Access Management , Cybercrime , Fraud Management & Cybercrime
Why Hackers Abuse Active Directory
From Ransomware to APT Attacks, AD Can Make Connecting to Systems Easy
(Part one of a two-part series)
See Also: Federal Agencies Tech Brief: Security Investigation, Detection and Rapid Response
Warning: Attackers are abusing poorly secured and managed implementations of Microsoft Active Directory.
Security experts say that Active Directory, built into most Windows Server operating systems, has become the dominant approach to managing Windows domain networks. But its ease of use can also be tapped by hackers. (For more information, see part two of this two-part series.)
"Active Directory is the core identity platform for many businesses around the world," says Huy Kha, an information security professional at a Dutch law firm who's an expert on Active Directory security.
"It is used to connect different systems to each other. So that means that it has also become a prime target," he tells Information Security Media Group. "Why? Because if the attacker can get a foothold inside AD, he can leverage it to access all the systems that are connected on the network."
Norway's Computer Emergency Response Team, NorCERT, for example, said that the attack earlier this year against aluminum giant Norsk Hydro involved LockerGoga ransomware "combined with an attack on Active Directory" (see: Hydro Hit by LockerGoga Ransomware via Active Directory).
In April, researchers Oleg Kolesnikov and Harshvardhan Parashar at Securonix reported other attacks that infected organizations with LockerGoga also tapped Active Directory. "In some incidents, the actors have also been using Active Directory management services to distribute the payload in the network," they wrote, referencing additional research conducted by Nozomi Networks.
Other hackers also regularly target or leverage Active Directory. After gaining initial access to a network, the hacking group APT15 - aka K3chang, Mirage, Vixen Panda, GREF and Playful Dragon - uses a custom-developed tool that can bulk export AD data, NCC Group reports.
Cobalt Strike Beacon
The cybercrime gang known as Carbanak, meanwhile, has been wielding malware known as Cobalt Strike Beacon, says security firm Bitdefender, which conducted a digital forensic investigation at an Eastern European financial institution that was hit by the gang in 2018.
Bitdefender says the malware includes the ability to execute shell command on systems, record keystrokes, take screenshots, escalate privileges "and even deploying memory scraping tools, such as Mimikatz, or enumerating Active Directory hosts," all of which can help attackers to use the initial system as a springboard for accessing other networked systems
Bitdefender says "day zero" of the attack against the bank involved an employee being phished via a Microsoft Word document containing three exploits, delivering Cobalt Strike beacon to the system, which mapped the organization's internal network and collected admin-level credentials. The same day, "credentials for one domain administrator were compromised and used throughout the duration of the attack," which lasted 63 days, before attackers stopped after covering their tracks.
Internal Vulnerabilities at Large
Windows vulnerabilities - including in Active Directory - that can be abused by attackers are widespread.
In a new report titled "Under the Hoodie 2019," security firm Rapid7 rounds up what it's seen over the course of its employees conducting 180 penetration testing engagements over a nine-month period ending in May. Rapid7 says 40 percent of its engagements involved pen testers conducting “external compromise” tests to identify "weaknesses and exposures that are exposed to the general internet," while 36 percent of engagements were primarily focused on internal network assessments, "where the tester is mostly focused on things like Windows Active Directory domains, printers and IoT integrations, and other IT infrastructure not (normally) exposed to the internet."
By and large, firms have at least one vulnerability a pen tester can exploit, the survey shows. "Across all internal and external network and code audit engagements surveyed, 96 percent saw at least one vulnerability reported by the penetration tester," Rapid7 says. But some vulnerabilities are worse than others.
On a scale of 0/3 - How easy is it to obtain Domain Admin credentials in a pentest or red team?
— Huy (@HuyKh4) April 11, 2019
Of the vulnerabilities found during internal testing, for example, Rapid7 said 11 percent involved clear-text credentials being found in memory, which can potentially grant an attacker admin-level access to other systems. Meanwhile, 9 percent of all internal vulnerabilities involved Kerberoasting.
"Kerberoasting, a term coined by Tim Medin, is a privilege escalation technique which proves to be very effective in extracting service account credentials in a domain environment," Microsoft's Moti Bani says in a blog that includes steps for blocking these types of attacks.
"Many organizations are using service accounts with weak passwords that never expired, and usually these accounts enjoy excessive privileges - local administrator or domain administrator," he says, noting that auditors often overlook what AD service accounts can do.
In June, for example, the Department of Commerce Office of Inspector General warned that "inadequate management of Active Directory" was putting at risk the U.S. Patent and Trademark Office's mission.
"We found that inadequate configuration of Active Directory allowed excessive access permissions; user credentials were not securely stored in Active Directory; weak passwords were used; and a security best practice was not followed to enforce multi-factor authentication," the OIG reported.
X-Ray Exposure
Rapid7 pen tester Nick Powers writes in the company's report that for one recent engagement, he was looking for wireless and internal network vulnerabilities at a system of eight hospitals, and the wireless network appeared to be very well locked down.
But the internal network had many nonstandard devices, most of which were networked medical devices. "One of these medical devices, an unused X-ray machine, was running an outdated version of Windows," he says. "The old and forgotten X-ray machine had been previously accessed by a privileged Active Directory user with 'domain administrator' privileges, which allowed for the clear-text credentials of that user to be recovered from memory. That X-ray machine gave us the keys to the entire network."
Old Windows Systems Get Retired
But Tod Beardsley, director of research at Rapid7, tells ISMG that from a Windows security standpoint, things are getting better, thanks in part to older Windows systems being treated as "end of life" by organizations.
"According to the statistics we gathered in 2019 compared to past years, Windows administrators seem to be doing a better job at basic, nondefault secure configurations than they have in the past," he says.
Take SMB signing, which can sign communications at the packet level to verify the packets' point of origination and their authenticity.
Rapid7's penetration report saw SMB relay attack exposure - due to a lack of SMB signing - in only 15 percent of engagements, compared to 26 percent of the time in 2018. "The exposure of null sessions AD domain controllers is similarly down - 2019 was the first time we saw disabling null sessions cross the 50 percent mark, so it's slightly more likely than not that domain administrators are disabling null sessions on domain controllers, an often-recommended, nondefault secure configuration," he says. Ideally, however, there would be 100 percent SMB signing and zero null sessions.
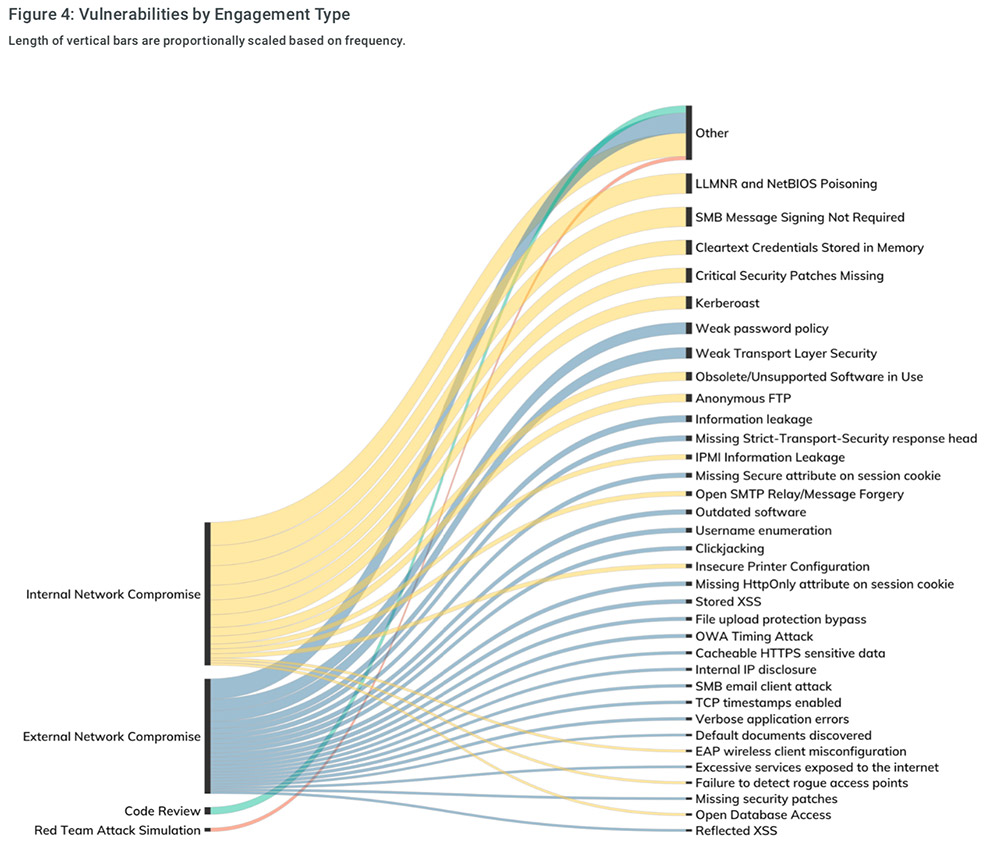
But the low exposure to Kerberoast is also a positive sign. "The Kerberoast stat tells me that there are fewer and fewer Active Directory domains configured to handle both current and legacy Windows endpoints, since Kerberoast relies on older, weaker encryption standards common on now-EOL versions of Windows," Beardsley says. "This is also a pleasant surprise - the population of old, unsupported Windows devices continues to fall in corporate internal networks. Perhaps one day, Windows XP will finally hit zero percent."
That has obvious upsides for not just IT security in general, but also Active Directory implementations. But experts say there are more specific defenses that organizations should be putting in place. To get the rundown, read part two of this two-part feature coming soon.























