Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development , Ransomware
Crypto-Locking Ransomware Attacks Spike
Ransomware-as-a-Service Market Expands Beyond Affiliates to 'Elite' Programs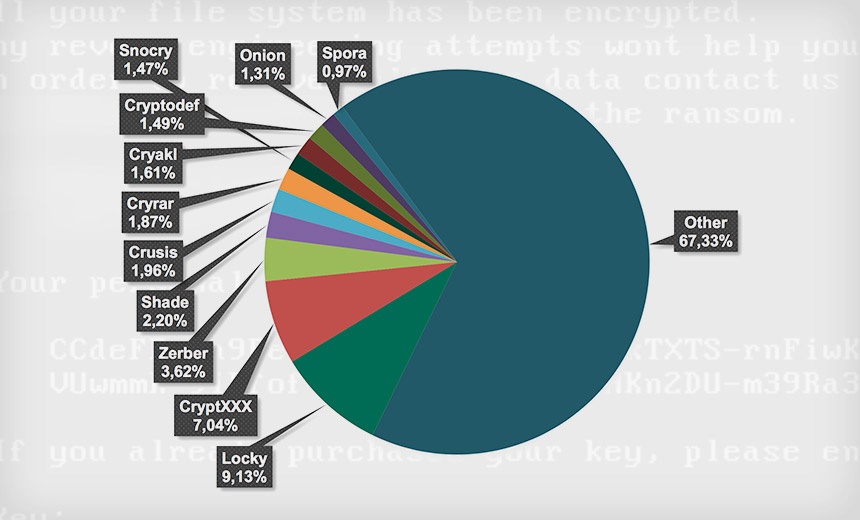
With the massive profits available to criminals who can infect PCs and servers and successfully extract a ransom from victims, it's no surprise that attacks involving crypto-locking ransomware continue to increase.
See Also: Cybersecurity Checklist: 57 Tips to Proactively Prepare
From April 2016 to March 2017, the number of people who encountered ransomware grew more than 11 percent to 2.6 million, according to a new report from Moscow-based anti-virus firm Kaspersky Lab. The report is based on ransomware strains encountered by users of its security products during that 12-month period.
Comparing that 12-month period to the same period a year earlier, the number of users who were attacked with crypto-locking ransomware nearly doubled, rising from 719,000 to 1.2 million, the firm's security researchers found.
Unfortunately, the ransomware reality has only gotten worse since then. In May, for example, WannaCry appeared, demonstrating how marrying a worm - capable of targeting a widespread bug - with ransomware could lead to an unexpectedly rapid outbreak.
Earlier this month, meanwhile, South Korean web hosting firm Nayana made headlines after it agreed to pay a $1 million ransom to decrypt 153 Linux servers that had been hit by ransomware. It's the largest known ransomware payoff to date.
And on Tuesday, a global Petya ransomware outbreak affected organizations in Ukraine, Russia, the United Kingdom, India and beyond, targeting the same EternalBlue flaw as WannaCry to proliferate rapidly (see Global Petya Ransomware Outbreak Spreads).
Mobile Ransomware Declines
On the upside, however, comparing April 2016 to March 2017 with the prior 12-month period, the number of users who encountered mobile ransomware decreased by 5 percent, from 137,000 users to 130,000 users.
Even so, Kaspersky Lab saw an increase in mobile ransomware attacks in the beginning of 2017, thanks to just two mobile ransomware malware families, Fusob and Svpeng, which primarily targeted Android mobile device users in the United States, Canada, Germany, the United Kingdom and Italy. One caveat, however, is that those statistics were gathered only from users running the security firm's Android software, and thus may not be representative of the general population.
Profit Still King
Cybercrime is a business, and criminals increasingly look to ransomware for an easy payday. Barriers to entry, especially for non-technical users, continue to decrease (see Want to Get Into Ransomware? This Kit Costs Just $175).
Meanwhile, more sophisticated gangs are bringing better business acumen to bear, to not only infect large numbers of systems, but also to provide the customer service environment that might be required to handle ransom-demand negotiations as well as guide victims into procuring the demanded cryptocurrency - most often still bitcoins - to pay the ransom and receive the promised decryption key.
Diversity Rules
The use of cryptocurrency and the increasing diversity of ransomware providers complicates attempts to disrupt such activities - for example, by attempting to track down and arrest ringleaders or disrupt related attack infrastructure.
From April 2015 to March 2016, the most active - as in widely propagated - ransomware seen by Kaspersky Lab were Bitman, Cryakl, Cryptodef, Mor, Onion and Shade. Even so, these malware families only accounted for 31 percent of ransomware attacks seen during that period.
"A year later the situation had not changed considerably," Kaspersky Lab reports. "Most widespread families - including Locky, CryptXXX, Zerber, Shade, Crusis, Cryrar, Snocry, Cryakl, Cryptodef, Onion and Spora - together hit about 33 percent of all users attacked with crypto-ransomware during the period."
Ransomware-as-a-Service Grows
This year, ransomware's reach and severity has continued to expand. As security firm McAfee noted in a December 2016 report: "2016 may be remembered as 'the year of ransomware,' with both a huge jump in the number of ransomware attacks and significant technical advances in this type of attack."
One of the trends noted in that report was the continuing growth of the ransomware-as-a-service marketplace, which first launched in 2015. But it continued to expand throughout 2016 with the appearance of Shark, later rebranded as Atom; Petya, aka Mischa; and Cerber.
Ransomware-as-a-service typically involves a developer or group sharing the code with affiliates, who infect endpoints - historically via exploit kits, although more often now via social engineering and spam - and share a percentage of their profits back with the developer (see Inside the Cerber Ransomware-as-a-Service Operation)
"While ransomware-as-a-service is not a new trend, this propagation model continues to develop, with more and more ransomware creators offering their malicious product," according to Kaspersky Lab's report. "This approach has proved immensely appealing to criminals who lack the skills, resources or inclination to develop their own malware."
Gaining access to an affiliate program can require "nothing but the will to conduct certain illegal activities and a couple of bitcoins as a partnership fee," Kaspersky Lab reports. The harder affiliates work, the more money they stand to make.
Access to many affiliate programs is exclusively via closed Russian cybercrime forums, security experts note.
The ransomware used in these schemes is fully functional Petya, for example, introduced full-disk encryption - not just encrypting files - by encrypting the file system table, thus disabling a victim's ability to even boot his PC. Petya was also the first strain to begin doubling the ransom demand - in its case, after seven days, McAfee reports.
Enter the 'Elite' Program
While affiliate programs abound in the cybercrime sphere, Kaspersky Lab says it's increasingly seeing a higher level tier of "elite" programs, which have a high bar for entry, including a mandatory recommendation from someone else in the program, as well as a proven ability to distribute large quantities of malware.
"In one case we observed in the last year, the candidate had to demonstrate their ability to complete at least 4,000 successful downloads and installations of the malware on victims' PCs," Kaspersky Lab says. "In exchange, the partner gets some free tools for the obfuscation of ransomware builds (in order to make them less visible to security solutions) and a good conversion rate - up to 3 percent, which is a very good deal, at least compared to rates that legal affiliate programs offer."
For example, based on that 3 percent conversion rate, for every 0.5 bitcoin ransom payment - currently worth $1,200 - that their ransomware produced, the "elite" program member would receive $36.
Low and Slow
Kaspersky Lab also reports seeing an increase in ransomware campaigns that target corporate networks, conduct extensive reconnaissance - sometimes lurking on a network for six months - and only then unleash crypto-locking malware. So far this year, the security firm says it has identified eight criminal groups targeting financial services firms, including the developers behind PetrWrap - based on stolen Petya source code, "the infamous Mamba group" - as well as six other unnamed groups.
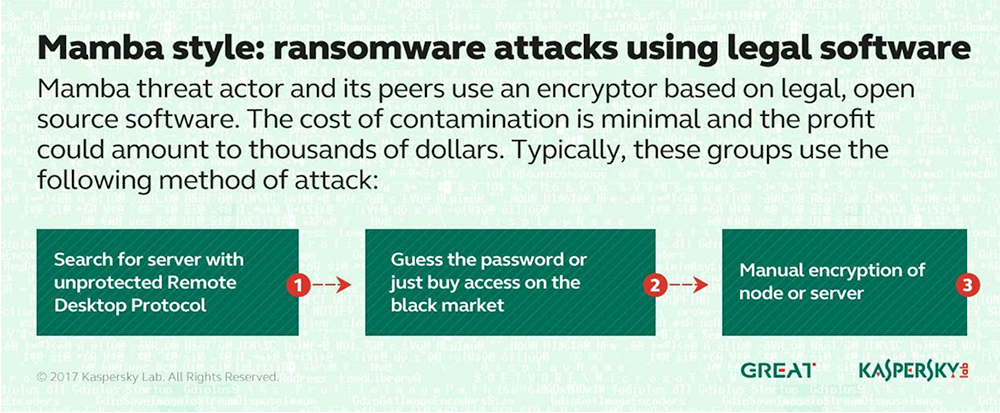
"In general, the tactics, techniques and procedures used by these groups are very similar," Kaspersky Lab says. "They infect the targeted organization with malware through vulnerable servers or spear-phishing emails. Then they establish persistence in the victim's network and identify the valuable corporate resources to encrypt, subsequently demanding a ransom in exchange for decryption."
Some attack groups, such as the Mamba group, use off-the-shelf or open source tools, in part to disguise their activities. In the case of Mamba, the gang has built crypto-locking malware based on the open source DiskCryptor software, Kaspersky Lab notes. "Once the attackers gain a foothold in the network, they install the encryptor across it, using a legal utility for Windows remote control," the security firm says. "This approach makes the actions less suspicious for security officers of the targeted organization."
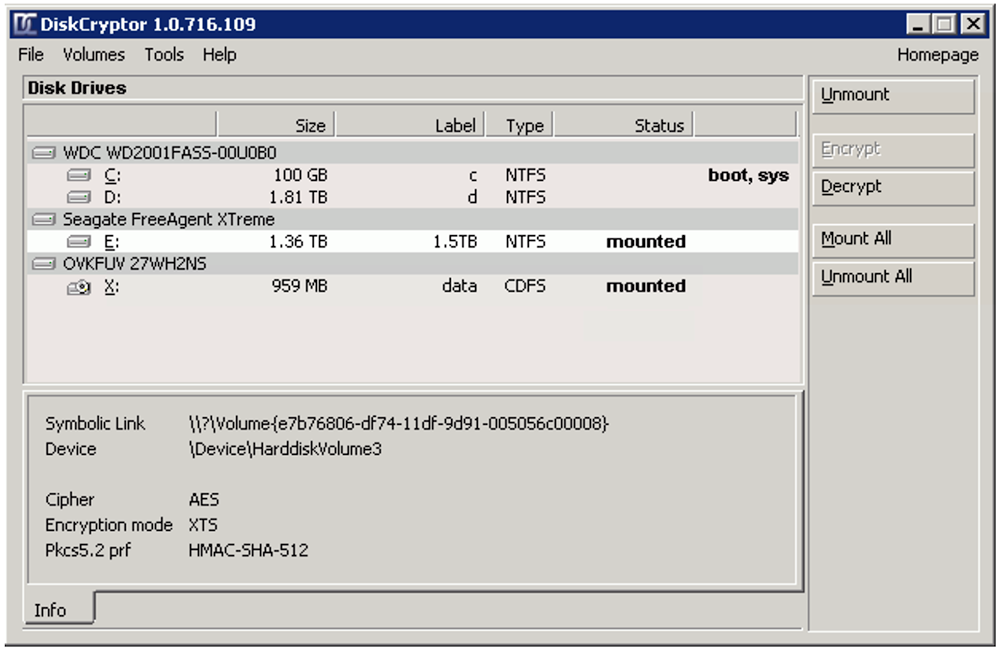
Such attacks can be lucrative. In some cases, Kaspersky Lab notes, it's seen ransom demands of 1 bitcoin - currently worth $2,400 - per encrypted endpoint. For criminals, that represents a massive potential payday. As shown by the growth in ransomware attacks, they continue to try to cash in.





















