Account Takeover Fraud , Cybercrime , Cybercrime as-a-service
Mobile Malware Bypasses Banks' 2-Factor Authentication: Report
IBM Researchers Describe How 'TrickMo,' a TrickBot Variant, Works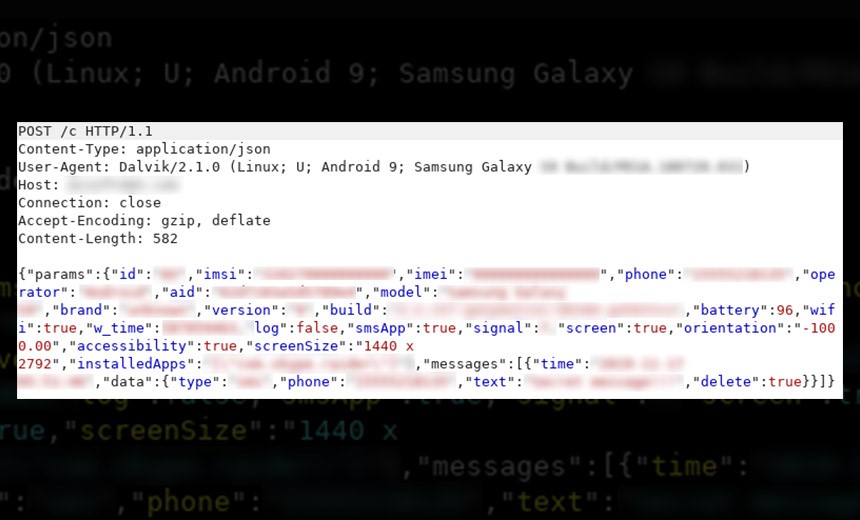
A variant of the TrickBot Trojan bypasses two-factor authentication for mobile banking, for example, by intercepting one-time codes sent over SMS, according to IBM X-Force.
See Also: OnDemand | Ransomware 3.0: We Thought It Was Bad and Then It Got Even Worse
So far, the malware has targeted banking customers in Germany, but the researchers say it’s likely to spread elsewhere and remains in active development.
The malware, which IBM X-Force researchers have dubbed "TrickMo," is disguised as a security app from a bank and is designed to be installed only on Android mobile devices. The fake app, once downloaded, infects the user's device and enables the attacker to take over.
Back to Bank Fraud
While TrickBot began life as a banking Trojan in the early 2010s, the malware has evolved into a cybercrime-as-a-service model that can be used for a variety of purposes, including delivering secondary attacks, such as ransomware. The IBM report, however, suggests that cybercriminals remain interested in using its for bank fraud.
"Germany is one of the first attack turfs TrickBot spread to when it first emerged in 2016," according to the IBM X-Force report. "In 2020, it appears that TrickBot's vast bank fraud is an ongoing project that helps the gang monetize compromised accounts."
How TrickMo Works
TrickMo was first spotted by the federal computer emergency response team of Germany, or CERT-Bund, in September 2019, the IBM X-Force report notes.
Aufgepasst beim #Online #Banking:#Emotet lädt #Trickbot nach. Auf infizierten PCs blendet Trickbot beim Online-Banking eine Abfrage nach der Mobiltelefonnummer und des Gerätetyps ein und fordert Nutzer anschließend zur Installation einer angeblichen Sicherheits-App auf. pic.twitter.com/QHfmYojZxK
— CERT-Bund (@certbund) September 20, 2019
TrickMo targets victims whose Windows PCs had previously been infected by TrickBot, which gathers data from a web browser, according to the report. This allows attackers to use the web injection feature of TrickBot to send fake messages spoofing a bank asking victims for their phone numbers and what type of mobile device they use and encouraging them to download a "security app" from the bank to their mobile device to protect their accounts, the IBM report notes.
Once the fake app is downloaded to an Android mobile device, the TrickMo malware is installed, according to the report. TrickMo can then steal personal device information, intercept SMS messages, record targeted applications for one-time passwords, lock down the phone, steal pictures and then self-destruct, IBM researchers explain.
The malware also attempts to access Android's accessibility services, which are designed to assist users with disabilities, the report notes. This enables TrickMo to gain near total control of the infected device, with the malware becoming the default SMS app.
In addition to capturing one-time passwords sent over SMS, the TrickMo malware can intercept newer authentication methods, such as transaction authentication numbers, which some German banks use for an additional layer of security beyond one-time passwords. To do this, the malware takes a screenshot of the number and sends that back to the attackers through a command-and-control server, according to the report.
Device Fingerprint
The IBM researchers note that TrickMo can collect enough data about an infected Android phone to reproduce its digital "fingerprint.”
This type of information can be sold on the dark web or used by fraudsters who are attempting to mimic legitimate transactions from a smartphone that has already been authenticated by the bank, according to the researchers.
"For example, since some banks use anti-fraud solutions that only check device fingerprinting, fraudsters can use the collected information to perform fraudulent transactions from a device that mimics that same fingerprint," the IBM report notes.
Due to its modular nature of TrickBot, its operators and those who rent it as a service, are able to vary the Trojan to meet their needs.
Earlier this month, the security firm Bitdefender discovered a new variant of TrickBot that uses remote desktop protocol brute-force methods to target potential victims and bypass security protocols (see: New TrickBot Variant Targets Telecoms in US, Asia: Report).






















