Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management
Passwordless MongoDB Database Exposes 275 Million Records
Practitioners Warn Against More Unprotected Servers on MongoDB
Security practitioners are warning enterprises using MongoDB to ensure proper authentication mechanisms are in place after a researcher discovered a MongoDB database containing information on 275 million Indians was exposed on the internet for at least two weeks and then it was apparently taken over by hackers.
See Also: The Alarming Data Security Vulnerabilities Within Many Enterprises
It's not yet clear who owned the MongoDB database, which included names, dates of birth, gender, mobile number, email, educational qualifications, area of specialization, employment history, salary and functional area in the job, according to Bleeping Computer.
"There are a host of servers using MongoDB which are still unprotected," warns Dinesh O. Bareja, COO at Open Security Alliance.
The most common reason for a MongoDB hack is a lack of authentication because by default, it has no password mechanism in place, says Sachin Raste, security researcher at eScan, an anti-virus firm. "The root cause has been the lack of security in MongoDB, which allows anyone to access it remotely," he says. "Organizations using it need to add layers of authentication to make data secure."
Hackers Take Over Control
The exposed database was discovered May 1 by security researcher Bob Diachenko, according to BleepingComputer. When he could not determine the owner of the data, he alerted the Computer Emergency Response Team in India, or CERT-In, but the database remained unprotected for another week, the report in Bleeping Computer states.
A hacker group known as Unistellar apparently has taken control of the database and is demanding a ransom to return control to the owner, the report says.
"Taking over this database was only possible thanks to the lack of any authentication steps, which allowed the hackers to install ransomware on the MongoDB servers," Raste says. "Anyone could act as the administrator, which Unistellar did."
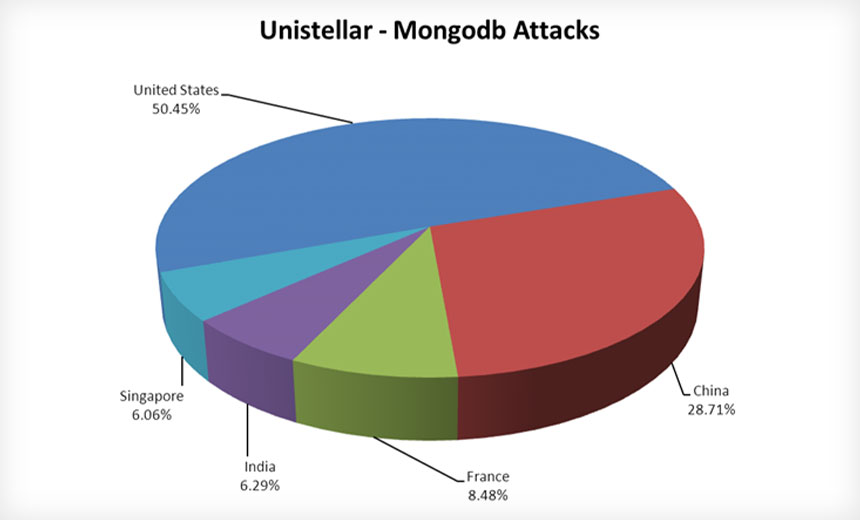
The below graph shows the percentage of Unistellar hacking group attacks targeting various countries.
CERT-In and MongDB did not immediately reply to a request for comment.
This is not the first instance of such attack on MongoDB. Last year, for example, Verifications.io, a data email verification platform, suffered a data breach that exposed 763 million records thanks to non-password protected MongoDB.
High Demand
The MongoDB database program is in widespread use worldwide.
In India, Aadhaar which captures biometric data of over 1.2 billion residents, has used MongoDB as one of its database programs, says Raste.
And Shutterfly, a popular internet-based photo sharing and personal publishing company that manages more than 6 billion images, has recently made a transition from Oracle to MongoDB, says a report on MongoDB's site.
"Organizations use MongoDB as it provides high performance, high availability and automatic scaling," Raste says. "Being non-structured, whenever a new field needs to be added to a document, then it can be created without affecting all other documents in the collection without the need to take the system offline ... or update the central system catalogue."
Mitigation Steps
Raste advises organizations using MongoDB to take several security steps, including:
- Enable access control and enforce authentication;
- Configure role-based access control;
- Encrypt communications;
- Encrypt data at rest;
- Limit network exposure.


















