokes certificates used in malware attacks and does not issue certificates to known malware purveyors. We encourage security researchers to report instances of malware employing Sectigo certificates at signedmalwarealert@sectigo.com."
Anatomy of an Attack
Following the phishing emails, the TA505 attack that Cybereason documented started with placing malware within the network using "living off the land" binaries, which are legitimate binaries within systems that attackers manipulate for their own purposes.
The use of these binaries creates persistence within the network, giving the threat actors time to map the systems they want to target, gather additional information and then send this back to the command-and-control server, according to Cybereason. This technique also allows TA505 to hide its activities, because it's using legitimate Windows binaries as well as native operating system processes.
Cybereason found that these activities, combined with the legitimate certificates, helped disguise the delivery of a malicious payload that attempted to install the ServHelper backdoor.
In addition to its ability to handle reconnaissance and information gathering, ServHelper can also let the attackers know if the removal of all the evidence within the network and the infected systems is necessary. Researchers found a module called pegas.dll, which helps direct the reconnaissance and information stealing aspects of ServHelper and helps it communicate with one of several command-and-control servers.
ServHelper also helps the attack group find those machines in the network that have administrative privileges, the report found.
"Similar to many kinds of backdoor malware, ServHelper is able to lurk quietly in a sleep state," according to the report. "This is a known backdoor characteristic that lets the malware stay under the radar and strike at the exact time the attacker wants to activate additional malicious activities."
Ongoing Threat to Banks
Cybereason's Salem believes that these types of attacks will continue because banking employees are likely to continue to fall victim to phishing emails designed to gather credentials and passwords that pave the way for deeper access to networks. And the TA505 group stays in networks for extended periods, he warns.
"Their persistence is what makes it difficult for banks and financial institutions to combat them," Salem says. "A bank's cyber defenses are critical today, and since cyber actors have lots of time on their hands, it is a guarantee that they will eventually get in because no defense is foolproof."






















