Cybercrime , Endpoint Security , Fraud Management & Cybercrime
Huge Malware Distribution Network Crippled
'EITest' Shuffled as Many as 2 Million Users a Day to Malware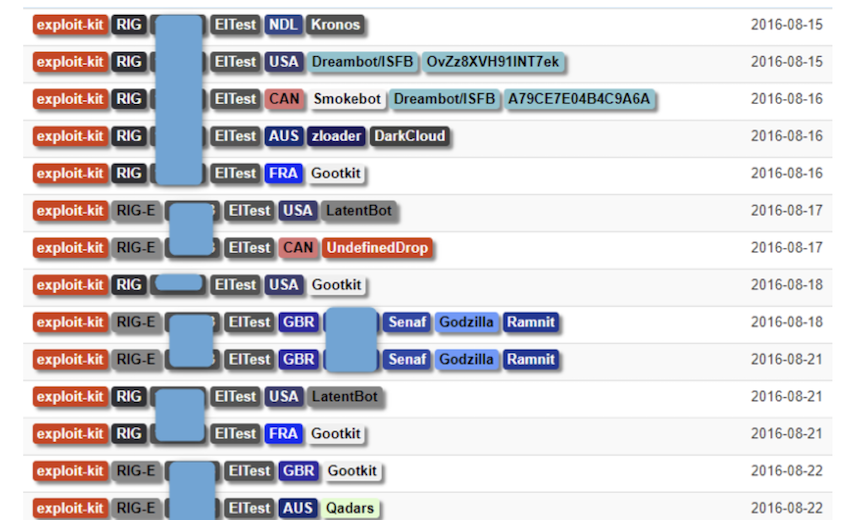
Security researchers are claiming at least a temporary victory over an enormously productive malware distribution scheme that shuffled as many as 2 million users a day from legitimate websites to malware.
See Also: An Assume-Breach Mindset: 4 Steps to Protect What Attackers are After
The networked, dubbed EITest, leveraged compromised websites to direct users to ransomware, tech support schemes and exploit kits. EITest, noticed as far back as 2011, had been dubbed the "king of traffic distribution."
Malware researcher Kafeine, who works for Proofpoint, writes that users who encountered a website tampered with by EITest are now being redirected to a sinkhole set up by researchers. The sinkhole, which is a non-malicious domain, became active on March 15.
"We are now receiving the traffic from the backdoors on the compromised websites, freeing them from the EITest C&Cs and their visitors from the resulting malicious traffic and injects," he writes.
The sinkhole operation was launched by Proofpoint along with researchers from brillantit.com and abuse.ch, which tracks malware campaigns, Kafeine writes.
Sinkhole Data
The sinkhole has revealed the scale of EITest. In just under three weeks, the sinkhole notched 44 million requests from 52,000 compromised servers and websites.
"Decoding the requests, we were able to obtain a list of compromised domains as well as IP addresses and user agents of the users who had browsed to the compromised servers," Kafeine writes.
EITest relied on infecting legitimate websites with code that redirected users to a constantly changing list of domains leading to booby trapped servers. Of the 52,000 sites observed since the sinkhole was set up, most appeared to be running the content management system WordPress.
Exploiting vulnerabilities in content management systems is easy, low-hanging fruit for attackers. Over the years, researchers had noticed EITest embedded itself into sites running WordPress, Joomla, Drupal and PrestaShop.
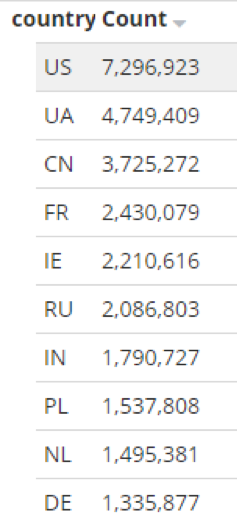
The top affected countries by number of infected legitimate websites ar the U.S., Ukraine, China, France, Ireland, Russia and India. The sinkhole will stop 2 million redirects per day to malicious destinations.
In January, brillantit.com wrote that EITest carefully chose its victims. The harmful code is only injected into a legitimate web page after the victim's user agent, HTTP referrer, HTTP host and IP address is checked. This is an often-used evasion technique that's used to avoid scrutiny by security researchers.
Large Traffic Distribution
When EITest was detected in 2011, it appeared to be a fairly closely held operation. It redirected victims to an exploit kit called Glazunov, which was kept private and not rented to other cybercriminals.
It also directed victims to Angler, a now defunct but highly potent exploit kit. Exploit kits bundle multiple exploits for software vulnerabilities in hopes that a computer encountering the kits will be can be infected using one (see Did Russia Knock Out a Critical Cybercrime Tool?).
Around 2014, EITest broadened it scope and became more of a traffic distribution network, Kafeine writes. It used its network of compromised websites to deliver traffic to purveyors of ransomware, tech support schemes and other malware.
That year, Kafeine writes, whomever was behind EITest sold traffic in blocks of 50,000 to 70,000 visitors for $20 per thousand.
Cleanup Underway
Since the sinkhole took effect, Kafeine writes that those behind EITest haven't drastically reacted aside from shutting down their command-and-control proxy servers.
But researchers suspect those controlling EITest may try to wrest control back of the infected websites.
"Although we witnessed some encoded calls to the sinkhole that embedded commands we would associate with takeover attempts, we cannot verify whether they were initiated by the operator or other researchers or threat actors attempting to interact with the real EITest C&C," Kafeine writes. As far as the infected legitimate websites, "we are sharing the complete list of compromised websites with national CERTs, and cleanup efforts are ongoing," he adds.
Prior efforts to hamper EITest have been mixed. In March, Kafeine published an anonymous post on his personal blog by someone who had made an effort to stop EITest from redirecting users to tech support scams.
Two flaws EITest allowed researchers to redirect traffic destined to tech support scams for about 14 hours, according to the post.






















