Breach Notification , Business Continuity Management / Disaster Recovery , Cybercrime
Hive Threat Group Attacks MediaMarktSaturn, Demands Ransom
German Store Chain Operations in at Least 3 Countries Reported Hit
MediaMarktSaturn Retail Group, a German multinational chain of stores, has confirmed to Information Security Media Group that it has suffered a ransomware attack.
See Also: Modernizing Malware Security with Cloud Sandboxing in the Public Sector
The attackers are demanding $50 million, according to a Tuesday report from Dutch media outlet RTL Nieuws, which is a huge drop from the $240 million ransom reported by news platform Bleeping Computer on Sunday. Bleeping Computer also attributed the attack to the Hive group.
A spokesperson for the company told ISMG: "The MediaMarktSaturn Retail Group and its national organizations became the target of a cyberattack. The company immediately informed the relevant authorities and is working at full speed to identify the affected systems and repair any damage caused as quickly as possible. In the stationary stores, there may currently be limited access to some services."
Store operations were affected in the Netherlands, Belgium and Germany, according to RTL Nieuws. MediaMarktSaturn has more than 850 stores spread across 13 European countries.
"MediaMarktSaturn continues to be available to its customers via all sales channels and is working intensively to ensure that all services will be available again without restriction as soon as possible," the spokesperson told ISMG.
All employees have been advised to disconnect network cables from cash registers and not restart systems until further notice, RTL Nieuws reports.
ISMG observed a tweet by @HozanMurad, who claims to be a political activist, suggesting that MediaMarktSaturn hinted to its employees that the company had been the victim of a ransomware attack.
#MediaMarkt / #Saturn gerade scheinbar in ganz DE und NL von #Ransomware betroffen.
— Hozan Murad ☀️ (@HozanMurad) November 8, 2021
Alle Kassen still, nichts läuft, sieht nicht gut aus pic.twitter.com/OR4stCaTT6
A screenshot in the tweet allegedly shows a letter sent by MediaMarktSaturn to its employees, which translates as: "All data on the server were encrypted by a Trojan (problem exists nationwide). Please do not try to restore data yourself (e.g. by renaming), this will only make things worse and with a bit of bad luck, the data will be permanently gone. As I said, [our team] is working on it."
Bleeping Computer shared what appears to be a ransom note from the attackers.
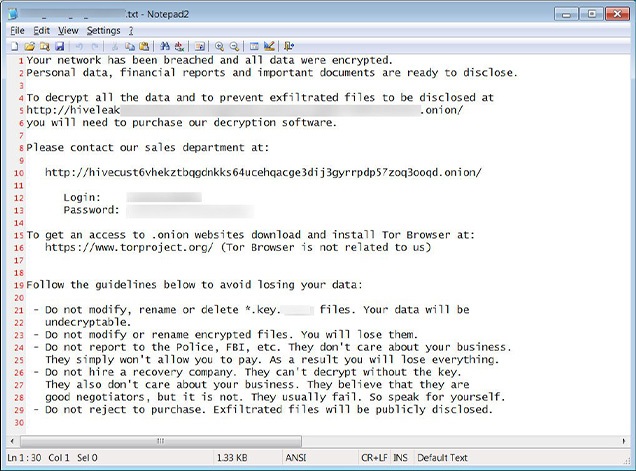
Hive Ransomware Attack
The company's systems and servers have been pulled offline, MediaMarktSaturn sources told RTL Nieuws. The move is in line with both the FBI and CISA's ransomware recommendations. According to Bleeping Computer, the attack on MediaMarktSaturn systems began on Sunday evening and continued until the early hours of Monday.
Hive has taken thousands of MediaMarktSaturn computers and servers hostage, RTL Nieuws reports. Bleeping Computer, citing the company's communication with employees, puts the number at nearly 3,100.
The FBI has recently warned that Hive goes after backup copies or snapshots of its victims' data in order to drag them to the negotiation table (see: FBI Issues Alert on Hive Ransomware).
It is unclear whether the company's backups have been encrypted.
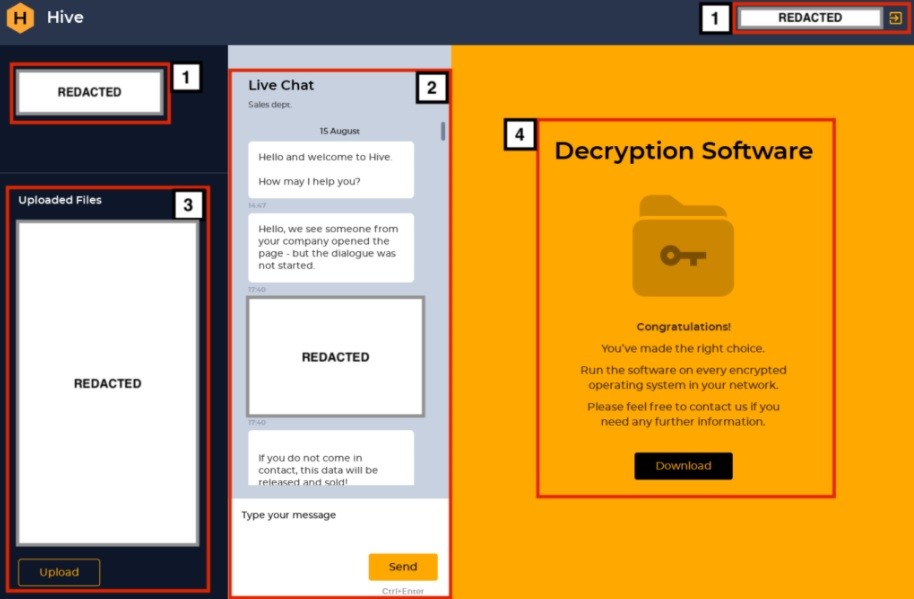
All of Hive's communications, including negotiations, are conducted by its operators through a well-established help desk on the group's website. Victims are given credentials in the ransom note to access the portal, cybersecurity firm Netskope says.
Once authenticated, a victim can see their organization's name and get access to a live chat to interact and negotiate with the threat actors and file upload capability to send encrypted files to the attackers. The threat actors decrypt the sent file to prove their decryption software capabilities. After the ransom is paid, the threat actor sends the victims a link to its decryption software, the Netskope blog says.
Interest in Healthcare
The Hive ransomware group, which emerged in June 2021, has targeted the healthcare sector before. In August 2021, the group conducted cyberattacks on one healthcare entity in Ohio and another in Nevada (see: Healthcare Organizations Mopping Up After Cyberattacks).
"Several characteristics of the Hive ransomware group make the threat actor particularly menacing to victims, which include healthcare sector targets," says Adam Meyers, vice president of intelligence at security firm CrowdStrike. "A lot of the ransomware actors focus on one particular platform, like Windows," he notes. "Hive is a group that has [ransomware] for multiple platforms - Windows, Linux, and also EXSi hypervisors, which is another tactic that's relatively new,” he says (see: Why Hive Attacks Are the Latest Menace to Healthcare Sector).




















