Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management
Attackers Target Oil and Gas Industry With AgentTesla
Two Campaigns Appear Tied to Global Oil Crisis, Researchers Say
Two recently uncovered spear-phishing campaigns targeted oil and gas firms in the U.S., Asia and South Africa with AgentTesla, a notorious information stealer, according to the security firm Bitdefender.
See Also: The State of Organizations' Security Posture as of Q1 2018
These two campaigns came as the COVID-19 crisis has pushed the price of oil down globally as demand deceases. At the same time, a dispute among OPEC members, as well as Russia, disrupted oil production until an agreement was reached this week to cut production by about 10 percent, according to the BBC.
Even with news of that agreement, the price of oil fell into negative territory earlier this week, according to CNBC.
Espionage Effort
Bitdefender researchers suspect that these spear-phishing campaigns were designed to spy on certain companies to gather information about how they planned to respond to the oil crisis. The report notes that AgentTesla, which has been in use since 2014, is not typically associated with attacks on the oil and gas industry.
In addition to oil and gas companies, the report notes, the spear-phishing emails attempted to target charcoal processing facilities, hydraulic plants, raw materials manufacturers as well as transportation firms in the U.S., Malaysia, Iran, South Africa, Oman, Turkey and the Philippines.
"It's impossible to tell how many victims could have been compromised, as we don't know all the intended recipients of these spear-phishing emails," Liviu Arsene, a cybersecurity researcher at Bitdefender, tells information Security Media Group.
First Campaign
The first campaign ran from March 31 to April 6, according to the report. The attackers’ messages impersonated an Egyptian oil and gas consulting firm, Engineering for Petroleum and Process Industries.
The messages invited recipients to submit a bid for equipment and materials as part of the Rosetta Sharing Facilities Project, an oil project with links to the Egyptian consulting firm, the report notes.
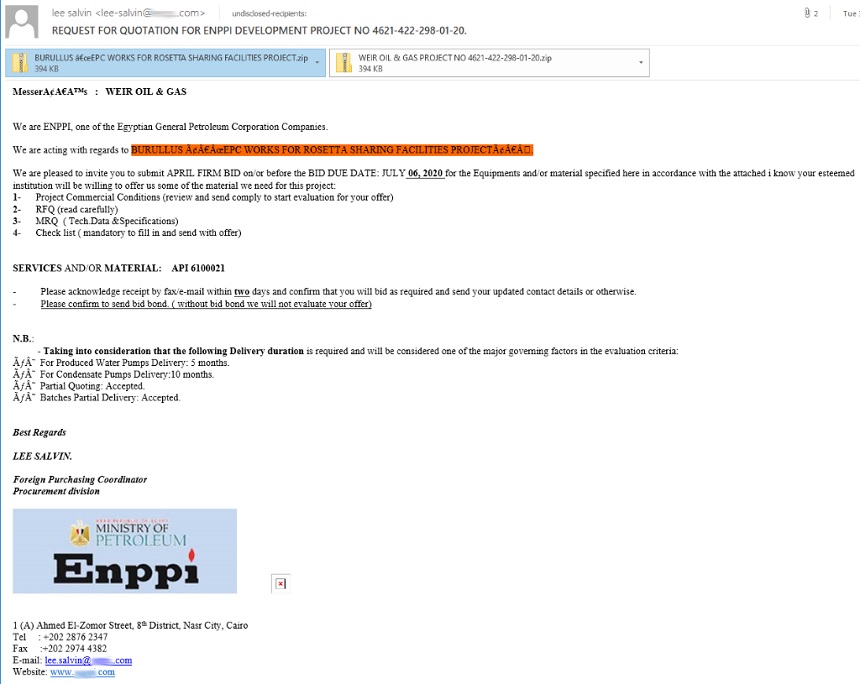
These phishing emails contained two zip files. When opened, the AgentTesla malware would then infect a device, begin harvesting credentials and connect to a command-and-control server, according to the report.
"While the email does sound legitimate by having a bid submission deadline and even requesting a bid bond, the attached archives that should contain a list of requested materials and equipment are rigged to drop the AgentTesla spyware Trojan," the report says.
Second Campaign
A second campaign, which ran for two days in April, involved phishing emails that appeared to originate with a shipping company called Glory Shipping Marine, which is based in Hong Kong. The campaign attackers targeted shipping firms in the Philippines.
The phishing emails used information about oil and chemical tankers, along with industry-specific language, to entice victims to click on malicious attachments, according to the report.
For instance, in an email sent to a victim on April 12, the attackers said they needed to send an "Estimated Port Disbursement Account" for a shipping vessel named MT.Sinar Maluku, along with information on container-flow management, the report says.
"It just so happens that there actually is a chemical/oil tanker bearing that name registered under the Indonesian flag, which had left port on April 12 and was expected to reach its destination on April 14," the report notes.
AgentTesla Enhanced
The amount of malware targeting the oil and gas industry has increased since the start of 2020, with firms in the U.S. and U.K. seen the most frequent targets, Bitdefender notes.
What makes the latest two spear-phishing campaigns unusual is the use of AgentTesla, which is typically associated with business email compromise schemes. Cybercriminals have adjusted the AgentTesla code to provide new capabilities and help the malware avoid detection, according to Bitdefender.
Earlier this month, Palo Alto Networks' Unit 42 released a report that found an increase in COVID-19 themed phishing emails that attempted to deploy AgentTesla on infected devices (see: Fresh COVID-19 Phishing Scams Try to Spread Malware: Report ).






















