Application Security & Online Fraud , Critical Infrastructure Security , Next-Generation Technologies & Secure Development
Report: Iowa Caucus App Vulnerable to Hacking
Veracode Finds Insecure Data Transmission, ProPublica Reports
A review by two computer security experts of the mobile app that malfunctioned during Iowa’s critical tally of the Democratic Party’s caucus has uncovered that it insecurely sends data, ProPublica reports.
See Also: 12 Immutable Rules for Observability
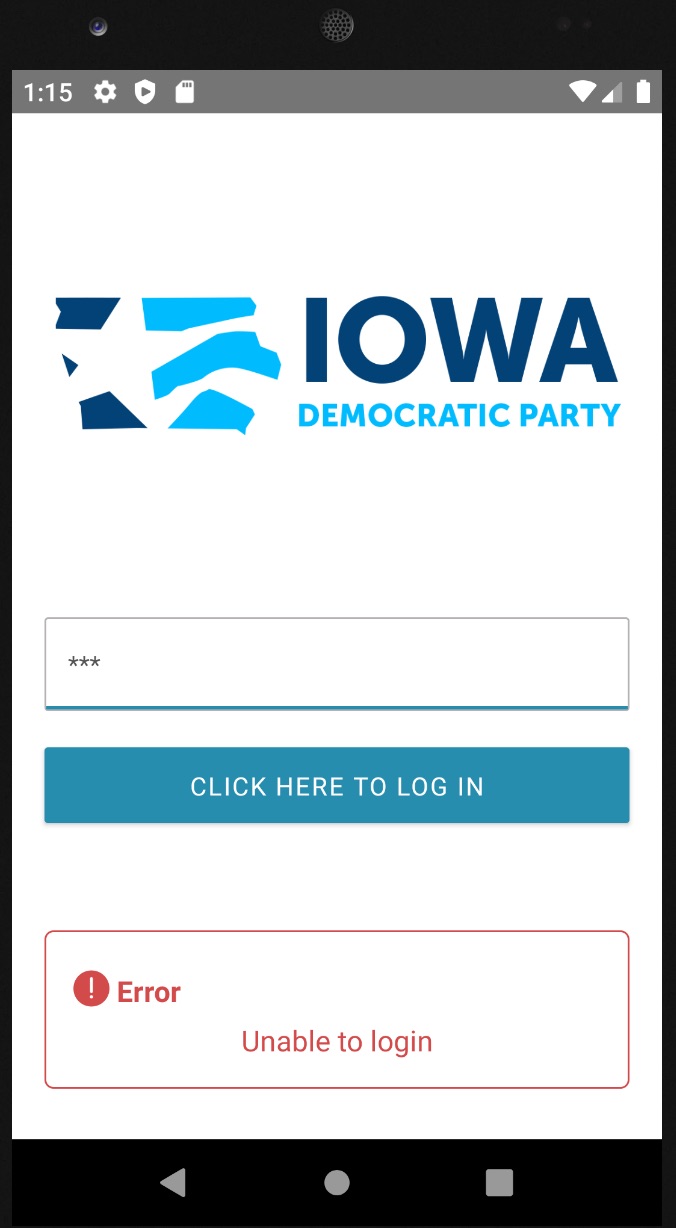
ProPublica obtained a copy of the app, called the IowaReporterApp, from an Iowa precinct chair and supplied it to Veracode, an application security testing company.
Veracode found that the app was vulnerable to hacking “because of a lack of safeguards, transmissions to and from the phone were left largely unprotected,” it reported.
The actual vulnerability isn’t described. Chris Wysopal, who is Veracode’s founder, CTO and CISO, tweeted on Wednesday that “per our disclosure policy we won’t be releasing details publicly.”
Vercode’s finding was confirmed by J. Alex Halderman, who is chief scientist at Censys and a computer science professor at the University of Michigan. ProPublica quotes him as saying: “This is an extremely serious vulnerability.”
Shadow Inc., the Colorado-based technology consultancy that developed the app, couldn’t be immediately reached for comment. But its founder, Gerard Niemira, told ProPublica that “our app underwent multiple, rigorous tests by a third party.”
“As with all software, sometimes vulnerabilities are discovered after they are released,” he says.
The app is poised for a wider review. Vice’s Motherboard has made available the Android APK. Motherboard reports that Shadow Inc. has shut down the back-end servers and the app is no longer being used.
Experts interviewed by Motherboard concluded the app appeared to be hastily thrown together. It also included hard-coded API keys, which although not unheard of in an app also is not the best practice, Motherboard reported.
App Failures
Iowa’s Democratic Party caucus was thrown into chaos after the mobile app deployed among precinct workers failed because of a variety of technical problems (see: The Iowa Caucus: No Hacking, But a Bungled Risk Matrix).
The issues ranged from difficulties in downloading the app to problems signing in and transmitting tallies. The app was designed as a faster way to report results, rather than over the phone, as had been the tradition.
Per our disclosure policy we won’t be releasing details publicly.
— Chris Wysopal (@WeldPond) February 5, 2020
In an interview with Bloomberg, Niemira says Shadow Inc. identified the bug around 10 p.m. on Monday night. Once the bug was fixed, it was then capable of sending data to the Democratic Party’s data warehouse. The malfunction was because of a data formatting issue, Niemira says.
Questions have been raised as to why Iowa’s Democratic Party chose to deploy an app that was designed over just a couple of months before the first major caucus of the election season. The failure of the app immediately spawned conspiracy theories that falsely exploited the error as a sign that something untoward was afoot.
Iowa’s Democratic Party didn’t entirely rely on the app to tally preferences. It kept a robust paper backup, which is being used to get the accurate results.
No HTTPS?
While the actual vulnerability in the IowaReporterApp isn’t described, there is an obvious suspect.
Insecure data transmission could mean that app didn’t use HTTPS encryption, which encrypts data traffic between a device and a server. If data was sent over HTTP, anyone on the same network could see the traffic and potentially tamper with it.
ProPublica gave another clue as to the issue: “An attack would have required some degree of sophistication, but it would have been much easier to pull off had a precinct worker used an open Wi-Fi hotspot to report votes instead of a cell data plan.”
Halderman tells ProPublica that “an adversary could exploit it to intercept and change caucus results as they were being submitted through the app.”
Not implementing HTTPS in a mobile app – regardless of whether it is used for election-related functions – would be regarded as an egregious, amateur mistake. But it remains unclear what might be wrong with the app.