Fraud Management & Cybercrime , Malware as-a-Service , Ransomware
How Ekans Ransomware Targets Industrial Control Systems
Researchers Identified Malware Variants With Advanced Capabilities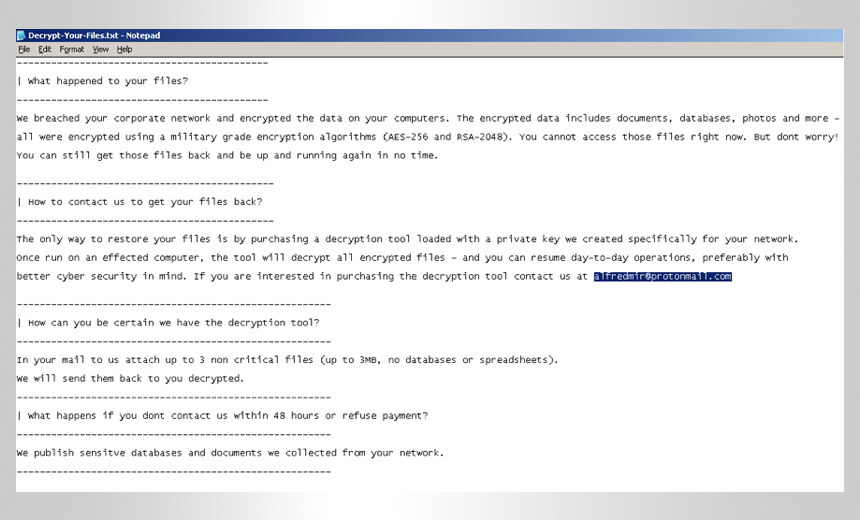
Researchers with FortiGuard Labs have uncovered two samples of the Ekans ransomware strain that offer some additional insight into how the crypto-locking malware targets industrial control systems, according to a new report.
Ekans, which is also referred to as Snake by some researchers, was first identified in February, and early reports indicated that it had been designed to target industrial control systems used in large-scale manufacturing facilities (see: New Ransomware Targets Industrial Controls: Report).
Now, FortiGuard researchers Ben Hunter and Fred Gutierrez have uncovered two variants of Ekans that offer some additional insights into how the ransomware strain was developed and how it targets industrial control systems. The first sample was spotted in May, and the second appeared in June.
In both cases, it appears that the ransomware was designed to take advantage of Windows-based systems, according to FortiGuard Labs, which is the research arm of security firm Fortinet.
"Both of these variants perform all of the typical ransomware activities you would expect, such as encrypting files and leaving a ransom note telling the victim to contact them at a specified email address, to receive instructions on how to pay a ransom and decrypt their files," Hunter and Gutierrez write in their analysis. "But they also perform actions that are not so typical."
These more unusual activities include confirming targets based on a domain analysis of targeted organizations, as well as isolating the infected networks once the attack starts, the researchers note.
Malware Capabilities
In their report, Hunter and Gutierrez note that both samples of Ekans that they uncovered were written in the Go - a programing language that is gaining in popularity with malware developers because they can use it to easily compile malicious code that works across multiple operating systems.
While the May version of the Ekans ransomware displayed a number of coding errors, the researchers note that the June sample showed significant improvement as well as additional capabilities such as the ability to turn off a firewall, the researchers note.
"Another interesting addition was to turn on the firewall before encrypting, probably to detect [anti-virus] and other defense solutions by blocking any communication from the agent," Hunter and Gutierrez note.
Ransomware Operation
The Ekans ransomware begins the attack by attempting to confirm its target. This is achieved by resolving the domain of the targeted organization and comparing this resolved domain to a specific list of IP addresses that have been preprogrammed, the researchers note. If the domain doesn't match the IP list, the ransomware aborts the attack.
"If the domain/IP is not available, the routine exits," the researchers add.
If the ransomware does find a match between the targeted domain and the list of approved IP addresses, Ekans then infects the domain controller on the network and runs commands to isolate the infected system by disabling the firewall, according to the report. The malware then identifies and kills running processes and deletes the shadow copies of files, which makes recovering them more difficult, Hunter and Gutierrez note.
In the file stage of the attack, the malware uses RSA-based encryption to lock the target organization's data and files. It also displays a ransom note demanding an undisclosed amount in exchange for decrypting the files. If the victim fails to respond within first 48 hours, the attackers then threaten to publish their data, according to the Ekans ransom recovered by the FortiGuard researchers.
Initial Access
In addition to analyzing the Ekans ransomware, FortiGuard found that the operators of the malware have several techniques to start the attack.
The main delivery method is through spear-phishing emails, but the attackers have also taken advantage of unsecure or vulnerable Remote Desktop Protocol sessions to gain footholds within a network. After that, the malware can move laterally through the network before finding its final target, the report notes.
Targeting ICS?
While some research suggests that Ekans or Snake was designed to target industrial control systems, not everyone is convinced. Brett Callow, a threat analysts with security firm Emsisoft, believes that Ekans targets as many systems as possible and not just ICS.
"In addition to the usual set of processes, Snake and some versions of Megacortex also attempt to end processes associated with ICS to free-up even more files for encryption," Callow tells Information Security Media Group. "So, it's not really designed to attack ICS as such; it’s simply designed to encrypt as much data as possible. If an actor actually wanted to attack ICS, there’d be far more effective ways to do it than the very rudimentary approach taken by Snake. In other words, Snake isn't Stuxnet II; it's vanilla ransomware."
Ekans Attacks
Security researchers suspect that Ekans has been used against several large-scale organizations.
In June, researchers with security firm Malwarebytes and others suspected that the Ekans ransomware was used against Japanese auto giant Honda. This attack affected production operations at several of its global facilities, including plants in the U.S., Japan, Turkey and Italy (see: Honda Confirms Hack Attack Disrupted Global Production).
In May, some researchers suspected that Ekans targeted the networks of Fesnius, Europe's largest private hospital operator and a major provider of dialysis products and services (see: Ransomware Slams Healthcare, Logistics, Energy Firms).






















