Feds Struggle with Authentication
Examining the Latest FISMA Annual Report
It's easy to point fingers at officials who are in charge of securing federal government IT. After all, nearly every Government Accountability Office and inspector general audit identifies flaws that put those agencies' digital assets at risk.
See Also: ISO/IEC 27001: The Cybersecurity Swiss Army Knife for Info Guardians
The latest annual Office of Management and Budget report to Congress on Federal Information Security Management Act compliance shows IT security is complex and tough to effectively implement. But as Office of Management and Budget Director Shaun Donavan declares in a letter to congressional overseers, "As you will note, progress has been made in key areas of information security."
Yet, with every step forward agencies have taken, it seems they've taken a step or two back. Still, the progress made shouldn't be dismissed.
One of the government's top IT security initiatives - continuous diagnostics and mitigation, or CDM (once known as continuous monitoring) - has been implemented at 79 percent of the government's largest agencies. And the latest rendition of the Einstein 3A intrusion protection system has been rolled out to seven agencies. The Obama administration proposes spending $582 million in fiscal 2016 to extend the capabilities of CDM at all agencies and Einstein 3A to more agencies.
Another piece of good news: agencies have achieved the goal of 95 percent of external network traffic passing through trusted Internet connections, meaning that federal data passing to and from the Internet is safer.
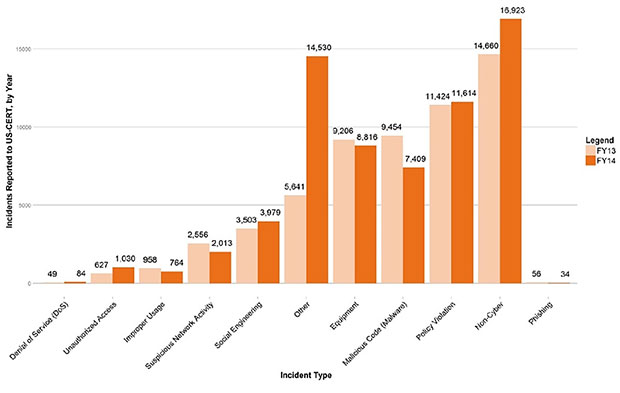
Before getting to some of the challenges that continue to plague government cybersecurity, take a few moments to look at the government's digital environment. The study shows that CFO Act agencies - the two dozen largest federal agencies - reported 67,196 security incidents to the U.S. Computer Emergency Response Team in fiscal 2014, which ended last Sept. 30. That's an increase of 16 percent from fiscal 2013. But, as the OMB questions, does the surge in incidents represent an increase of total events or the enhanced capability of the government to identify, detect, manage, record and respond to these incidents? Perhaps both.
CFO Act Agency Incidents Reported to U.S.-CERT
 U.S.-CERT Incident Reporting System
U.S.-CERT Incident Reporting System
Also, reported incidents aren't necessarily tied to computers. The largest category of breaches as the loss of hard copy records containing personally identifiable information. Reports of unauthorized access and distributed denial-of-service attacks represented a relatively miniscule 6.5 percent of all reported incidents last year from CFO Act agencies.
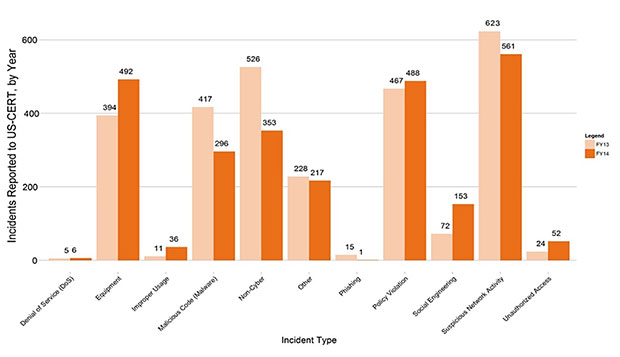
Non-CFO Act Agency Incidents Reported to U.S.-CERT
 U.S.-CERT Incident Reporting System
U.S.-CERT Incident Reporting System
An analysis cited in the FISMA report indicates that nearly one-third of federal security incidents could have been prevented by strong authentication implementation. That's a big stat.
A quick glance at the numbers, and you'd think that the government has a handle on authentication. In 2014, OMB says, 72 percent of federal agencies employed strong authentication, which is defined as signing onto systems with personal identity verification cards - a form of two-factor authentication - instead of less secure means, such as only usernames and passwords. But that figure also means that 28 percent of agencies have yet to adopt strong authentication.
Worse yet, OMB says, remove the Department of Defense from the equation, and only 41 percent of large civilian agencies employ strong authentication for network access. That's troubling. In fiscal 2014, five agencies - Labor, Housing and Urban Development (which Donovan once headed), Nuclear Regulatory Commission, Small Business Administration and Department of State - showed no use of strong authentication, while three other agencies - Office of Personnel Management, U.S. AID and Department of Agriculture - had less than 10 percent of personnel using strong authentication. Among the 24 largest agencies, only seven met the OMB's target of 75 percent of staff using strong authentication, with OMB characterizing that as a "key concern."
It's troubling that more agencies haven't implemented better authentication processes. Authentication is a fundamental part of IT security, and it's an area where security managers and agency heads should place greater emphasis.











