3rd Party Risk Management , Business Continuity Management / Disaster Recovery , Critical Infrastructure Security
As Ransomware Variants Shift, Incidents 'Still on the Rise'
LockBit 2.0, Conti and BlackMatter Dominated Attacks in Q3, Researchers Find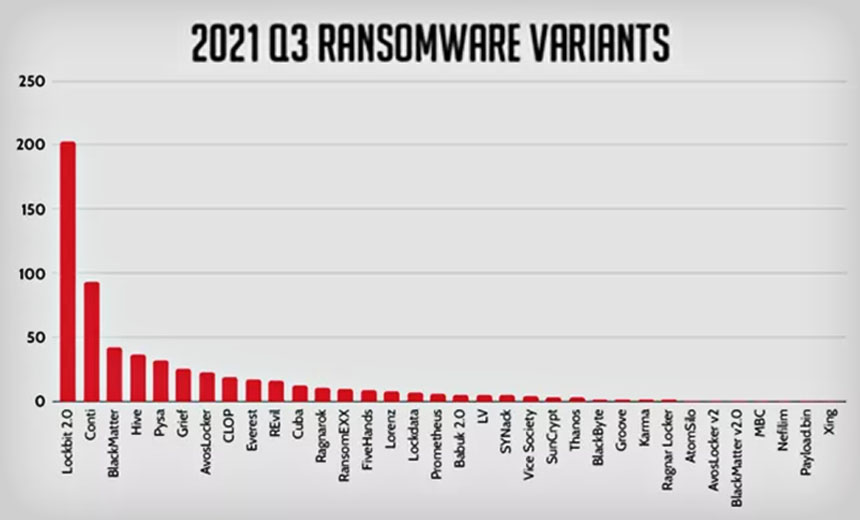
For anyone hoping to celebrate the decline and fall of ransomware by year's end, think again. Security researchers say that the ransomware soap opera remains alive and well: Some ransomware groups have exited, others have simply rebranded, the influx of new players remains constant, and highly skilled affiliates as well as initial access brokers continue to ply their trade.
See Also: Take Inventory of Your Medical Device Security Risks
Many ransomware groups continue to employ a ransomware-as-a-service model. In this model, the RaaS developer or administrator typically maintains the ransomware and a payment portal for victims and may run some attacks themselves. But typically, they'll rely on business partners - aka affiliates - who receive a customized version of the ransomware and use it to infect victims. For every victim who pays, the affiliate receives a cut.
Providers of RaaS services continue to change. Affiliates, meanwhile, may also change who they're working with, and sometimes work with more than one group at a time. All of this can make it difficult to predict what groups might target which types of victims, based on their sector, geography or size, some experts say.
4 Groups Dominate
Which ransomware operations are most active? From July through September, threat intelligence firm Intel 471 says it tracked 612 attacks tied to 35 different ransomware variants. But just four variants together accounted for the majority of attacks it tracked:
- LockBit 2.0: 33%
- Conti: 15.2%
- BlackMatter: 6.9%
- Hive: 6%
What's notable is that three of those four groups were relative newcomers. Hive, for example, was first spotted on June 26. By August, the FBI had issued a flash alert over Hive, after the group hit Memorial Health System in Ohio, among other victims.
Other fresh ransomware operations at that time included LockBit 2.0 and DarkSide, as well as ALTDOS, AvosLocker, HelloKitty and OnePercent Group.
Meanwhile, groups such as Sodinokibi - aka REvil - as well as Avaddon and DarkSide have exited in recent months, which highlights that groups are coming and going, at least in name.

"Due to law enforcement, infighting among groups or people abandoning variants altogether, the RaaS groups dominating the ecosystem at this point in time are completely different than just a few months ago," Intel 471 says. "Yet, even with the shift in the variants, ransomware incidents as a whole are still on the rise."
Intel 471's findings may differ from those of other researchers. Ransomware incident response firm Coveware, for example, says that based on actual ransomware incidents that it investigated, the strains that it saw most in Q3 were Conti, Mespinoza, Sodinokibi, LockBit 2.0 and HelloKitty.
LockBit 2.0 Surges
Based on all attacks that came to light publicly in Q3, Intel 471 says LockBit 2.0 accounted for one-third of them, and that's notable in part because the operation first appeared only in June. Already, it's been tied to some notable hits, including against consultancy Accenture.
In a double-extortion move, in the Accenture hit, attackers demanded $50 million, threatening to otherwise leak more than 6 terabytes of data they claimed to have stolen. Intel 471 says LockBit 2.0 also targeted the consultancy with a distributed denial-of-service attack - sometimes referred to as triple extortion when it's part of a ransomware shakedown - to make the incident more public and attempt to increase the pressure to pay.
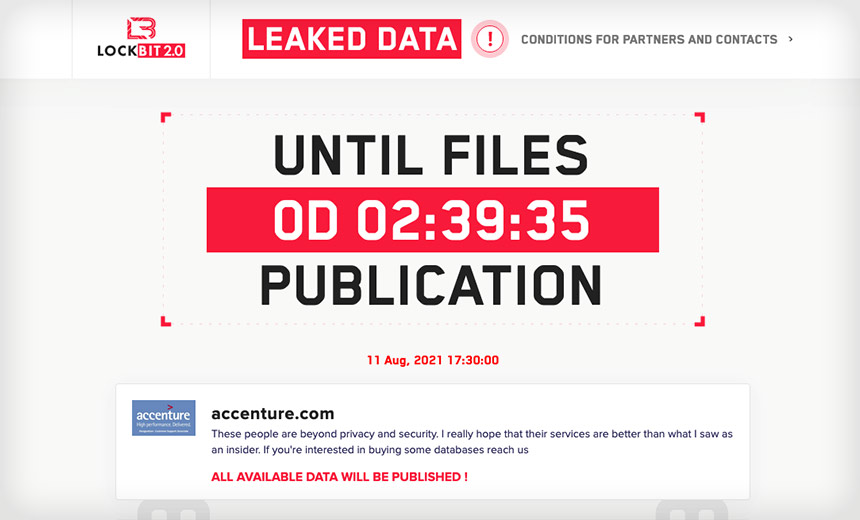
After Accenture refused to pay, the attackers carried through on their threat and leaked at least some stolen data via their data leak site.
Conti Explores Log4j
Of all now-active ransomware operations, Conti in particular has developed a reputation for ruthlessness, including hitting Ireland's national health service in May, resulting in months of disruption for the country's healthcare sector. Experts say Conti also frequently fails to provide a decryptor if a victim pays a ransom.
While the group continues to be a big player, the quantity of attacks tied to it decreased by 64% from Q2 to Q3 of this year, Intel 471 says. "This could be partly due to the operators not regularly updating and releasing victims' data on their public blog," it says.
Unusually, Conti has been taking a different approach to the RaaS model. "It is likely that Conti developers pay the deployers of the ransomware a wage rather than a percentage of the proceeds," the U.S. Cybersecurity and Infrastructure Security Agency reported in September. This approach, however, appears to have led to some animosity from deployers, with one of them leaking the group's attack playbook in retaliation for what he said were insufficient wages.
Further disruption could be ahead. In November, Swiss firm Prodaft Threat Intelligence reported that it had exploited a flaw in Conti's infrastructure, allowing it to breach the group's systems and gain insights into its operations. In a report, Prodaft says it identified actual IP addresses used by Conti, chat logs with victims, and 113 bitcoin addresses for receiving ransom payments, of which 100 were tied "to a single ransomware attack in which the victim requested to pay Conti in 100 separate transactions in order to hide the payment from tax and audit authorities."
Prodaft also reports that Conti appears to be tied somehow to the Ryuk group. Known ransoms paid to Ryuk in 2020 totaled nearly $100 million, blockchain analysis firm Chainalysis has reported.
"Based on an analysis made on ransomware samples and a comparison of bitcoin wallets used for receiving ransom payments, there is an undeniable connection between Conti and Ryuk ransomware teams," Prodaft reports. "They may be the same team, or different teams that share members and resources with one another."
Conti, meanwhile, has continued to evolve. Threat-intelligence firm Active Intelligence says the operation appears keen to exploit the recently discovered Apache Log4j flaw and has been actively scanning for the vulnerability. By Wednesday, it says, Conti appears to have begun using endpoints it's already infected with Cobalt Strike to exploit VMware vCenter server management software, into which Log4j is built. Exploiting vCenter can give the attackers the ability to move laterally in a victim's network, Advanced Intelligence reports.
The Power of Rebranding
While ransomware operations come and go, sometimes it's only in name. The BlackMatter operation that debuted this past summer, for example, was simply a rebrand of DarkSide, after its hit on Colonial Pipeline in the U.S. caused consumers to panic-buy fuel, triggering a political firestorm. Indeed, the FBI is offering a reward of up to $5 million for information tied to anyone working with DarkSide and its BlackMatter spinoff, including any affiliates.
Hence the DarkSide crew appears to have deep-sixed the name and rebooted as BlackMatter. But any attempt to make a clean break was short-lived, as security experts quickly spotted similarities not just in the code but also in the cryptocurrency wallets being used to receive ransom payments.
For crime groups operating from Russia or other countries that won't extradite their citizens, however, it's not clear that such revelations alone will disrupt their operations, although Western governments have said they're more actively attempting to hack into and disrupt ransomware operations' infrastructure.
Even so, "developers are still easily shutting down popular variants, laying low, and coming back with finely tuned malware used by themselves as well as affiliates," Intel 471 says. "As long as the developers can remain in countries where they are granted safe harbor, the attacks will continue, albeit with different variants."




















