Account Takeover Fraud , Cybercrime as-a-service , Fraud Management & Cybercrime
Emotet Botnet Returns After Months-Long Hiatus
Security Researchers Detect New Spam Campaigns in US and UK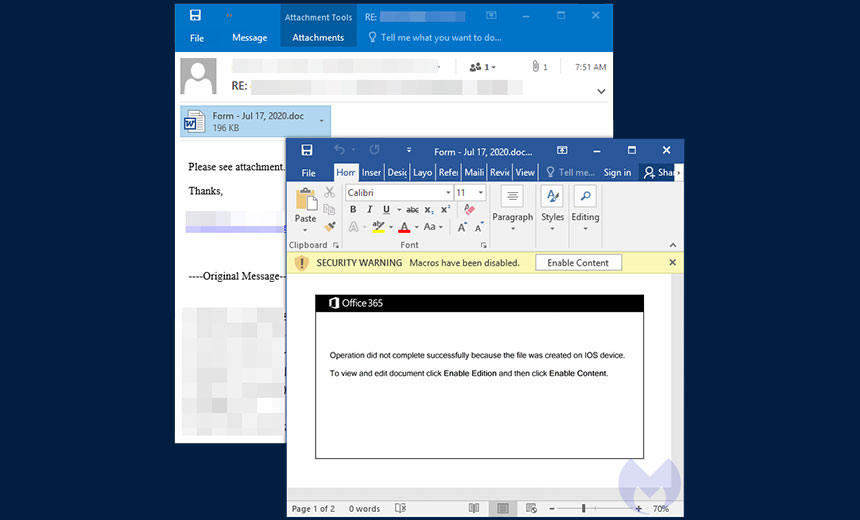
After a nearly six-month hiatus, the Emotet botnet sprung back to life on Friday with a fresh spam campaign targeting victims in both the U.S. and U.K., according to security research reports.
See Also: OnDemand | Ransomware 3.0: We Thought It Was Bad and Then It Got Even Worse
By late Friday, security firm Proofpoint had detected about 30,000 spam messages associated with the Emotet botnet.
Proofpoint researchers have confirmed their first sighting of #Emotet via email since early February, 2020. Delivery via Word attachment or URL to Word attachment download.
— Threat Insight (@threatinsight) July 17, 2020
Sample #IOCs
C2: 31.31.77.83:443
C2: 62.75.141.82:80
C2: 190.160.53.126:80
C2: 139.59.60.244:8080 pic.twitter.com/CO7KgqMh4I
"Emotet is a highly effective malware that is capable of downloading and installing a range of additional malware that often steal information, send malicious email, and spread across networks using infected devices to launch future attacks," says Sherrod DeGrippo, Proofpoint's senior director of threat research. "Its infrastructure is test and metric-driven and is built to scale depending on what’s working."
Proofpoint last detected Emotet on Feb. 7. On July 13, researchers at security firm Malwarebytes detected new botnet activity before the first wave of malspam started on Friday.
Why Emotet, which is considered one of the more dangerous and prolific malware variants currently in circulation, went quiet in February and then sprung back to life now remains a mystery, says Jerome Segura, director of threat intelligence at Malwarebytes.
"Emotet, like other criminal gangs, have had 'downtime' before, but typically surrounding specific holidays. It's unclear why they went on such an extended break, in particular before the [COVID-19] pandemic had even started," Segura tells Information Security Media Group.
Latest Campaign
The new Emotet campaign starts with phishing emails blasted out to as many potential victims as possible. These messages typically contain one line of text and ask the user to open a malicious Word document attached to the email called "electronic.form," according to security research reports. Sometimes the phishing emails contain a URL and ask the user to click on it.
The subject lines of the phishing emails are fairly simple, according to Proofpoint.
"Subject lines like 'RE:', 'Invoice #' followed by a fake invoice number are commonly seen, and often include the name of the organization being targeted," the Proofpoint report notes.
If the user opens the attached document, malicious macros are enabled that attempt to download the Emotet malware. Typically, a PowerShell script is launched that attempts to contact various remote websites to download the full payload, according to Malwarebytes. Once contact with the site is made, Emotet is downloaded onto the device and connects with a command-and-control server.
Once Emotet is downloaded to an infected device, it installs additional modules to steal credentials, harvest emails and spread itself across local networks, according to Proofpoint.
Over the years, Emotet has been redesigned to download secondary malware onto infected devices. This includes malicious code variants such as Qbot, The Trick, IcedID, and Gootkit. In other cases, Emotet is combined with TrickBot in order to download Ryuk ransomware (see: Emotet, Ryuk, TrickBot: 'Loader-Ransomware-Banker Trifecta').
Emotet's History
Emotet first appeared as a banking Trojan in 2014, and over the years its operators, which Proofpoint identified as a group known as TA542, have adjusted its code and it now primarily works as a botnet delivering other malware to infected devices, according to security researchers.
Over the years, researchers have noticed that Emotet will suddenly re-emerge after periods of inactivity.
After a four-month absence, Emotet came back to life in September 2019 and continued sending out malicious spam and phishing emails until it went quiet again in February (see: Researchers: Emotet Botnet Is Active Again).
In January, just before the World Health Organization declared COVID-19 a global pandemic, IBM researchers found Emotet operators using COVID-19-themed phishing emails to spread Trojans as well as other malware (see: Fake Coronavirus Messages Spreading Emotet Infections).
Managing Editor Scott Ferguson and News Editor Doug Olenick contributed to this report.






















