Blockchain & Cryptocurrency , Cybercrime , Fraud Management & Cybercrime
Police Arrest €10 Million IOTA Cryptocurrency Theft Suspect
Scheme Offered 'Free' Website for Generating Cryptocurrency Wallet Seeds
Police in England have arrested a 36-year-old man as part of an investigation into the theft of at least €10 million ($11.3 million) in IOTA cryptocurrency since January 2018 from 85 victims worldwide, perpetrated via a malicious cryptocurrency seed generation website that stored users' private keys.
See Also: OnDemand | API Protection – The Strategy of Protecting Your APIs
The suspect, who has not been named, was arrested on Wednesday in Oxford on suspicion of fraud, theft and money laundering. Police say they seized a number of computers and other electronic devices, as well as drugs and cash, from the suspect's residence. Police conducted a number of digital forensic examinations of seized devices at the residence.
The operation was led by England's South East Regional Organized Crime Unit - known as SEROCU - and included support from officers from the State Criminal Police of Hesse, in Germany; the U.K.'s National Crime Agency; as well as the EU's law enforcement intelligence agency, Europol.
SEROCU says the U.K.-based suspect was first identified by the State Criminal Police of Hesse in July 2018, before being referred to Europol's Joint Cybercrime Action Taskforce, or J-CAT, in The Hague, Netherlands, which coordinated the different EU member states involved.
"This has been an intricate investigation into the theft of huge sums of money from victims across the world, and we have been grateful for the support of our European colleagues," says Detective Inspector Rob Bryant, from SEROCU's cyber and digital forensics unit. "The offenses have taken place over an extended period, and it's likely that there are other victims out there. We would urge them to contact their local police force to report the matter."

"The investigation was only successful because of the exceptional and sophisticated collaboration of international authorities, companies and IOTA community members," says Police Inspector Matthias Krekeler, from the State Criminal Police of Hesse's cybercrime investigations unit.
Video of police in England executing their search warrant released by SEROCU shows the suspect - his face obscured - wearing a "CampZone 2017" T-shirt. CampZone is a large, annual gaming event held in the Netherlands.

The suspect faces extradition to Germany, ZDNet reports. Europol and SEROCU didn't immediately respond to a request for comment.
But SEROCU tells Information Security Media Group: "The man was interviewed at an Oxfordshire police station after his arrest yesterday morning (23/1) and has since been released on bail."
Theft of IOTA Private Seeds
IOTA is backed by the IOTA Foundation, a non-profit organization founded in Germany in 2017 by Dominik Schiener and David Sønstebø to serve as an open source, distributed ledger - aka blockchain - for the internet of things, by providing micro-transactions without a fee and verifying the integrity of data being handled by devices.
Schiener says via Twitter that IOTA has been working with authorities in Germany, Japan and the U.K. as part of their investigation into the IOTA theft.

As of Thursday, the value of an IOTA coin was $0.29, and the cryptocurrency had a market capitalization of $817 billion, equivalent to 227,700 bitcoins.
'Free' IOTA Seed Generator
Press reports from early in 2018 traced the IOTA theft to an unknown suspect using the name "Norbertvdberg" who in August 2017 created a supposedly secure seed generator - at "iotaseed.io" - that IOTA users could employ to create an 81-character password, or seed, for securing their IOTA wallet. The seed generator was also available as a download via code-sharing site GitHub, which the developer said could be used to verify that the service was legitimate.
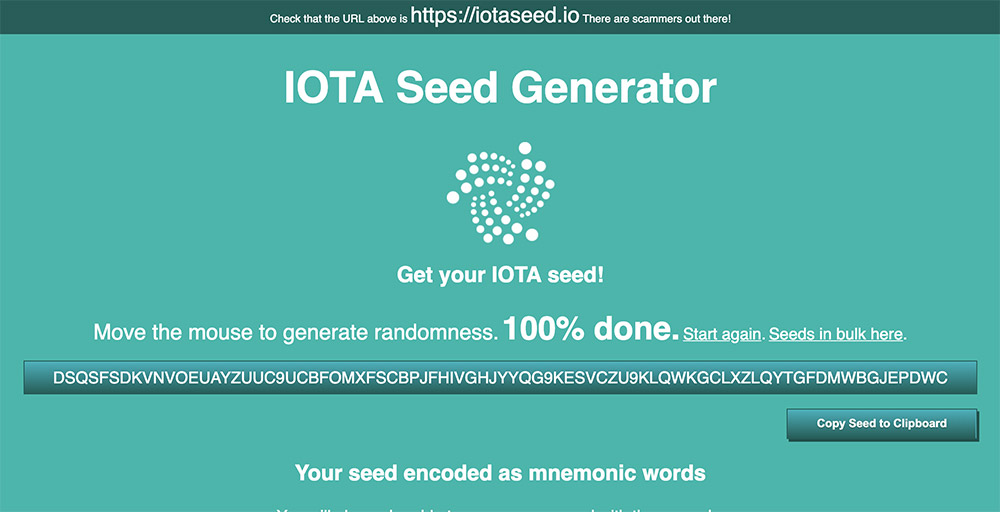
"This service is provided for free (to give back to the IOTA ecosystem) and as is, and is not related to IOTA," the iotaseed.io website read. "Donations are welcome!"
Norbertvdberg also maintained a presence on Quora and Reddit before disappearing after the heist and leaving the iotaseed.io website reading simply: "Taken down. Apologies."
But in reality, Norbertvdberg was allegedly keeping copies of users' private seeds. He then used them to drain multiple users' accounts on Jan. 19, 2018, authorities say.
The theft was initially obscured by a distributed denial-of-service attack, as IOTA users later discovered.
In the end, at least $3.94m worth of IOTA was stolen. This was facilitated by a DDoS attack against all public nodes.
— nic carter (@nic__carter) January 21, 2018
"Several victims created the seed on this website in good faith; however, the seeds were stored in the background by the service provider," Europol says. "Later, the criminal used these to gain access to the victims' wallets and transferred their money to other wallets created with fake IDs."
'Paranoia Can Be a Good Thing'
An analysis of the code running the iotaseed.io website, as well as the code contained in the iotaseed GitHub repository, discovered that the website code included a back door.
"This was a very cleverly hidden backdoor and was clearly done with malicious intent, rather than some sort of mistake in how the cryptography was implemented," according to a code analysis published in January 2018 by U.S. high school student Alex Studer. "Many steps were taken to hide the backdoor's existence, and a quick glance at the developer tools in your web browser would not have shown anything suspicious."
But Studer said that after digging into the code, he verified that it was, indeed, a clever ruse, via which the site creator stored copies of users' private seeds.
"In general, this incident should be taken as a reminder that, when it comes to cryptocurrencies (especially when dealing with large amounts of money!), paranoia can be a good thing," Studer said. "You should never rely on online services, like seed generators or web wallets, for holding any amount of currency you care about, and you should make sure that you use software that is open source and has been carefully reviewed and audited by the community."



















