NIST Updating Mobile Forensics Guidance
Significant Tech Changes Challenge Forensic Examiners
Apple unveiled the iPhone in June 2007, a month after the National Institute of Standards and Technology issued "Guidelines on Cell Phone Forensics." Seven years later, NIST is revising its guidance and giving it a new moniker, "Guidelines on Mobile Device Forensics".
See Also: Securing Your SWIFT Environment Using Micro-Segmentation: What Financial Institutions Need to Know
The latest version of the guide is known as the second draft of Special Publication 800-101 Revision 1. The final version of Revision 1 should be published later this year.
The revised guidance has two objectives, says Rick Ayers, who co-authored the 2007 and 2014 versions of the guidance: To help organizations develop appropriate policies and procedures for dealing with mobile devices and to prepare forensic specialists to conduct forensically sound examinations.
"The technology has changed so much within the past seven years; it was time to update the document to best meet the needs of mobile forensic examiners," Ayers says. "The older document, while technically correct, did not cover many of the more recent technologies in use today."
Ayers identifies the recent technologies to include micro SIM cards and flasher box extraction methods. Forensic experts use flasher box devices to recover user data from dead or faulty mobile phones.
Since 2007, changes have occurred in mobile device memory, identity modules and cellular network technology. In addition, mobile device tool classification systems, methods for handling obstructed devices and certain data preservation techniques didn't exist seven years ago.
Back then, about a dozen tools existed to help forensic experts recover and investigate data on cell phones. Today, the marketplace offers hundreds of tools, many designed for specific models of specific mobile devices.
No Know-It-Alls
"In the past, there were enough tools that you could hold them in your hands and say, 'I'm the master of all the mobile forensic tools,'" says guidance co-author Sam Brothers, a digital forensic specialists at U.S. Customs and Border Protection, part of the Department of Homeland Security. "We laugh at that now. But we've come to a point where that's virtually impossible. You have at least 100 different tools that are out there. For someone to try to know all of them would be very difficult."
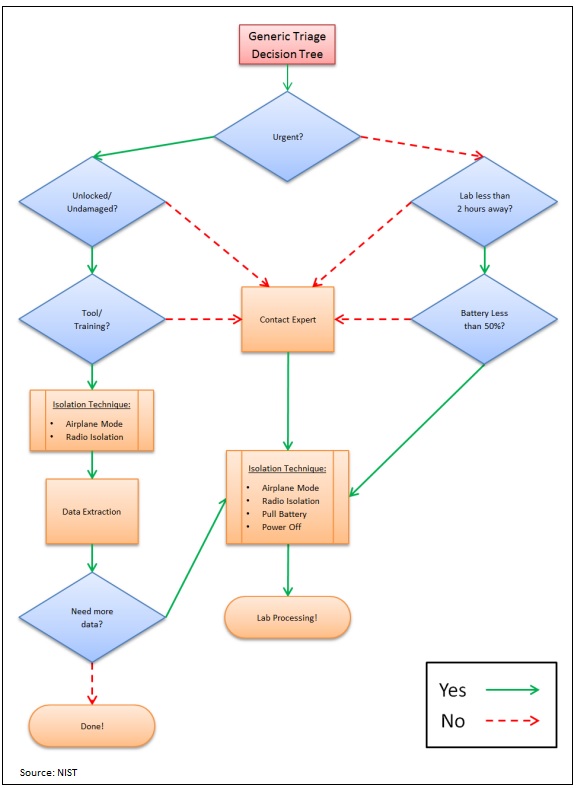
The revised guidance provides on-site triage processing, illustrated with a flow chart outlining common situations encountered by forensic examiners. "There are so many different kinds of phones that are being used to support so many different kinds of cases in so many different kinds of situations," says Barbara Guttman, NIST software quality group manager.
The new guidance also furnishes updated acquisition and preservation techniques for handling current mobile devices.
"The publication is not intended to be used as a step-by-step guide for executing a proper forensic investigation when dealing with mobile devices nor construed as legal advice," Ayers says. "Its purpose is to inform readers of the various technologies involved and potential ways to approach them from a forensic perspective."
The draft publication discusses procedures for the preservation, acquisition, examination, analysis and reporting of digital evidence. The publication also addresses the ever increasing backlogs for most digital forensics labs and provides guidance on handling on-site triage casework.


















