Cybercrime , Fraud Management & Cybercrime
Darknet Markets Thrive Despite Repeat Disruptions by Police
190 'Significant' Darknet Markets Debuted in 2022 to Meet Demand, Researchers Say
Despite repeated takedowns by law enforcement, darknet markets continue to thrive.
Last year, 190 "significant" new darknet markets or forums debuted, threat intelligence firm Flashpoint reports.
Ransomware-as-a-service groups patronize these black market e-commerce sites to advertise for affiliates. Initial access brokers use them to advertise new victims, while malware developers hawk their wares and data brokers sell stolen information, including payment card details. They're typically reachable only via an anonymizing network - aka darknet - such as Tor or I2P.
The debut of new markets continues as upheaval remains constant. Western law enforcement last year scored takedowns of several major players, including SSNDOB, RaidForums and Hydra, which the FBI says handled 80% of darknet market transactions in 2021 (see: Hydra Darknet Market: Threat Intelligence Lessons Learned).
Russia also cracked down. In early 2022, Russian authorities disrupted major carder markets selling stolen payment card data, including UniCC, Ferum Shop, Sky-Fraud and Trump's Dumps, aka TDStore. Despite that crackdown, the carder ecosystem rebounded by May 2022, threat intelligence firm Recorded Future reports.
After major players get disrupted by law enforcement, fresh alternatives typically debut quickly. "We have observed this cycle of dark web markets before, from Silk Road to Silk Road II to Silk Road Reloaded; there are always competitors, copycats and scammers looking to capitalize on displaced dark web users," Flashpoint says.
Russia's invasion of Ukraine, which escalated to a war of conquest in February 2022, has also had an impact on darknet markets. "The war has widened the splits in the cybercrime underground," Ian Gray, director of analysis and research at Flashpoint, told Information Security Media Group.
Following Hydra's demise, Flashpoint found that a pro-Ukrainian faction had migrated to RuTor, backed by marketplace OMGOMG - aka OMG!OMG! - while a pro-Russia faction embraced WayAWay/Kraken, which isn't affiliated with the legitimate San Francisco-based cryptocurrency exchange of the same name.
While Russian-language markets are well known for serving only Russians, experts say that's not the dominant darknet market language globally. "English continues to serve as the lingua franca of the underground," said Gray. "We have observed various types of fraud focus on specific regions - for example, drug sales, carding and malware development," which is localized for that region, and in those cases, the markets often use the local language."
Many of Hydra's buyers and sellers first regrouped using encrypted chat apps, Gray said. "Without the structure of a marketplace, encrypted messaging apps lend themselves to direct interactions between vendors and customers. But they do not offer the relative security offered by a marketplace," Gray said (see: Why Encrypted Chat Apps Aren't Replacing Darknet Markets).
But while encrypted chat apps might provide a lifeline, buyers and sellers often get drawn back to markets because they offer users multiple protections, including buyer and seller ratings for quality of service, escrow features for holding funds until orders get fulfilled, and dispute resolution services (see: Cybercrime: Darknet Markets Live on, Even as Players Change).
What's on Offer
On the cybercrime front, researchers report that popular darknet market offerings seen last year included:
- Stolen records: Markets known as log shops do a roaring trade in valuable, stolen information. Flashpoint reports that misconfigured databases and services continue to provide much of the data being sold and that despite misconfigurations being tied to only 5% of reported breaches, 71% of lost records were due to misconfigurations.
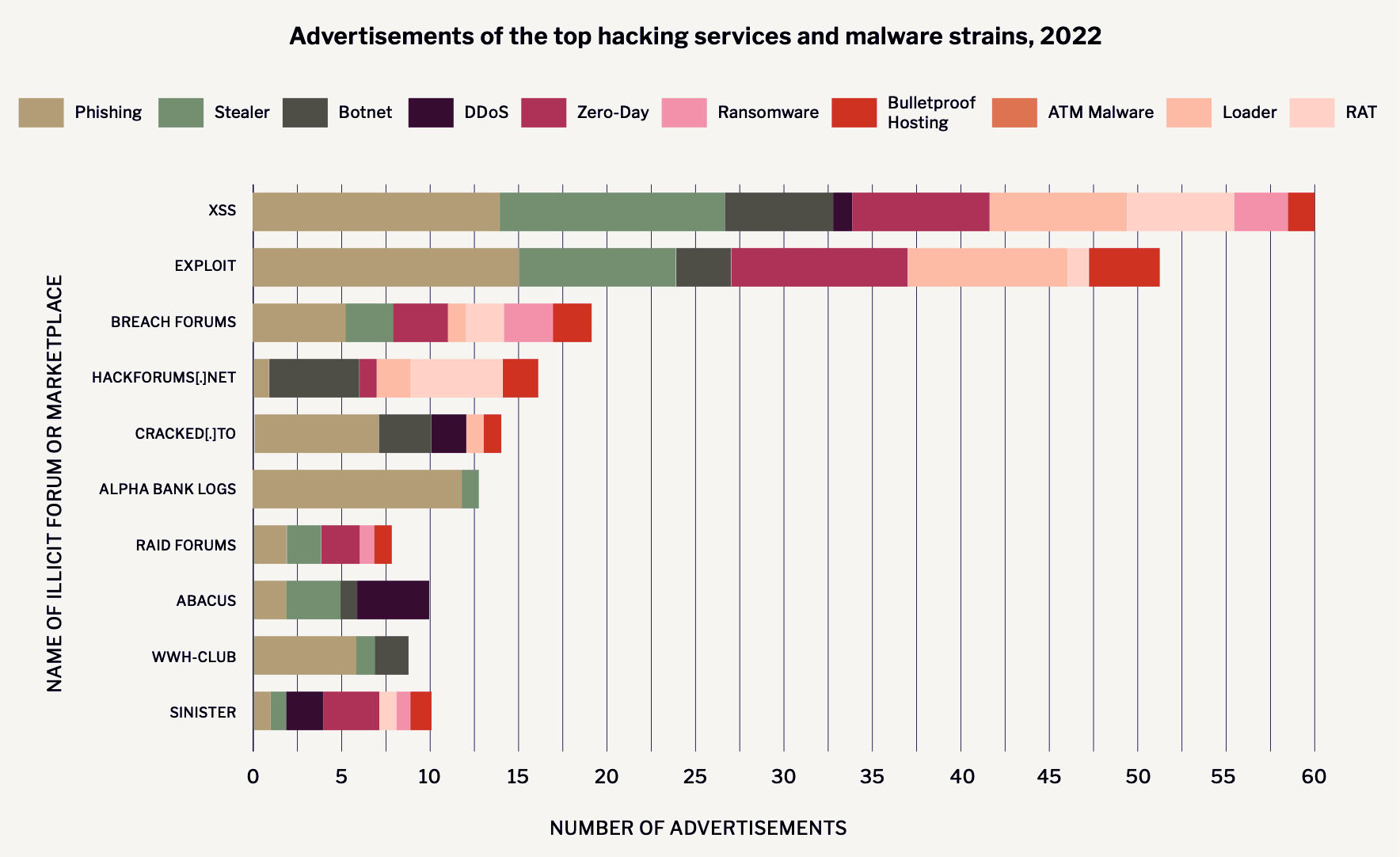
- Malware: Information stealers - aka info stealers - and other types of malware remain wildly popular and increasingly accessible. Last year, Raccoon, RedLine and Vidar were especially popular, while newcomers AcridRain and TyphonStealer also appeared, Flashpoint says. Info stealers are often used to gather payment card data, cryptocurrency wallet credentials and personal identifiable information, much of which ends up for sale in log shops - for criminals who want to use the stolen credentials to emulate consumers, IT administrators and others.
- Phishing kits and services: The capabilities these offer continue to improve. For example, a new phishing-as-a-service platform called EvilProxy, launched last May is designed to steal session cookies and bypass multifactor authentication defenses - to give attackers remote access to a victim's network.
- Vulnerability exploits: Discussion of known vulnerabilities is rampant on cybercrime forums, where exploits sell for $2,000 to $4,000 - or more than $10,000 for advanced ones - and "factors such as the range of products affected or the ease of use" affect the asking price, Flashpoint says.
Recorded Future says there has been a shift in crime trends, and Russian criminals are likely to embrace more payment card fraud as their country faces economic sanctions following the Kremlin's 2020 invasion of Ukraine. "Regardless of fraud's reputation as an unsophisticated form of cybercrime, it is likely becoming less a crime of opportunity than of survival," the company says.
At the same time, darknet markets remain highly "resilient" as well as "viable and widespread despite turnover due to takedowns, shutdowns and exits," Flashpoint's Gray said. "The overall illicit economy is alive and well."






















