Breach Notification , Incident & Breach Response , Managed Detection & Response (MDR)
'Hacking Incident' Impacts Nearly 280,000 Medicaid Patients
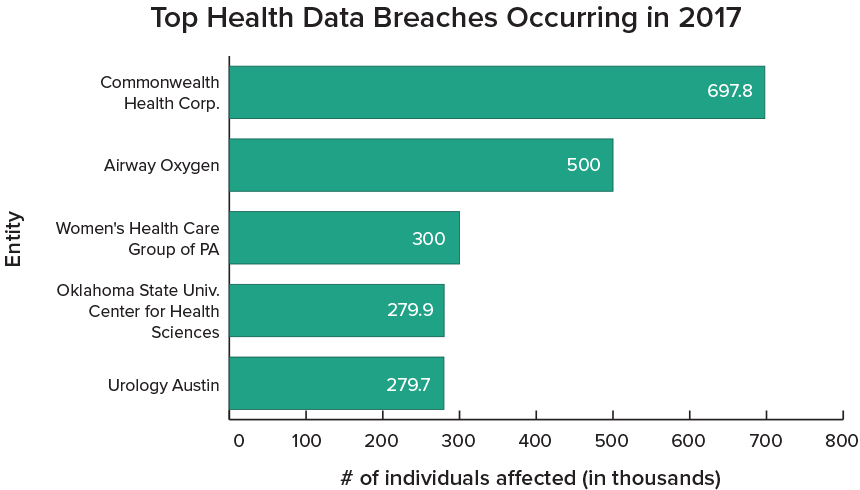
Oklahoma State University Center for Health Sciences Sends Notification Letters
A health data breach reported to federal regulators as a "hacking/IT incident" impacting nearly 280,000 Medicaid patients in Oklahoma has experts wondering exactly what happened.
See Also: Why Active Directory (AD) Protection Matters
The Oklahoma State University Center for Health Sciences reported the incident Jan. 5 to the U.S. Department of Health and Human Services as impacting a network server and affecting 279,865 individuals. A notification letter OSUCHS is sending to affected individuals notes that the incident was discovered nearly two months earlier.
"On Nov. 7, 2017, we learned an unauthorized third party had gained access to folders on the OSUCHS computer network," the notification letter says. "These folders stored Medicaid patient billing information. On Nov. 8th, we took immediate action to remove the folders from the computer network and terminated the third-party access. We also launched a thorough investigation, including hiring an independent data security firm. The firm assisted us in determining whether the folders had been compromised."
The OSUCHS incident is not only the largest breach reported that's been posted on the HHS HIPAA Breach Reporting Tool website - commonly called the "wall of shame" - so far this year but also ranks as the fourth largest breach occurring in 2017.
The HHS Office for Civil Rights, which enforces HIPAA, posts to the "wall of shame" reports of breaches impacting 500 or more individuals as the agency confirms details of the incident. Other breaches occurring in 2017 could also potentially be added to the tally in the coming months.
The breach follows the trend in 2017 - as well as in 2016 - of large hacking incidents dominating top breaches posted on the wall of shame.
Hacking was the cause of nine of the 10 top breaches in 2017 and about 70 percent of the total number of individuals affected by all health data breaches during the year (see 2017 Health Data Breach Tally: An Analysis).
Notification Letter
In its notification letter, OSUCHS says its investigation could not rule out that the third party accessed patient information. "The information in the folders may have included patients' names, Medicaid numbers, healthcare provider names, dates of service and limited treatment information," the letter states. "It is important to note these folders did not contain medical records. A single Social Security number was contained on the server."
OSUCHS's notification letter says the organization has "no conclusive indication of any inappropriate use of patient information" and did not mention whether it planned to offer free credit and identity theft monitoring to affected individuals.
OSUCHS did not immediately respond to an Information Security Media Group request for additional information about the breach.
Scant Details
While the OCUCHS notification letter also doesn't provide details about whether the organization has any clues about the identity of the "unauthorized third-party" who accessed the data - whether it was indeed an unknown hacker or a perhaps an unauthorized insider - such as an employee of contractor - the incident spotlights the array of risks and threats to protected health information.
"'Unauthorized third party' is a very vague identification," says Kate Borten, president of the privacy and security consulting firm The Marblehead Group. "This could be a total stranger on the internet, or this could be a known contractor or business associate who had been granted access to the OSUCHS network or a specific system, but was not authorized to access this Medicaid folder," she says.
"In some ways, the latter is far more serious since it suggests that internal access controls were not properly implemented. And insider threats are more dangerous since insiders may know where assets are stored and what weaknesses are in the systems.
David Finn, executive vice president of strategic innovation at security consulting firm CynergisTek, points out: "At this point any speculation about how an unauthorized third party gained access to these folders would be just that - speculation.
"What it does point to ... is that getting access to health information is still too easy, be it a malicious outsider or a well-intended insider. It also indicates that organizations that maintain PHI still don't understand their data - where it is, how it got there, where it came from, who is using it, what they are doing with it and where they are sending it."
The OSUCHS incident is the second major breach reported so far in 2018 involving Medicaid data. On Jan. 5, Florida's Agency for Health Care Administration, which regulates healthcare facilities and is responsible for administering Medicaid in that state, also reported a hacking incident to HHS. The Agency for Health Care Administration says in a statement that the incident, which affected 30,000, involved a phishing attack in November.
"The Medicaid data is PHI and access should have been tightly restricted," Borten says. While OSUCHS has not indicated whether the Medicaid data was encrypted, encryption would have thwarted the breach in some circumstances."
Important Lessons
While OSUCHS also has not divulged whether its incident - like the one in Florida - also involved phishing or some other type of cyberattack, experts say the breach provides important lessons.
Most organizations need to make security improvements in a number of areas, says Rebecca Herold, president of Simbus, a privacy and cloud security services firm, and CEO of The Privacy Professor consultancy.
That includes keeping operating systems and networks regularly patched and updated; conducting vulnerability and penetration testing; performing regular risk analyses; providing ongoing workforce training; implementing a BA information security oversight management program; and ensuring secure disposal practices.
"There are far too many issues that get overlooked. I've seen breaches occur as a result of many of these situations," she says.
Finn says the OSUCHS breach highlights once again "that data is not only the currency of healthcare in today's world; it is also the most important asset. This isn't about the investigation, the fines, breach notification or even buying credit monitoring for the victims. This has damaged healthcare at this institution. This is about patient care, the quality of that care and trust in the system."
A second lesson from the incident, he contends, is: "In this age of hyper-connectivity in healthcare, your security is only as good as the worst security at those places, agencies, organizations you share data with. The more connectivity you have - from simple file sharing to remote access to your resources - the more vulnerabilities you have. You must take steps to ensure everyone you connect with is secure themselves or your sharing is designed to protect yourself."






















