Endpoint Security , Fraud Management & Cybercrime , Incident & Breach Response
Would Cheaper Windows Upgrades Solve Ransomware Woes?
Discounts Are a Good Start, But Won't Magically Fix Deeper Problems
By lowering the price of its Windows operating system, could Microsoft help stop the spread of mass ransomware worms?
See Also: The Cybersecurity Swiss Army Knife for Info Guardians: ISO/IEC 27001
India seems to think so. In an exclusive story, Reuters reported on Friday that Microsoft has agreed "in principal" to a "sharply discounted one-time" deal for upwards of 50 million Windows users in the country.
The request came from India's government, which reportedly approached Microsoft last month after the WannaCry ransomware outbreak. WannaCry, which U.S. and U.K. intelligence agencies believes was engineered by North Korea, infected as many as 300,000 computers with file-encrypting ransomware.
The urgency to rapidly find a solution has been magnified by a second attack of ransomware resembling malware called Petya. The ransomware last week first ravaged Ukrainian organizations before going much further, including hitting such high-profile targets as shipping giant Maersk and a Cadbury chocolate factory in Tasmania (see Massive Malware Outbreak: More Clever Than WannaCry).
There's little argument that the continued use of older Windows operating systems has contributed to global information security weaknesses. Microsoft has acknowledged as much, making rare policy exceptions twice in as many months by issuing patches for "no longer supported" operating systems dating back to XP (see Microsoft Issues Another Emergency Windows XP Patch).
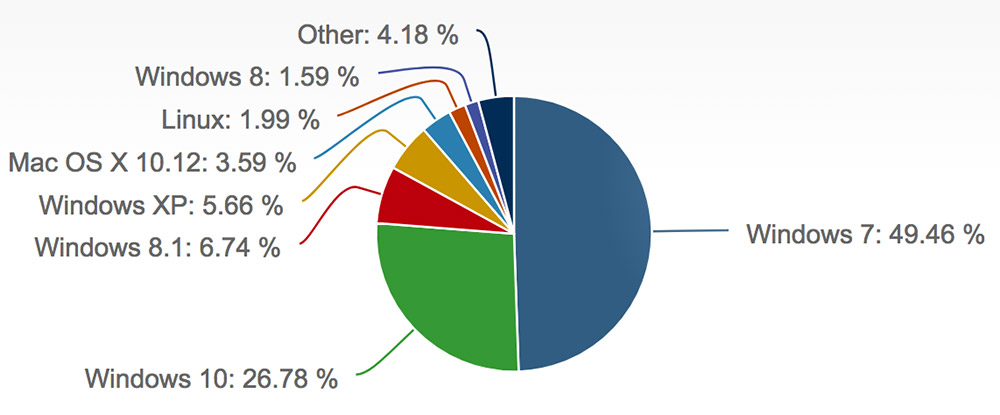
Upgrading to a current version of Windows is wise step, but also a basic one that - in and of itself - remains far from a comprehensive defense (see As Ransomware Attacks Spike, Organizations Need to Catch Up).
Patching is Hard
Digging into the weeds, the reasons why WannaCry and NotPetya had such success unveil complications that aren't easy to solve.
Both used an exploit, MS17-010, that is suspected to have been stolen from the NSA. Microsoft patched the exploit a month before WannaCry was released. But that did little to stop what was the largest single ransomware outbreak seen to date.
Patching is harder than it seems. Organizations have to ensure all applications are compatible with a patch, and related testing can require weeks. In the meantime, they're vulnerable.
Industries such as healthcare struggle with updates and patching, writes Wendy Nather, principal security strategist for Duo Security, in a recent blog post. Healthcare systems can't be updated if it impacts availability, and any changes may also have to pass time-consuming safety certifications.
"When you're paying millions of dollars for an MRI machine and suite, you expect it to last for decades, and indeed it was built for that purpose," Nather writes. "The idea of changing it by updating the software on a weekly or monthly basis was unthinkable when most of these were built."
The Public Sector
Another thorny vertical is the government sector, which is bound by byzantine budget proposals, long-scale timelines and ultimately political machinations. It's not an environment for agile development or quick change.
Corporate IT security pros may think they have a hard time convincing their board to allocate more funds to defend against unquantifiable threats. But the typical government remains a much harder sell.
"Taxpayers aren't going to pay to update hardware and software that are working just fine," Nather writes. "Legislative mandates, spending cuts and administrative rules designed to place controls on government also interfere with the agility necessary to keep up with security threats."
Still, governments are increasingly recognizing the need for better IT security, so the argument isn't falling on deaf ears. But related changes are not going to begin happening on a month-to-month basis, pacing the rapidly changing attack landscape.
One Step Forward
Microsoft has implemented many security changes that make more recent versions of Windows much more resistant to attacks than, say, XP.
But the company still can't force people to patch faster.
Also, the latest ransomware wave showed it had capabilities to spread to computers that had the latest patches. NotPetya used various tools to extract authentication credentials from infected machines and then access those computers without using either of its two software exploits (see Teardown of 'NotPetya' Malware: Here's What We Know).
NotPetya used Microsoft administrative tools such as PSExec and Windows Machine Instrumentation to reach other computers in a network.
Computer security expert Lesley Carhart writes in a blog post that those tools allow hackers to move effectively from computer to computer "in environments with poor network security architecture and implementation."
To make matters worse, some organizations do not use Microsoft's Credential Guard, which tries to protect authentication credentials from being pilfered, due to reasons that include compatibility. Credential Guard was recently introduced, in Windows 10 Enterprise and Windows Server 2016.
"All of these design and implementation problems are woefully common, repeatedly bemoaned by security professionals auditing and consulting on those networks," Carhart writes. "They are not easy or cheap problems to fix in many cases, and this is likely not going to be the case that pushes a lot of vulnerable organizations over the edge in mitigation."
Overdue Change
If Microsoft does give a discount to India, it will be hard pressed to not extend the offer elsewhere. But it would be a first good step - even if the roots of the problems of the computer security landscape are often oversimplified.
Microsoft has for years warned people that using outdated and sometimes unsupported operating systems are dangerous. But the advice has been ignored or can't be heeded. Change has to begin somewhere.











