Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Incident & Breach Response
Microsoft Removes 50 Domains Tied to North Korean Hackers
Company Says Malicious Sites Used For Spear-Phishing and Malware Attacks
Microsoft has taken control of 50 domains that the company claims were used by a hacking group with ties to North Korean to launch spread-phishing campaigns targeting specific individuals and to spread malware.
In a federal lawsuit filed in the U.S. District Court for the Eastern District of Virginia, Microsoft claims that this threat group not only targeted the company's customers during these malicious campaigns, but also infringed on its trademarks, brands and products.
See Also: 2018 Banking Threat Landscape: An Inside Look at How Cybercriminals Target Financial Services
On Dec. 27, a federal judge ruled in favor of Microsoft. On Monday, the software giant announced that it seized controlled of the 50 domains in order to stop the phishing attacks from continuing.
The hacking group, which the company calls Thallium, primarily targeted victims in the U.S., Japan and South Korea with phishing emails and malicious webpages designed to like legitimate Microsoft accounts and products.
"By gathering information about the targeted individuals from social media, public personnel directories from organizations the individual is involved with and other public sources, Thallium is able to craft a personalized spear-phishing email in a way that gives the email credibility to the target," Tom Burt, Microsoft's corporate vice president for customer security and trust, writes in a blog post. "The content is designed to appear legitimate, but closer review shows that Thallium has spoofed the sender by combining the letters 'r' and 'n' to appear as the first letter 'm' in 'microsoft.com.'
This particular North Korean-linked threat group is also known as APT37 and Group 123, and has been linked by other security researchers to various campaigns that have targeted educational institutions, as well as chemical, electronic, manufacturing, aerospace, automotive and healthcare companies around the world.
Spoofing Domains
Before filing its federal lawsuit against Thallium hacking group, as well as several unnamed individuals associated with it, Microsoft's Digital Crimes Unit and the Microsoft Threat Intelligence Center has been tracking its activities and mapping an infrastructure composed of various websites, domains and connected devices, according to Monday's blog post.
As part of the hacking campaign it tracked, Microsoft researchers found that Thallium used spoofed Microsoft.com domains to send spear-phishing emails to specific targets. These messages, which appeared legitimate, requested a password update from the targeted victim, according to the blog post.
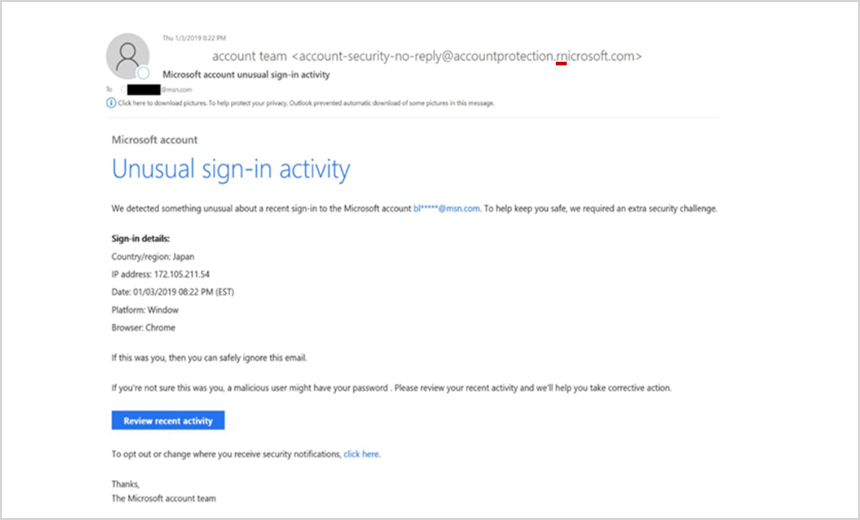
These phishing emails typically contained a link that, if clicked, would redirect the targeted victim to one of the malicious domains controlled by the hacking group. These webpages would then request the person's credentials, according to the blog post.
If the victim entered his or her credentials, the hackers would then have access to the person's email account, contact lists, calendar appointments and other personal data, according to the Microsoft. The attackers also ensured that they would maintain control of the accounts even if the passwords were changed again.
"Thallium often also creates a new mail forwarding rule in the victim’s account settings," Burt says. "This mail forwarding rule will forward all new emails received by the victim to Thallium-controlled accounts. By using forwarding rules, Thallium can continue to see email received by the victim, even after the victim’s account password is updated."
In addition to harvesting credential information, the attackers would also deploy malware, including two remote access Trojans called BabyShark and KimJongRAT, the company notes. In February, researchers with Palo Alto Network's Unit 42, published a detailed analysis of the BabyShark malware to describe how it exfiltrates data from infected systems and transfers the information to a command-and-control server. That report also detailed similarities between BabyShark and KimJongRAT.
In the various campaigns that Microsoft tracked, the company notes that the Thallium hackers primarily targeted government employees, think tanks and university staffers who focused on human rights and nuclear proliferation issues.
Using the Courts
Over the past several years, Microsoft has increasingly turned to federal courts to help it push back against hacking groups that infringe on the company's trademarks and product names to create phishing emails or spoofed websites that appear legitimate.
In March, for instance, Microsoft used its legal muscle to push back against the Iranian-linked group called Phosphorus to take control of 99 website domains by the attackers as part of a spear-phishing campaign (see:Microsoft Takes Control of 99 Websites From APT Group).
In 2017, the software giant used a similar legal strategy to seize domains operated by a Russian-linked group called Strontium, which is better known as APT 28 or Fancy Bear (see:Microsoft Battles Fancy Bear Hackers - With Lawyers).




















