Cryptocurrency Fraud , Cybercrime , Fraud Management & Cybercrime
DreamBus Botnet Targets Linux Systems
Researchers Say It Hijacks Powerful Computer Systems to Mine Monero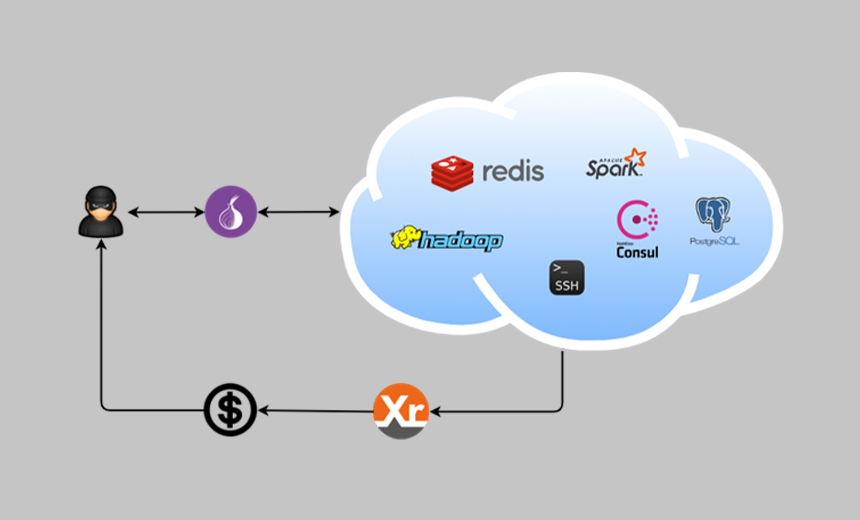
Zscaler's ThreatLabz research team is tracking a new botnet dubbed DreamBus that’s installing the XMRig cryptominer on powerful enterprise-class Linux and Unix systems with the goal of using their computing power to mine monero.
See Also: Bank on Seeing More Targeted Attacks on Financial Services
DreamBus presents a serious threat because of the many components it uses to spread via the internet and the wormlike behavior that enables it to move laterally once inside a targeted system, ThreatLabz says. Many of the bot’s components have previously been detected, some as far back as 2018, the report states.
Based on the time stamps associated with the deployment of new commands, Zscaler believes the attackers are located in Russia or Eastern Europe. Zscaler does not know how many organizations have been hit.
Attack Route
DreamBus, which is based on a series of executable and linkable format binaries and Unix shell scripts, uses a number of methods to identify victims. These include using different modules to search for targets with weak passwords or remote code execution vulnerabilities in popular enterprise applications, such as Secure Shell, as well as IT administration tools, cloud-based applications and databases, the researchers say. The botnet can exploit applications that include PostgreSQL, Redis, Hadoop YARN, Apache Spark and HashiCorp Consul.
The attackers are targeting Linux-based systems because they are softer targets than Windows-based systems, the researchers say. "This is, in part, because Linux-based malware is less common than Windows-based malware, and thus receives less scrutiny from the security community," the report notes.
While installing a cryptominer is the primary goal of the attack, once safely ensconced inside a system, the attackers have the option to upgrade the attack to something more insidious.
"The threat actor can potentially pivot in the future to more destructive activities such as ransomware, or stealing an organization’s data and holding that information hostage," the report states.
Technical Analysis
The DreamBus botnet uses a modular design, with developers rolling out new modules on a regular basis. The researchers say most of its command-and-control components are hosted through the TOR browser or on an anonymous file-sharing service, such as oshi[.]at. And they leverage the HTTP protocol.
The botnet can scan an organization's intranet to find and infect devices not directly facing the public internet. This is accomplished by having a module that scans the internal RFC 1918 for vulnerable applications that are targeted when found, the researchers say.
The primary spreader, however, is an ELF binary that’s designed to spread through SSH. It’s responsible for setting up the required environment, infecting systems with copies of itself, downloading new modules for spreading and deploying XMRig to mine Monero cryptocurrency.
Researchers note that each DreamBus ELF binary is packed by UPX with a modified header and footer, which is designed to obfuscate the malware’s code and reduce the file size.
"While this slight modification breaks the UPX command-line tool, the ELF binary is still valid. Therefore, it can be unpacked and executed,” the researchers say. “This simple change may be sufficient to bypass some security software. Antivirus software often has low detection rates for DreamBus and its various modules.”
To make sure the DreamBus botnet can be used across a range of Unix- and Linux-based operating systems, during an attack the hackers supply downloads of various dependencies and components if they are not present on the compromised system, Zscaler says.






















