Anti-Phishing, DMARC , Cybercrime , Cyberwarfare / Nation-State Attacks
10 Cyberattacks Investigated Weekly by UK
Majority of Incidents Trace to Hostile Nation-States, NCSC Says
The U.K. government's incident response teams have investigated more than 1,000 significant incidents in the past two years. That works out to more than 10 incidents per week targeting U.K. organizations, the majority of which appear to trace to nation-state attackers.
See Also: 2018 Banking Threat Landscape: An Inside Look at How Cybercriminals Target Financial Services
So says the National Cyber Security Center, which is part of the U.K's GCHQ signals intelligence agency, in its second annual review.
Broadly equivalent to the Australian Signals Directorate and the U.S. National Security Agency, GCHQ - short for Government Communications Headquarters - is the U.K.'s signals intelligence, cryptographic and information assurance agency.
It's been a busy year for the NCSC, which serves as GCHQ's public-facing division. Earlier this year, together with the FBI, it issued an alert to businesses warning that Russian attackers were prepositioning themselves on systems in some critical sectors and providing advice on how to expunge attackers from their systems (see US, UK: Russian Hackers Deeply Embedded in Routers, Switches).
"We are calling out unacceptable behavior by hostile states and giving our businesses the specific information they need to defend themselves," says Ciaran Martin, head of the NCSC.
1,000 Serious Incidents and Counting
Since NCSC launched, Paul Chichester, who heads the agency's incident response team, says it has logged 2,011 incidents, of which about half - including 557 in the past 12 months - merited further investigation. In other words, NCSC's incident responders investigate, on average, more than 10 significant incidents per week.
"The majority of these incidents were, we believe, perpetrated from within nation-states in some way hostile to the U.K.," Martin says. "They were undertaken by groups of computer hackers directed, sponsored or tolerated by the governments of those countries. These groups constitute the most acute and direct cyber threat to our national security."

Attack Groups Blend
Martin's choice of language is not accidental. At the Infosecurity Europe conference in London in June, Robert Hannigan, who headed GCHQ until early last year, said one major takeaway seen by intelligence agencies is that cybercrime groups and nation-state hackers are increasingly blurring together.
"In some cases, you can see these groups sitting in the same room, and in some cases, you can see where people have been conducting state activity during the day, and then doing crime activity at night," Hannigan told attendees. "It's an interesting mixture of profit and political intent."

Under Hannigan's leadership, GCHQ stood up NCSC in 2016.
NCSC includes CESG - the information security arm of GCHQ - as well as the Center for Cyber Assessment, together with the U.K.'s computer emergency response team, CERT-UK, and the cyber-related responsibilities of the country's Center for the Protection of National Infrastructure (see UK Stands Up GCHQ National Cyber Security Center in London).
Incident Responders
Following major breaches, NCSC often issues public guidance to breach victims. In addition, it often goes onsite to investigate intrusions and help breached businesses recover (see Hacker Flies Away With British Airways Customer Data).
"Our experience engaging with the NCSC following the discovery that some of our customers' data had been subject to unauthorized access has been beneficial," Carphone Warehouse says, referring to a major breach it detected in June (see Dixons Carphone: 10 Million Records Exposed in 2017 Breach). "The NCSC has been supportive and provided valuable advice which has helped both shape our response and ensure that we are taking all appropriate steps to ensure the security of our customers' data."
NCSC also continues to offer guidance to organizations, from the types of questions boards of directors should be asking their information security leadership to best practices for working with passwords (see Experts' View: Avoid Social Networks' Single Sign-On).
Better Automated Defense
In terms of other success stories, the NCSC says that thanks to its "active cyber defense" initiative, it's helped reduce the number of phishing sites that get hosted on U.K.-based system. "The internet was not designed with security in mind and, from a security perspective, there are significant flaws in the way it operates," Martin says.
The U.K. government in 2016 launched ACD as a way to automate, as much as possible, cybersecurity defenses across the government.
"We were the first in the world to attempt this, reducing the damage done by large-scale but basic cyberattacks, freeing up our world-class operatives to focus on the most potent threats," Martin says. "Our aim is to take away as much of the harm from as many people as we can, as often as we can."
Since the program launched, from June 2016 to this past July, the NCSC says that the proportion of the world's phishing sites that get hosted in the U.K. has fallen from 5.3 percent to 2.4 percent. In addition, NCSC helped to remove nearly 140,000 phishing sites operating in the U.K., as well as 14,000 worldwide that spoofed the U.K. government.
For sites spoofing government brands, NCSC says that it's reduced from 42 hours in 2016 to 10 hours this year the median time that it takes to get a spoofed site removed.
Based in part on those results, the NCSC says it's hoping to roll out the program to additional sectors - beyond the government - as soon as possible.
Active Cyber Defense: 4 Components
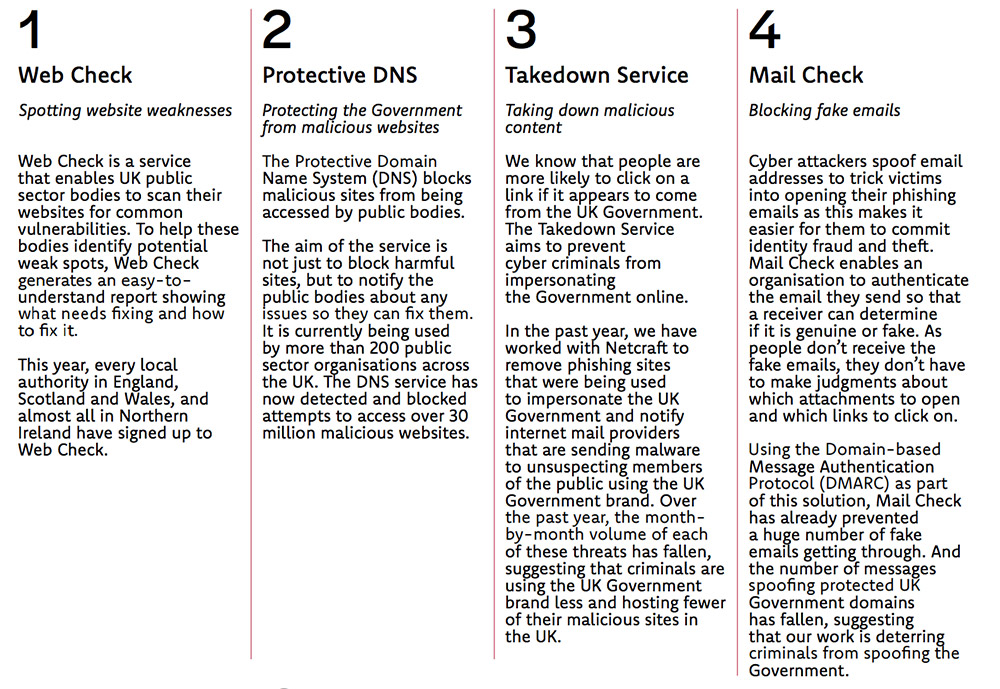
Martin says that while ACD shows what a government-promulgated program can do, making British organizations of all sizes savvier at cybersecurity defense remains a key aim.
"Getting the right cybersecurity capabilities for an organization starts with a better understanding of the risks. No one is asking British citizens and businesses to have cyber defense capabilities akin to those of a nation-state," Martin says. "They just need to be good enough to fend off what an organization can reasonably assess to be the risks it faces. Defenses also need to be good enough to contain attacks that do get through, as some inevitably will."
Alert: Supply Chain Risks
Looking ahead, NCSC says an increasing area of concern involves mitigating supply chain risks, including as the telecommunications sector begins adopting 5G (see What's Riding on 5G Security? The Internet of Everything).
"That's a key challenge for our experts who lead on our program to protect the nation's most critically important networks, alongside their work on our social security payments systems, the new generation of civil nuclear reactors, our systems to protect our national defense secrets, and the payments and clearing networks that underpin the U.K.'s world-leading financial system," Martin says.




















