Account Takeover Fraud , Card Not Present Fraud , Cybercrime
Cybercriminals Target Newbie Bad Actors With Phishing Sites
Fake Card Shops Used to Dupe Inexperienced CybercriminalsMultiple cybercriminal groups appear to be targeting relatively new entrants in the space with phishing attacks.
See Also: OnDemand | Payments Without Borders: Prevent Fraud and Improve the Customer Experience
In what the analysts call a "cannibalistic approach," these gangs are impersonating underground card shops - such as Joker’s Stash, BriansClub, Uniсс, Ferum Shop and ValidCC - to dupe the newbies for monetary gain, according to a new report from Singapore-based cybersecurity company Group-IB.
Dmitry Shestakov, head of cybercrime research at Group-IB, tells Information Security Media Group: "There is no honor among thieves. Cybercriminals often deceive each other, underground markets get breached from time to time - this is a fairly common practice. Nothing really stops carders from playing dirty, as the 'victims' — also carders in this case - cannot take legal actions."
The phishing websites, which Ruslan Chebesov and Sergey Kokurin at Group-IB in their report call "fake shops", were largely created by three groups that the analysts identify as UniFake, JokerMantey and SPAGETTI.
The network infrastructure established by the three gangs includes thousands of domain names used for phishing, the report says. It adds that SPAGETTI has the largest known network, operating more than 3,000 domain names.
Card Shops and Associated Marketplaces
The report describes the card shops and associated marketplaces in the underground as the Amazons and eBays of the dark web for banking-related data. They are primary resources used by smaller criminals engaging in small-scale fraud such as bank card fraud - or carding, scams and spamming, the analysts add.
"Card shops are a type of underground market. They are used to sell stolen bank card data in the form of full cardholder records (including name, card number, CVV, expiration date) or dumps: copies of a magnetic strip of a bank card," the analysts say.
Compromised data not related to bank cards are usually not sold on card shops, they add.
To be a member of genuine underground card shops and markets, users are required to pay account activation charges that range between $20 and $200 and/or deposit money into their accounts to buy compromised data, the analysts tell Information Security Media Group.
The fake shops take advantage of the prepayment process to mislead cybercriminals, the report notes.
Fraudsters add a layer of genuineness by using names of existing underground resources and completely copying their design, the analysts say, adding that when users spend their money in these fake shops, the operators collect the payments into their own crypto wallets.
The report notes that fake shops are not created one by one - they're usually set up in large clusters. "To reach more potential buyers of compromised bank card data, creators of fake shops place ads on underground forums and Telegram chats, and trick users into visiting their resources. As ironic as it sounds, this damages the reputation of the original websites," the analysts say, and note that alternatively, the smaller fake sites are merged into larger networks.
SPAGETTI
SPAGETTI, the largest of the three networks discovered, has seen more than 9,200 incoming transactions to various cryptocurrency wallets, the analysts note. They found that the amount received was largely in Bitcoin (23 BTC) and amounted to more than $1.2 million, according to the exchange rate on Oct. 12, 2021.
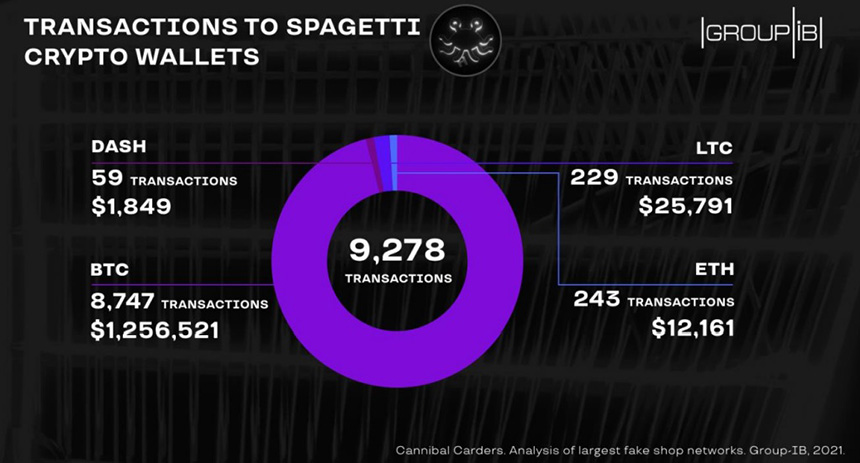
The cryptocurrency wallet addresses may have changed since the SPAGETTI fake shops network was created, so the actual revenue may be significantly higher, the analysts add.
Although SPAGETTI has several independent fake shops, its main "asset" is the one that masquerades as one of the oldest and largest card shops, called BriansClub, which has very few clones in the carding market, the analysts note. SPAGETTI's creators, they say, use a phishing domain called briansclub[.]ru. Apart from making money off the account activation fee fraud, it also spreads malware through its websites, the analysts note.
According to the report, after the activation fee for the fake briansclub[.]ru is paid, users are shown a "success" message and are asked to download a "protected" app from a link to an archive called "panelcontrol.rar." The archive contains two files: "PanelControl.exe" and "LitePanel.exe".
The former, instead of providing access to the card shop panel, launches a stealer called Taurus Project, the analysts say.
Also known as Taurus Stealer, the C/C++ information-stealing malware has been used in the wild since April 2020, according to news platform Security Boulevard. Promoted on a Telegram channel and Russian-language underground forums, it is likely developed by Alexuiop1337, who also created Predator the Thief malware, the report says.
Describing the stealer's activities, the analysts say that "the Taurus Project stealer not only collects information from Chrome, Opera and Firefox browsers, but also gains access to the camera and collects login details from multiple cryptocurrency wallets such as Bitcoin, Ethereum and Bytecoin. This means that after launching the file, an inexperienced user could lose the login details for their cryptocurrency wallets used to pay for the activation as well as lose access to other resources, including other card shops."
UniFake
UniFake which gets its name from the majority of fake domain names that impersonate variations of card shop Unicc, has more than 100 domain names. Of these, the analysts say that 66 are variations of the name Unicc. The analysts have identified 150 transactions made on the UniFake network, amounting to $17,377 at the Oct. 12, 2021, exchange rate.
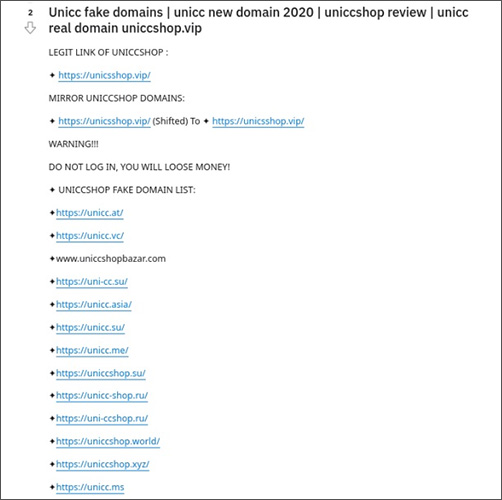
Unicc, according to the analysts, is one of the biggest underground card shops. "It was launched in 2012 and soon became popular among carders due to the large number of updates, but also among card shops that act as intermediaries and sell Unicc data for a commission using their own API systems for selling cards. These factors have most likely contributed to the (site’s) emergence," they say.
Most of these domains have a striking resemblance to Unicc's actual site design, apart from the fact that "the crypto wallets in the account activation are controlled by the fake shop owners," the analysts say.
JokerMantey
JokerMantey, a fake shop network that impersonates and phishes in the name of popular card shop Joker's Stash, has more than 20 fake domain names and also includes fake shops copying BriansClub card shop.
The original Joker's Stash owners shut the shop down in February 2021 (see: Joker's Stash Reportedly Shutting Down Operations).
The reports says that is why cybercriminals are using the same name to operate on the dark web. JokerMantey operators are less likely to face retaliation from the original card shop even if their malicious activities are detected, since the original card shop has already closed down, it says. "This makes it lucrative," the analysts add.
The analysts also identified two related Bitcoin wallets: one Litecoin and the other Dash, which they retrieved from the payment form on the phishing site.
The analysts note that until October 2021, JokerMantey has received a total of 304 transactions in its associated crypto wallets, amounting to $220,587, according to the same month's exchange rate.
Consequences of Fake Shops
"Some newbie carders who get scammed leave this illicit business, while others learn from their mistakes, become more careful and continue carding activity,” Shestakov tells ISMG.
He says the original illicit carding websites obviously suffer reputational damage. "Deceived carders talk about their negative experience on underground forums without realizing that they fell prey to fake shops. Such reviews cause distrust among both regular card shop users and partners, resulting in profit losses for original carding markets. Original card shop owners, in an attempt to prevent losing customers and damaging their reputation, go so far as to post lists of fake shops that impersonate them."
Nonetheless, Shestakov says, these fake shops will continue to exist because "card shop owners do not have legal means to shut down fake shops impersonating them."
He says the fake shops have an impact on security research and threat intelligence because they can cause false positives. "Without knowing that they are dealing with the fake shop," Shestakov says, "threat intelligence specialists can alert customers and the public with inaccurate and misleading information."






















