Cybercrime , Cybercrime as-a-service , Fraud Management & Cybercrime
'Fear' Likely Drove Avaddon's Exit From Ransomware Fray
Leading Industrial Nations Call on Moscow to Crack Down on Domestic Cybercriminals
Evidently feeling the heat over its ransomware activities, the Avaddon operation on Friday announced its retirement and released free keys for all of its victims.
See Also: The Cybersecurity Swiss Army Knife for Info Guardians: ISO/IEC 27001
Whether the individuals who run the Avaddon ransomware-as-a-service operation are really quitting the business, or just taking a break before rebranding, remains to be seen. But thanks to having the keys, two cybersecurity experts were able to release a free decryptor for all victims of Avaddon, which first appeared in March 2020.
"Fear" likely drove Avaddon's claimed retirement, according to a new report from New York-based threat intelligence firm Advanced Intelligence.
Based on chatter happening on Russian-language cybercrime forums, AdvIntel's Vitali Kremez and Yelisey Boguslavskiy write in the report that "Avaddon's demise was likely caused by political reasons - a sharp reaction of the U.S. presidential administration on the recent ransomware attacks, and the subsequent pressure applied by Russian law enforcement against local cybercrime groups prior to the upcoming Biden-Putin summit."
That summit is set to start in Geneva on Wednesday, and ransomware is very much on the agenda, as it was in the meeting of leading industrial nations that ran from Friday to Sunday in England. That Group of Seven meeting ended with a unanimous declaration from the governments of Britain, Canada, France, Germany, Italy, Japan and the United States that the UN must enforce norms for responsible international cybersecurity behavior.
"We also commit to work together to urgently address the escalating shared threat from criminal ransomware networks," the G-7 declaration states. "We call on all states to urgently identify and disrupt ransomware criminal networks operating from within their borders and hold those networks accountable for their actions."
Dear President Putin
Just in case Moscow didn’t get the message, the G-7 declaration calls on Russia to stop trying to destabilize Western democracies, to cease launching chemical weapons attacks - including against its own citizens - and also "to identify, disrupt and hold to account those within its borders who conduct ransomware attacks, abuse virtual currency to launder ransoms and other cybercrimes."
In other words, ransomware now joins election interference and chemical weapons on leading nations' list of Russia's most egregious offenses.
Since the Colonial Pipeline and JBS attacks, the White House has also been urging U.S. organizations to take ransomware attacks more seriously - treating them not as data-loss events but potentially business-ending ones. The Department of Justice has also launched a Ransomware and Digital Extortion Task Force, giving those crimes the same level of attention as terrorism.
Ransomware Realpolitik
Life comes at you fast, especially if you're running a ransomware business.
Such organizations occasionally operate as a single organization, as the now-defunct Maze appeared to be run, handling in-house everything from malware development to attacks and shakedowns.
But what's more prevalent today are ransomware-as-a-service - aka RaaS - operations, in which affiliates, who may work with multiple operations, effectively lease access to a ransomware portal. Maintained by the operator, the portal gives affiliates the ability to generate that operation's malicious crypto-locking malware executable, such as Avaddon. The affiliate takes the malware and infects victims. Every time a victim pays, the operator keeps its cut - 30% or less for Avaddon, AdvIntel says - and routes the rest of the cryptocurrency to the affiliate.
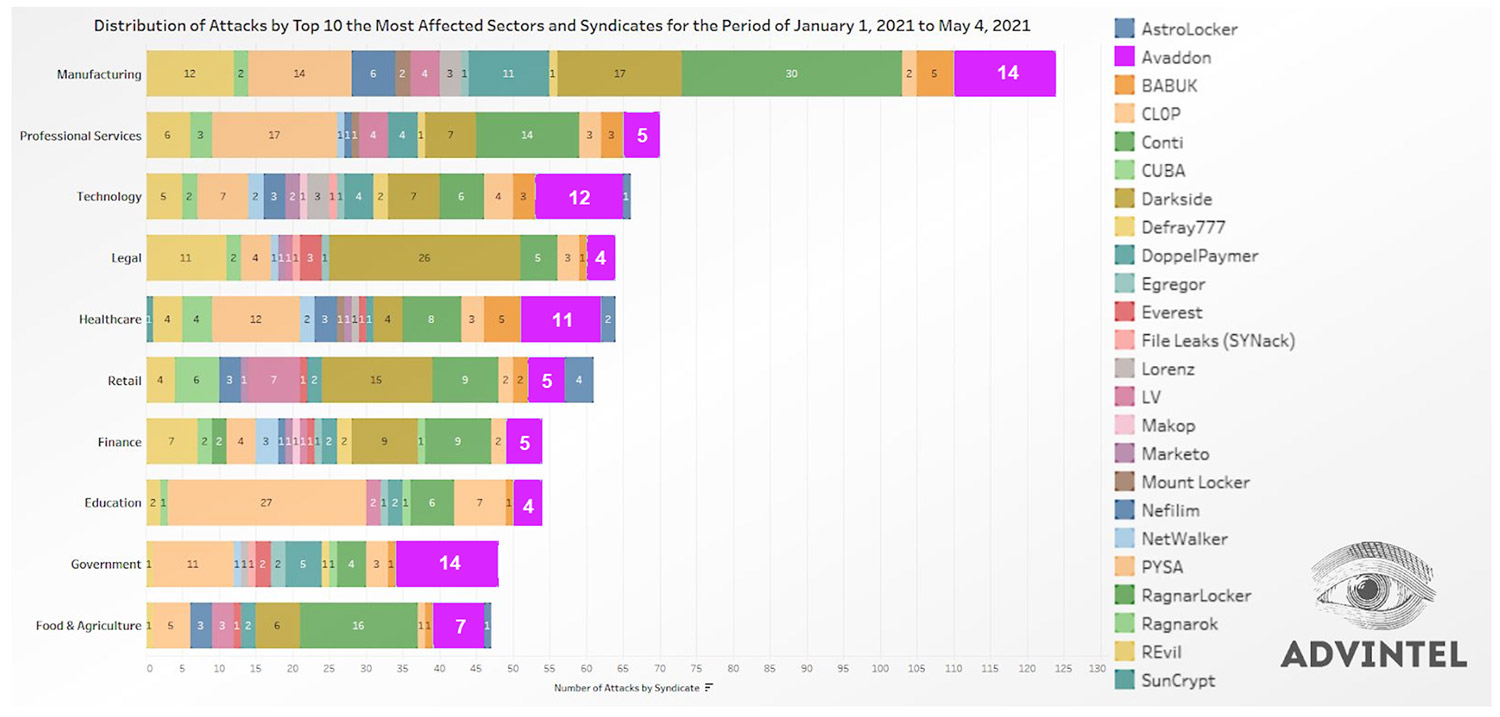
This approach, which has helped drive sky-high ransomware profits, functions as the equivalent of a cloud service for anyone who wants to wield ransomware, with operators keeping their cut. Specialization helps all the criminals win.
Or at least it did, until the Colonial Pipeline Co. attack, which disrupted systems tied to the supply of 45% of the U.S. East Coast's fuel. Now, the U.S. and allies are now treating ransomware not as a nuisance but a national security threat.
Ransomware operators have been seeing the writing on the wall. Shortly after the Colonial Pipeline hit by a DarkSide affiliate, its operator claimed that affiliates would no longer be allowed to attack those types of targets. Shortly thereafter, DarkSide announced that it would no longer work with affiliates. Another RaaS operation called Babuk, which had hit the metropolitan police department of Washington, D.C., announced that it was handing its source code off to another party.
Similarly, RaaS giant REvil - aka Sodinokibi - and Avaddon issued identical statements, announcing that affiliates were prohibited from attacking any of the Commonwealth of Independent States - which includes Russia and former Soviet countries - according to threat intelligence firm Intel 471 and others. Attacking any organization "in the public sector, healthcare, educational institutions, charitable organizations" would also be prohibited, and the operators said that "before processing the target," final approval was required from an administrator of the RaaS program. (It's not clear exactly what is meant by "processing".)
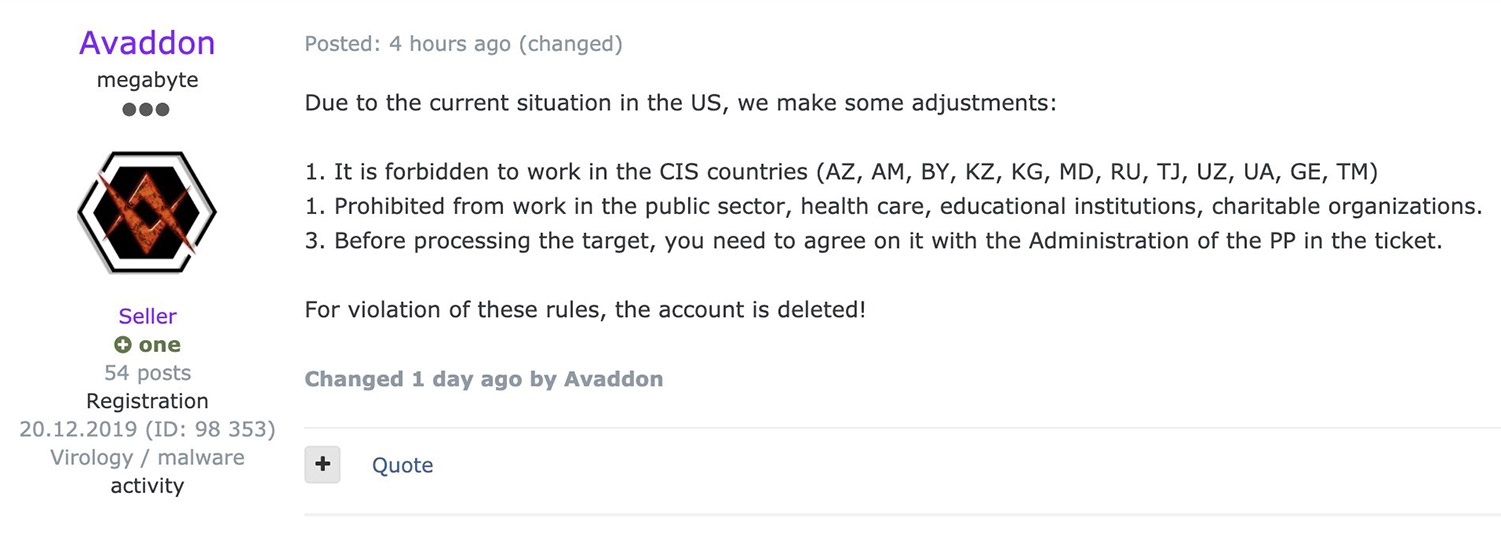
Some cybercrime forums - notably Russian-language giant XSS - have also announced restrictions on ransomware, although those may be empty promises. Intel 471 says some other supporting cybercrime ecosystem services also claimed to have shuttered, including BitMix - a cryptocurrency mixing service designed to make it more difficult to "follow the money" that was used by Avaddon, DarkSide and REvil.
Market Forces
In recent weeks, experts say, Avaddon appeared to be increasing its attack efforts in what now looks like an attempt to exit, if not in a blaze of glory, then at least profitability. "Avaddon was tied with Conti for most number of ransomware extortions published since the Colonial Pipeline attack," totaling 59 new victims, says Allan Liska, an intelligence analyst at threat intelligence firm Recorded Future who specializes in tracking ransomware activity.
Avaddon was making money hand over fist. AdvIntel, based on its analysis of victims and ransoms paid, offers a "ransonomics" estimate that Avaddon's operators - who routed about 70% of every ransom payment to the responsible affiliate, and kept the rest - earned $26 million, which it says was likely divided between at least four operators, meaning they each earned nearly $7 million over its approximately yearlong run.
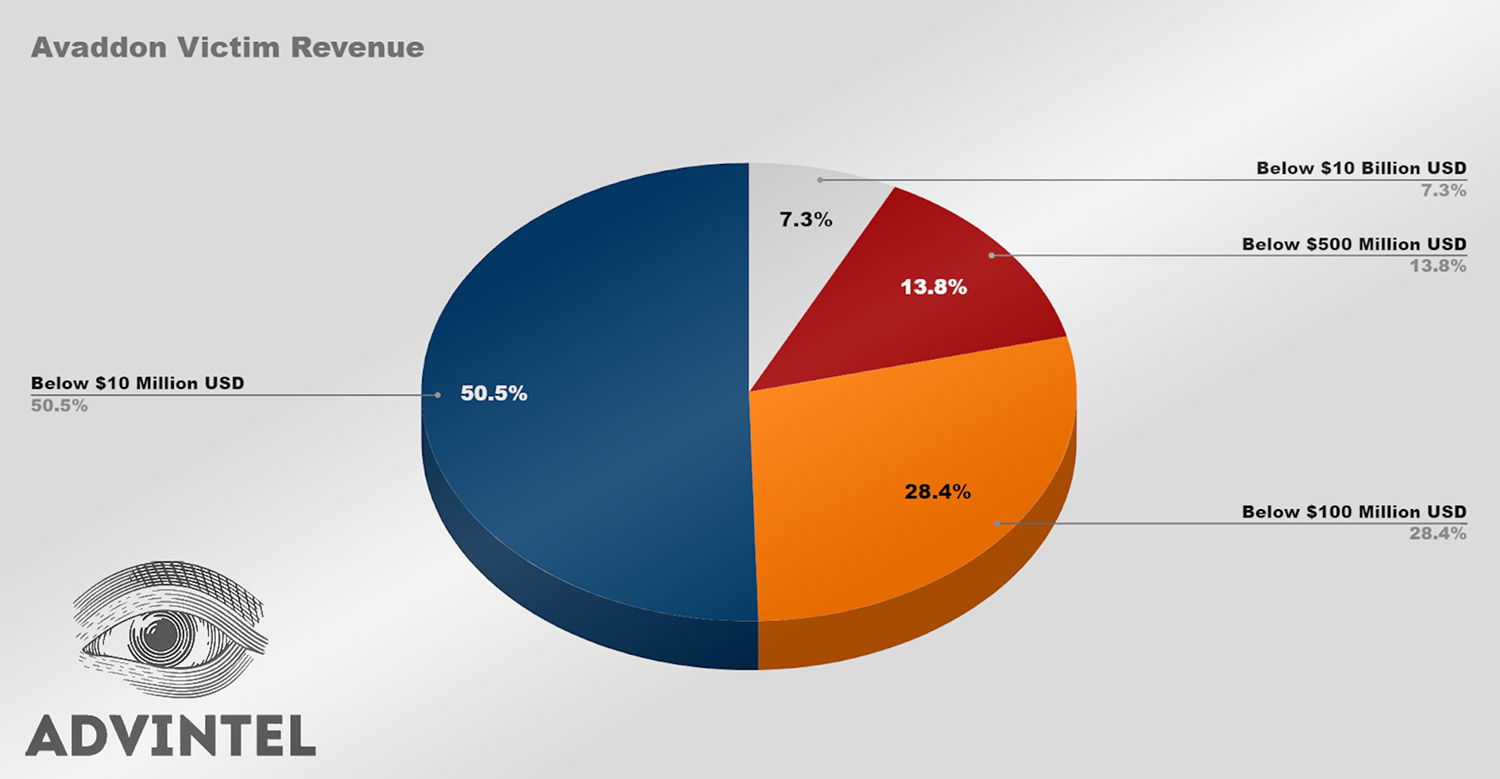
"To compare: the median annual income in Russia is estimated to be $7,000," AdvIntel's Kremez and Boguslavskiy write. "In other words, in one year of ransomware development, an Avaddon member made the same amount of money as an average Russian would make in a millennium - the best illustration of how lucrative ransomware could be for the region."
Market forces have now driven DarkSide, Avaddon and others to seek a lower profile. But will their operators really exit the ransomware life, or might they lay low and rebrand, pending whatever action Putin may take?
"A number of the operators will most likely operate in their own closed-knit groups, resurfacing under new names and updated ransomware variants," Intel 471 says.
With millions of dollars of further potential profits on offer, my money is on them waiting for the right moment to return.












