3rd Party Risk Management , Cloud Access Security Brokers (CASB) , Governance & Risk Management
Cloud Security: Mess It Up and It's on You
Jay Heiser of Gartner Says the Cloud Demands New Security Processes, Tools
The transition to cloud-based software and infrastructure has revolutionized development and services. But it’s also created a bevy of new security challenges that continue to catch organizations off guard.
See Also: Security Pros and Cons on Different Cloud Types: SANS Analysis
Although the cloud has been heralded for more than a decade as the new computing model, it easy to forget that it’s actually still in early stages. Many can say they grew up on Unix, Windows or Linux, but few active professionals can say they grew up on the cloud, says Jay Heiser, a research vice president at Gartner.
Heiser, who spoke at Gartner’s Security and Risk Management Summit in Sydney on Monday, has a clear message for those moving to the cloud and wondering if that poses a risk: “One thing I am going to repeat as the core idea of cloud security is that if you don’t get it right, it’s your fault."
Vetting CSPs? Probably Unneeded
Gartner predicts prodigious growth in security products for cloud environments - at a 40 percent compound annual growth rate.
A few cloud service providers - including Allscripts, Google and Salesforce – have had a security incidents over the last couple of years, but hacking is rare. As a result, ensuring that a cloud deployment is secure on an organization’s own side is time better spent than extensive vetting of a cloud service provider, Heiser says.
"Cloud service providers do a great job of drawing the line between their responsibility and your responsibility. And so far, AWS has done a great job of always blaming their customers. So be forewarned."
—Jay Heiser, Gartner
The majority of incidents are the result of errors and misconfigurations by cloud service providers’ clients, Heiser says. That’s due in part to how fundamental security practices of the past don’t apply to cloud computing models.
Take Capital One, a financial services company that’s been one of the most aggressive in that vertical in embracing the cloud. A Seattle woman, Paige A. Thompson, is accused of taking advantage of a misconfigured firewall to gain access to more than 100 million credit card applications going back to 2003 (see: Woman Arrested in Massive Capital One Data Breach).
She allegedly gained access credentials for a role with expansive permissions, including the area where the credit card applications were stored. AWS, Capital One’s service provider, has indicated the problem wasn’t on its side.
“Security in the cloud is your responsibility, whether or not your cloud service provider makes it easy for you,” Heiser says. “Cloud service providers do a great job of drawing the line between their responsibility and your responsibility. And so far, AWS has done a great job of always blaming their customers. So be forewarned.”
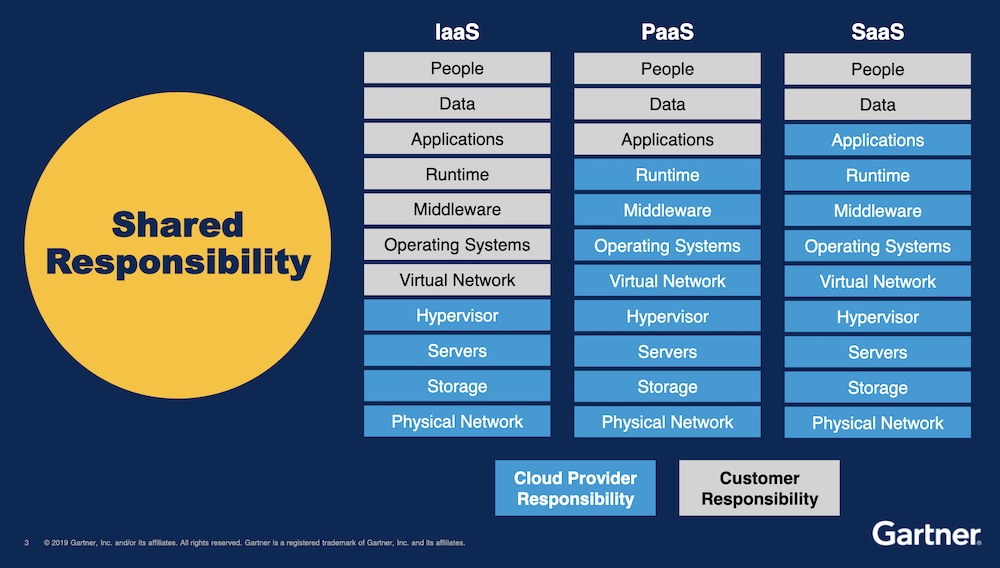
Organizations would be better served by not focusing so much on the security of a cloud service provider, but rather how they handle the new processes demanded by the cloud, Heiser argues.
So how can organizations reduce the risks?
Infrastructure-as-a-service providers have ways to publicly share data objects, generating URLs. The defaults are usually not to allow data shares, but developers may change those controls, potentially increasing the risks.
Software-as-a-service is different, and the defaults are usually allow open shares, such as Microsoft’s OneDrive, Heiser says. It may not be efficient to turn off sharing because users would likely turn to email to share documents. But what’s important is to build policies around that sharing, Heiser says.
“File sharing is easy to govern, but you have to recognize and try it,” he says.
And then there's the open bucket problem. Security researchers and fraudsters scan the web looking for open Amazon S3 buckets, and often they’ve found astounding stores of data. Turning off the public access is easy, but often it’s done too late. “It’s an easy thing to control,” Heiser says.
That dovetails with permissions. “The tendency is to allow too many people to have admin privilege,” Heiser says. “Why should every programmer be allowed to share S3 buckets with the outside world?”
Tools of the Trade
Two keys points with cloud deployments are visibility and policy enforcement. Heiser contends organizations can’t control the cloud without control automation, and there are emerging tools, including cloud access security brokers. As the title of one Heiser’s slides says: “CASBs are to cloud as firewalls are to data centers.”
CASBs sit between an organization and a service provider, applying policies, maintaining visibility, monitoring users and other functions such as data loss prevention, threat protection and compliance. Gartner considers CASBs the best security tool when moving to the cloud.
On the infrastructure side, cloud workload posture management tools have features such as risk identification, monitoring, DevOps integration, threat protection and policy enforcement.
And cloud workload protection platforms can be used for IaaS and platform-as-a-service implementations. CWPPs can help with exploit prevention, application white listing, network segmentation, system monitoring and workload configurations.
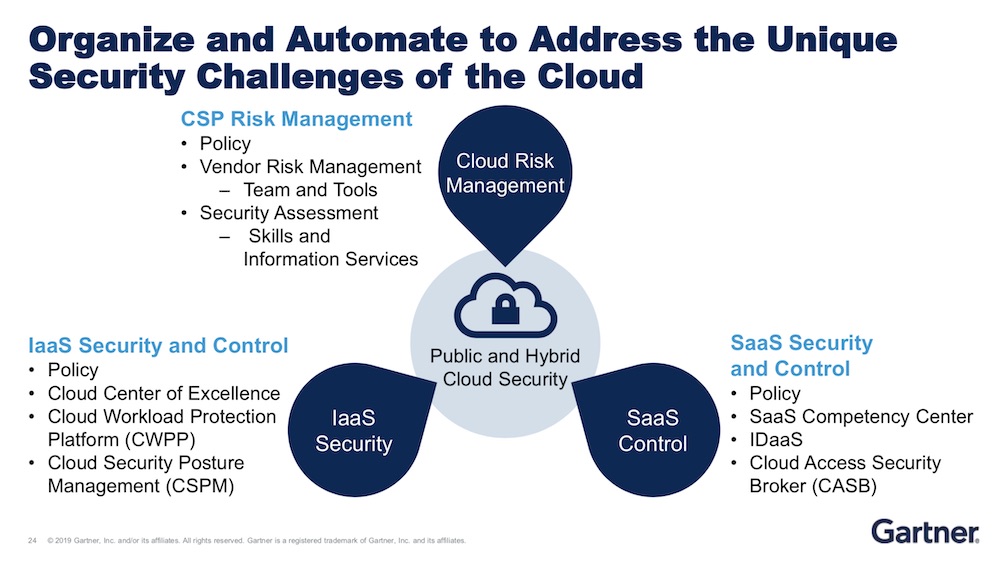
Heiser says many organizations are using their SIEM tools for event monitoring within the cloud. That kind of logging and monitoring is critical, Heiser says.
Capital One, for example, was able to supply key information to the FBI after it became aware of the attack, Heiser says, and Thompson was quickly arrested.
The ephemeral nature of how cloud services are architected is another aspect to keep in mind. Once a machine image is expunged, there’s no possibility of forensics, Heiser says.
“We do need to figure out how to do event monitoring,” Heiser says. “But you can’t provide an ad hoc forensic examination of an image once that image is gone.”

















