Epsilon Breach: How to Respond
Banks, Merchants Reach Out to Quell Consumer Fears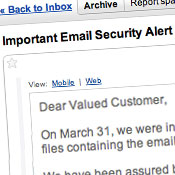
"There is nothing to offer customers directly in this case," Grossman says. "Financial institutions should be moving down the path of authenticating transactions, such as backend fraud monitoring, rather than authenticating the identity of a person. Financial institutions should assume the customer's computer or account is compromised and implement ways to continue business, anyway, under those circumstances."
Epsilon, an online marketing unit of Alliance Data Systems Corp., announced April 1 that an outside intrusion had hacked into some of its customer files. Epsilon sends e-mail campaigns and offers to consumers who register for a company's website or who give their e-mail addresses while shopping. Epsilon sends more than 40 billion e-mails annually and also runs loyalty programs for credit card users.
Letters to Customers
Best Buy and Chase, just two on a growing list of companies suspected of being impacted by the Epsilon e-mail breach, have both sent e-mails to customers, warning them about possible spear phishing attacks.In its letter, Best Buy writes: "We have been assured by Epsilon that the only information that may have been obtained was your e-mail address and that the accessed files did not include any other information."
The letter that went out to Chase customers had a similar ring: "We have a team at Epsilon investigating and we are confident that the information that was retrieved included some Chase customer e-mail addresses, but did not include any customer account or financial information."
Entanglement and Confusion
Nicolas Christin, associate director and a faculty member of the Information Networking Institute at Carnegie Mellon University, says the breach is a concern because of the massive number of e-mail addresses Epsilon possesses. "What struck me was the magnitude of the breach," he says. "This is a very, very large marketing company that has access to a number of e-mail addresses."Christin also notes that Epsilon's affiliation with other e-mail and marketing firms makes determining potential points of compromise difficult. Thus, confirming rumors that Epsilon might have been breached first in December may be difficult as well, he says, because of those entanglements.
"It is possible that today's breach is a direct byproduct of a breach that happened in December," Christin says. "It's also possible that the two breaches are unrelated. And the reason we are not sure is because these e-mail lists that are shared by different market affiliates are shared by various companies and various marketing entities, and it's not really clear where a leak can come from."
Insecurity of Third Parties?
Getting to the bottom of the breach would be beneficial not only for banks and retailers, but also consumers, Grossman says. "A lot of people would find it helpful if Epsilon made the technical details of how the breach occurred public," he says. "Without specifics, it is difficult to know what exactly happened, the extent of the breach, and if their actions will help make sure this doesn't happen again."That may be information even Epsilon does not know, given the entangled relationship it has with other e-marketers and e-mail list providers. Figuring out how the lists were leaked or breached may be as challenging as determining which link in the chain led to the compromise, says Julie McNelley, a security analyst at Aite Group. "As we've seen with the RSA attack, there are many ways they could have gotten in,"
"If someone like RSA can be breached, it can happen to anyone," she adds. "I think you have to look at how much you want in the cloud, outside your control."
Financial institutions, which have historically been wary of outsourcing anything that touches account information, have been quick to jump on the third-party bandwagon for e-mail marketing. "I think we're going to be seeing some ramifications from that decision," McNelley says. "A number of financial institutions do work with companies like Epsilon for e-marketing, and I think some might go back to the table to revisit that decision."