Heartbleed Update: Fixes Plateau
Two Months Later: OpenSSL Vulnerability Widely Patched
Two months after the OpenSSL flaw known as Heartbleed was discovered, related remediation efforts have slowed. But several information security experts have lauded businesses' rapid response to the threat, noting that they've installed related fixes - which are still being released - much more quickly than usual.
Lately, however, the pace of Heartbleed-related patching has decreased, according to Robert David Graham, CEO of Atlanta-based Errata Security. "Two months after Heartbleed, 300k systems still vulnerable - unchanged from last month," he tweeted June 21, based on his scans of servers that are running a vulnerable version of OpenSSL, which is an open-source implementation of the SSL and TLS protocols that's used to secure data sent between clients and servers.
Graham first began Internet-wide scans of port 443 - on which the HTTPS service typically runs - when Heartbleed was discovered in early April. He found 600,000 vulnerable systems. One month later, however, he found just 300,000 vulnerable systems, meaning that half appeared to have been patched.
With his latest, third scan, no more vulnerable systems appear to have been patched. "Last night, now slightly over two months after Heartbleed, we scanned again, and found ... 309,197 still vulnerable," Graham said in a June 21 blog post.
Oddly, the number of SSL-supporting servers found by his scans declined from 28 million with the first scan to 21 million with the second, before returning to 28 million with the third. So, are his findings reliable? "Scans are really strange, affected by things like time of day, day of week, and so on," Graham tells Information Security Media Group. "That's why there's often variation from one scan to the next."
Excellent Patch Progress
Graham's findings suggest Heartbleed-related remediation efforts have slowed to a crawl. Regardless, Ivan Ristic, director of engineering at vulnerability management firm Qualys, lauds the current state of Heartbleed remediation efforts. "Heartbleed patching rates are excellent and better than the rates for any other SSL-related issue," he says. Indeed, according to June statistics from the SSL Pulse scan, just 0.7 percent of scanned servers had the Heartbleed flaw. "By comparison, we still see insecure renegotiation - a vulnerability from 2009 - at about 6.4 percent," Ristic says.
Those statistics differ from Graham's because they're based on scans of popular websites. "They are well maintained and have all the incentives to be patched," Ristic says. "Errata Security scans IP addresses across the entire IPv4 space, which means that they encounter all sorts of devices and endpoints, not just websites. Thus, differences are to be expected."
Product Warnings Plateau
The Heartbleed flaw doesn't just affect servers running vulnerable versions of OpenSSL, but any products that build in a vulnerable version of OpenSSL. As a result, when Heartbleed was discovered, it wasn't clear how many products were at risk.
More than two months later, however, "590 different products from 100 different vendors have so far been recorded by us as having been made vulnerable by the Heartbleed vulnerability," says Kasper Lindgaard, director of research and security at vulnerability management specialist Secunia in Copenhagen, Denmark. Furthermore, by June 11 - or 65 days after the first public Heartbleed alert was published - vendors appeared to have released the vast majority of Heartbleed-related vulnerability announcements.
"I believe we are close to the final count - if the vendors haven't identified vulnerable products by now, they probably won't," Lindgaard says.
Heartbleed Vulnerability Alerts
Total Number of Affected Vendors / Products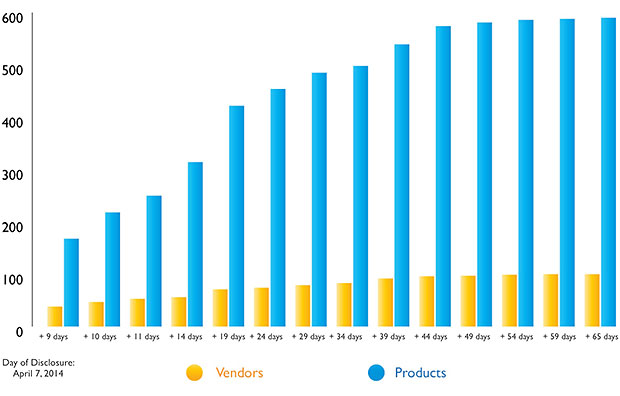
Source: Secunia
Not all of those vulnerability warnings, however, have yet been followed by vendors releasing a related fix, which means some businesses still can't patch all of their Heartbleed-related problems. "We are waiting for the remaining big vendors to publish the final patches," Lindgaard says. He also notes that some businesses, in their haste to patch Heartbleed, may have inadvertently upgraded from a version of OpenSSL that wasn't vulnerable, to a version that was vulnerable, and may not yet have "bothered to 're-patch.'"
Any business using a server or product that's running a Heartbleed-vulnerable version of OpenSSL should put a related fix in place as soon as possible because attackers could exploit the bug to steal data. "The remaining systems should be patched, but the reality is that there are many abandoned systems as well as small devices that are not monitored and never updated," Ristic says. "Thus, as with many other problems, Heartbleed will remain on a large number of systems for a long time."
Going forward, expect to see a continuing, gradual decline in systems with Heartbleed-related flaws. "We should see a slow decrease over the next decade as older systems are slowly replaced," says Errata Security's Graham. "Even a decade from now, though, I still expect to find thousands of systems, including critical ones, still vulnerable."
Open Source Changes
One upside to Heartbleed is that it's focused attention on the open source technology that powers much of today's Internet. "The Heartbleed case has opened up a very good debate on the need to identify and support 'critical Internet infrastructure,'" says Sean Sullivan, security advisor at Helsinki, Finland-based security software vendor F-Secure.
Notably, the discovery of the flaw led to the creation of the Core Infrastructure Initiative, through which major technology companies have pledged to collaboratively fund open-source projects that have a big impact on the state of information security. For starters, the initiative has promised to provide funding to improve OpenSSL.
In addition, two groups have announced efforts to take the existing OpenSSL code and create a new "fork." The OpenBSD community in April announced its own version of OpenSSL, called LibreSSL; and Google developer Adam Langley last week previewed BoringSSL, which he's billing as a more lightweight version of OpenSSL that's meant to complement that code base, as well as LibreSSL. Google also promised to share all BoringSSL code with the two other projects.
With luck, all of these community-driven open source projects and security initiatives will help prevent future Heartbleeds.




















