Account Takeover Fraud , Anti-Phishing, DMARC , Email Security & Protection
Abnormal Security Raises $210M to Push Beyond Email Defense
Abnormal Wants to Apply Its Account Takeover Prevention Technology to New Areas
Abnormal Security has closed a $210 million funding round on a $4 billion valuation to apply its account takeover prevention technology to areas other than email.
The San Francisco-based email security firm wants to use its artificial intelligence and behavior analytics expertise to protect accounts across more systems and SaaS platforms as well as in environments such as Workday and Salesforce, according to Abnormal CISO Mike Britton. The Series C funding round was led by Insight Partners and brings Abnormal up to $284 million of outside funding since its 2018 founding.
"We look at ourselves as more than just an email security platform in the future," Britton tells Information Security Media Group. "That's our future road map and where we see ourselves going."
Abnormal Security was founded in 2018 and employs 432 people, up from just 175 employees a year ago, according to LinkedIn and Crunchbase. The company closed a $50 million Series B round led by Menlo Ventures in November 2020 and a $24 million Series A funding round led by Greylock Partners in November 2019.
Britton says the company's technology excels at correlating various signals to distinguish legitimate user activity from abnormal behavior or possible malicious activity. Abnormal has invested heavily in recent years to understand what normal behavior looks like in Office 365 or Google Workspace, and Britton says the company need to gain a better understand of key IT signals in other areas of the workplace (see: Business Email Compromise: Why It Works - and How to Prevent It).
Abnormal is looking to extend its account takeover prevention muscle to SaaS platforms and corporate IT that's heavily used in the Fortune 500, such as Salesforce and Workday, which are the leading CRM and HR management platforms for many large enterprises, Britton says. Many enterprise SaaS tools today are API or event-driven, meaning that Abnormal's ability to detect logging or account sign-ons will be handy.
"There are a variety of things that we can do for each customer and across tenants where we can really hone in and say, 'Okay, this is indicative of an attack,' or, 'This is indicative of normal behavior,'" Britton says.
A New Approach to Security Awareness Training
For Abnormal's core email security technology, Britton says the company hopes to use the $210 million to increase the efficacy of its ML and AI models and expand the threat indicators that can be pulled out. The company plans to build out capabilities around security awareness training as well as pursue new integrations with third-party SIEM or SOAR providers, he says.
According to Britton, Abnormal's approach to security awareness training would be different from that of players such as Cofense and Wombat - now part of Proofpoint - that rely on a library of templates. Instead, Abnormal is hoping to dynamically take real-world threats and flip them into training simulations in real time with the click of a button so users can see how their defenses fare against the latest sophisticated threats.
"It just continues to show the value of your preventative tools," Britton says. "It also makes it real-world and realistic to your users so that they can't say, 'Oh, I wouldn't have fallen for that. That's not a real attack."
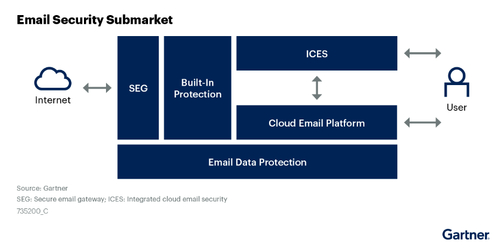
Abnormal has historically been used to augment either existing secure email gateways from Mimecast, Proofpoint, Broadcom or Cisco or to augment native defenses offered by Microsoft or Google. But Abnormal recently rolled out an Integrated Cloud Email Security, or ICES, platform that can displace secure email gateways altogether, and Britton says Fortune 500 CISOs are becoming increasingly open to that.
"It's scary and it's hard to switch off your email gateway, because ... when you cut over from that to pointing straight to Office 365 or Google, there's potential risk for business interruption of email," he says.
US Government, Global Expansion on Tap
From a geographic standpoint, Britton says Abnormal wants to use the money to build upon last year's expansion into the United Kingdom, Australia and New Zealand. Abnormal has the opportunity to both do more in those countries by getting into marketplaces as well as expand into other regions, such as the Nordics; Benelux, which is Belgium, the Netherlands and Luxembourg; and Singapore; according to Britton.
"There's a big market in both [the U.K. and Australia/New Zealand]," Britton says. "We feel there's an opportunity for us to displace incumbent secure email gateways."
Britton says Abnormal is strongest in verticals such as financial services, healthcare and manufacturing that are heavily represented in the Fortune 100 and on the Fortune 500.
Abnormal also wants to use Series C proceeds to embark upon the FedRAMP journey and take on U.S. government agencies as customers, according to Britton. The company has a team assembled, is looking for the right civilian agencies to sponsor it, and has drawn up a playbook that has the company seeking the authority to operate in the federal market in the second half of 2022 and first half of 2023.
"There's been a large push to modernize technology in the federal government, a large push for cloud, and we feel like we have a first-mover advantage when it comes to the newer generation of email security solutions," Britton says. "It's a very wide-open market with the government agencies, especially the civilian agencies, so I think there's a lot of addressable market there."