Active Defense & Deception , Cybercrime , Fraud Management & Cybercrime
Encrypted Communications Network 'Anom' Was Sting Operation
FBI Developed Smartphone-Based Platform as Honeypot for Criminals
For the past 18 months, thousands of criminals have been relying on an encrypted communications platform called "Anom" to coordinate their operations.
See Also: The Importance of Resolving All Alerts
But what criminals didn't know, and law enforcement officials revealed Tuesday, was that Anom had been developed by the FBI and was used as a honeypot by a global consortium of law enforcement agencies, who monitored every message written and image sent across the service.
In recent days, the information and intelligence gleaned from those communications was used in a large-scale series of police operations across 16 countries that led to more than 800 arrests and the seizure of more than 8 tons of cocaine, 22 tons of cannabis and cannabis resin, 2 tons of synthetic drugs, 6 tons of synthetic drugs precursors, 250 firearms, 55 luxury vehicles and over $48 million in various worldwide currencies and cryptocurrencies, says Europol, the EU's law enforcement agency.
The effort was led by Australian Federal Police and the FBI, as well as Dutch National Police and Swedish Police, backed by Europol and the U.S. Drug Enforcement Agency. The AFP and New Zealand police referred to the operation as Ironside, the FBI as Trojan Shield and Europol as its Greenlight operational task force.
Officials say criminals flocked to Anom after it was introduced in late 2018. The service ran on smartphones that were customized to only run the service's software.

"The goal of the new platform was to target global organized crime, drug trafficking, and money laundering organizations, regardless of where they operated, and offer an encrypted device with features sought by the organized crime networks, such as remote wipe and duress passwords, to persuade criminal networks to pivot to the device," Europol says in a news release.
Uptake appears to have been swift, with thousands of users sending 27 million messages over the past 18 months, said Jean-Philippe Lecouffe, Europol's deputy director of operations, at a Tuesday press conference at Europol's headquarters in The Hague, Netherlands. "The figures are impressive: more than 12,000 encrypted devices, used by more than 300 criminal syndicates, operating in more than 100 countries," he said.
Europol says the user base included "Italian organized crime, outlaw motorcycle gangs and international drug trafficking organizations," among many others.
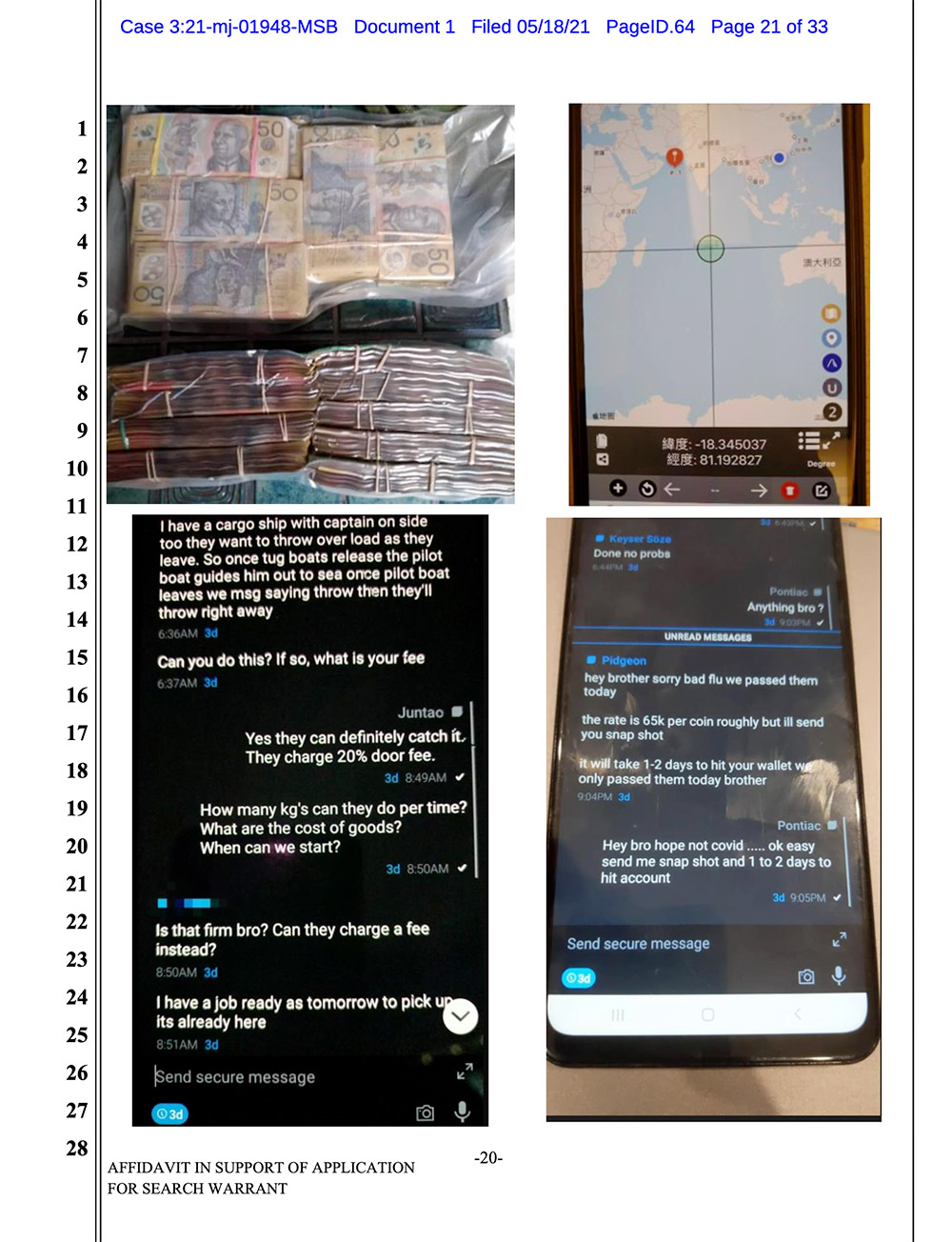
"To give you an idea of the magnitude of our penetration, we were able to actually see photographs of hundreds of tons of cocaine that were concealed in shipments of … canned goods," Calvin Shivers, assistant director of the FBI's Criminal Investigative Division, said at the press conference.
As Vice Media first reported, a search warrant obtained by the FBI and served to Google, seeking communications for multiple suspects, dated May 18 and unsealed Monday, notes that as part of the covert, ongoing investigation, "the FBI is targeting almost two dozen of the Anom platform’s administrators and distributors."
The search warrant, which says that multiple named individuals and unnamed co-conspirators are suspected of engaging "in international maritime narcotics smuggling," notes that the wider investigation was set to conclude Monday and be publicly announced Tuesday, as has happened. "Until then, the continued success of the investigation depends on maintaining the secrecy of the FBI’s role in Anom," the search warrant states.
Police: Anom's Reputation for 'Absolute Reliability'
As the unveiled investigation now reveals, "thousands of criminal users wrongly believed themselves to be unobserved in their communication via this service," said Jannine van den Berg, chief commissioner of the Netherlands' National Police Unit, aka the Politie, at the Tuesday press conference. "Eventually, hundreds of criminal organizations were using this platform. It has a good reputation among criminals. They mutually promoted it as the platform you should use for its absolute reliability. But nothing was further from the truth."
Law enforcement agencies have previously disrupted communications services that were allegedly developed by and for criminals, including EncroChat in June 2020, and Sky ECC in March. In both cases, police surreptitiously gained access to the networks and monitored communications. Intelligence gleaned from those efforts continues to lead to more arrests, recently including suspects in France and the Netherlands.
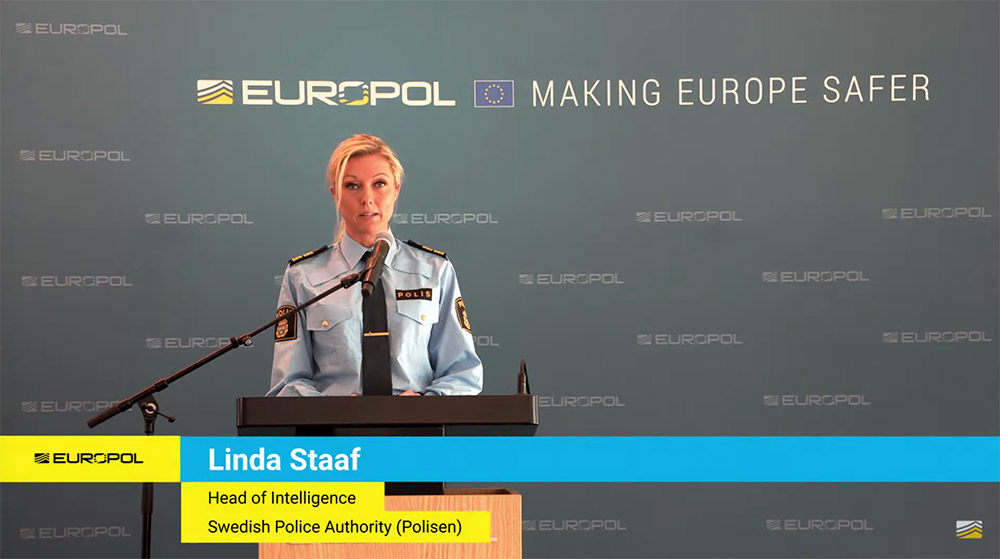
"The takedown of EncroChat was, from the Swedish point of view, a game changer in combating serious, violent crime," Linda Staaf, head of intelligence for the Swedish Police Authority - known as the Polisen - said at the Tuesday press conference. "Thanks to information from that server, we could arrest many of those who instigate murders. And for the first time, in many years, we've seen a decrease in shootings and explosions in Sweden."
The covert law enforcement operation demonstrates that rather than attempting to outlaw encryption or to weaken widely used services by requiring backdoor access, law enforcement agencies can successfully pursue other strategies.
"There’s more than one way to skin a cat," says Alan Woodward, a visiting professor of computer science at the University of Surrey. "It's notable that the criminals would rather trust an app that their 'friends' recommended than WhatsApp or Signal that seem to have worried governments so much. It’s as if the criminals think that mainstream app messengers have already been compromised by governments."
Anom Distribution Began in Late 2018
Anom appears to have been first distributed beginning in October 2018. That's when the FBI arranged with a confidential informant to begin offering Anom phones via three former distributors for the Phantom Secure encrypted communications service, primarily to individuals with suspected ties to Australian crime syndicates, according to the search warrant. "The growth of devices in Australia was initially slow," the warrant says, but "grew organically based on word of mouth" from the informant's "criminal distributors and other end users," before ramping up in the summer of 2019, at which point Anom had hundreds of users.
As of last month, the search warrant noted, the service had nearly 10,000 active users. "The top five countries where Anom devices are currently used are Germany, the Netherlands, Spain, Australia, and Serbia," the May 18 search warrant states.
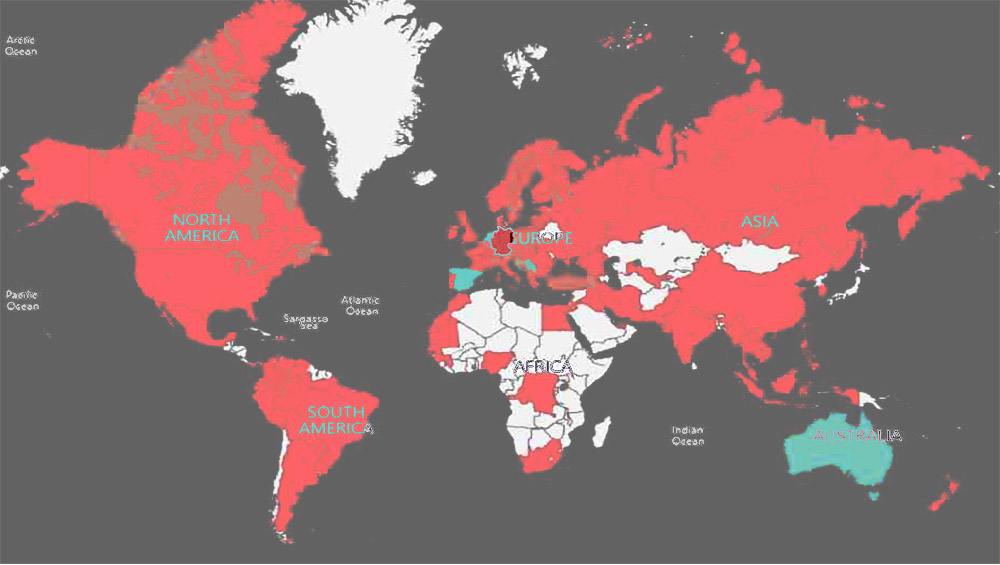
Officials say Anom users communicated in 45 languages. "Most of the messages were in Dutch, German and Swedish," said the Dutch Politie's van den Berg, and intelligence has been shared between all 16 countries participating in the effort.
Beyond Australia, the Netherlands, New Zealand, Sweden and the U.S., other countries participating in the investigation were Austria, Canada, Denmark, Estonia, Finland, Germany, Hungary, Lithuania, Norway and the United Kingdom including Scotland.
"For nine months, we have been receiving intelligence to build criminal cases" via Anom, the Swedish Police Authority's Staaf said. "We have also had information that has helped us to prevent more than 10 planned murders within Sweden. In addition to the arrests yesterday, we have arrested another 80 suspects during this operation, which makes a total of 155 arrests so far."
Fuel for Further Operations
Officials say that information and intelligence gleaned from this operation will fuel further investigations.
"Countless spinoff operations will be carried out in the weeks to come," Europol says, as part of a continuing effort to identify and take down "high-value criminal targets on a global scale."
"Just like during the investigation into Sky and EncroChat, the police were able to read millions of messages from national and international criminal organizations," van den Berg of the Dutch National Police Unit said. "The messages provide evidence for numerous ongoing investigations into serious organized crime."
Security experts say this is an obvious blueprint for how law enforcement agencies will continue to target crime syndicates by undermining the tools they rely on to communicate.
"It shows that the law enforcers are not trying to break the encryption per se; they are definitely going the equipment interference route," Woodward says. "Expect more of the same."





















