3rd Party Risk Management , Access Management , Application Security
Okta Breach Timeline, Attack Method Analyzed
Researcher Shares Alleged Mandiant Security Report; Sitel Refutes Some Claims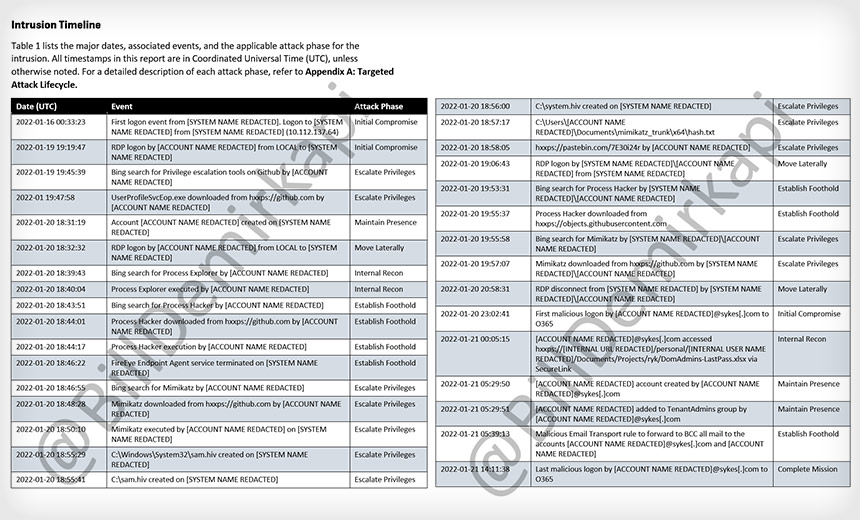
Days after the recent Lapsus$ hacking of Okta came to light, a report, allegedly produced by cybersecurity firm Mandiant, detailed the breach timeline and offered a step-by-step account of how the threat group gained access to the identity management company's environment.
See Also: The State of Organizations' Security Posture as of Q1 2018
The document shows that the attackers used simple methods to access and navigate Sitel's systems - and didn't try to hide their activities either.
Former Zoom offensive security researcher Bill Demirkapi (@BillDemirkapi) says in a series of tweets, "I have obtained copies of the Mandiant report detailing the embarrassing Sitel/Sykes breach timeline and the methodology of the Lapsus$ group."
David Bradbury, chief security officer at Okta, said earlier that Lapsus$ had compromised a laptop belonging to Sitel, a third-party customer support firm, via remote desktop protocol, enabling it to infiltrate Okta's network.
Bradbury said at the time that the attacker did not compromise Okta services via account takeover and only obtained "screenshots and could control the machine through the RDP session." The support engineer, he added, did not have "godlike" access and their access was "limited to basic duties in handling inbound support queries."
The Investigation
Mandiant, which was reportedly hired by Sitel to investigate the incident, declined Information Security Media Group's request for additional details and did not confirm the veracity of the document tweeted by Demirkapi.
Screenshots shared by Demirkapi show that Lapsus$ initially compromised Sitel on Jan. 16 and escalated its privilege on Jan. 19.
"We can see how Lapsus$ originally began investigating their compromised host on Jan. 19, 2022. With little regard for OPSEC, Lapsus$ searched for a CVE-2021-34484 bypass on their compromised host and downloaded the prebuilt version from GitHub," Demirkapi says.
CVE-2021-34484 is a Windows user profile service elevation of privilege vulnerability that is "not bound to the network stack and the attacker's path is via read/write/execute capabilities," according to Microsoft. Microsoft says an attacker can exploit the vulnerability by accessing the target system locally or remotely, relying on user interaction by another person to perform actions required to exploit the vulnerability. The company says it has issued an official fix to address the vulnerability.
After moving laterally in the network, Lapsus$ used "off-the-shelf tooling from GitHub for a majority of their attacks" and "bypassed the FireEye endpoint agent by simply terminating it," Demirkapi says.
Interestingly, the attackers performed a Bing search at this point and downloaded Mimikatz - an open-source pentest tool that allows users to view and save authentication credentials, the screenshots show.
What's the first thing advanced threat groups do after the first successful login on a target system with low privileges?
— Florian Roth ⚡️ (@cyb3rops) March 29, 2022
Correct, they use the local browser to run a Bing search for privilege escalation tools on Github. https://t.co/3dXRQvVmFR pic.twitter.com/OQCrgPsoX0
Demirkapi adds that Lapsus$ created a backdoor in Sitel's environment "after retrieving an Excel document conspicuously titled DomAdmins-LastPass.xlsx," and then proceeded to "forward all mail within Sitel's environment to their own accounts."
A statement Sitel shared with ISMG details its breach response steps and refutes some of the attack analysis by researchers and other media houses.
The Sitel Group said that on Jan. 20 it was "made aware of a security incident affecting a portion of the legacy Sykes network." The next day, it says, it issued "client-facing communications to notify customers who were possibly impacted by this incident" and hired an undisclosed cybersecurity vendor to investigate the attack.
"As of the initial identification of the incident, Sitel Group has maintained ongoing and regular communications with the customers who may have been impacted by this incident," the company says. There is "no longer a security risk regarding this incident," it adds.
Addressing some of the claimed reported inaccuracies, Sitel says that there have been false allegations that a spreadsheet, containing compromised passwords, was disclosed, and contributed to the security incident.
But the spreadsheet, it says, only listed account names from legacy Sykes and did not contain passwords. "The only reference to passwords in the spreadsheet was the date in which passwords were changed per listed account; no passwords were included in this spreadsheet. Such information is inaccurate and misleading and did not contribute to the incident," it says.
On Thursday, Okta responded to queries seeking confirmation on the veracity of the report shared by Demirkapi. "We are aware of the public disclosure of what appears to be a portion of a report Sitel prepared regarding its incident. This report is not specific to the services Sitel provides to Okta. Its content is consistent with the chronology we have disclosed regarding the January 2022 compromise at Sitel," Chris Hollis, senior manager of security and crisis communications at Okta, tells ISMG.
Infosec researcher Greg Linares, in a tweet, says: "#BlueTeams, if you see this open them up and replace the credentials with a honeypot network or login and change the pwd on the box and replace the pwd in the pain text file to "Come see the blue team for your new password."
Also commenting on the ease of preventing such attacks, James Meickle, principal infrastructure engineer at fintech incubator Fidelity Labs, says, "Timelines like this both show that even basic security practices work wonders, and that enterprise infosec culture actively hinders implementing them."
Researcher Sacked Over Tweets
Demirkapi, in a now-deleted tweet, said he was fired by video conferencing services provider Zoom, where he worked as a security researcher, for refusing to delete the tweets referring to the alleged security report from Mandiant.
I am officially looking for a new position! For those that aren't familiar with my work, my name is Bill Demirkapi and I'm a security researcher experienced with Windows internals/macOS security, reverse engineering, cloud security (mostly AWS), and vulnerability assessment.
— Bill Demirkapi (@BillDemirkapi) March 29, 2022
Demirkapi also clarifies that the published data was not bound by attorney-client privilege. "None of what I shared is from my organization and it was obtained entirely independently. I did not break any NDA/contract," he says.
Zoom did not respond to ISMG's request for comments.





















