Yahoo Hacked by Cybercrime Gang, Security Firm Reports
1 Billion Accounts Stolen by 'Professional Blackhats,' InfoArmor Says
The record-breaking Yahoo breach wasn't perpetrated by nation-state attackers, as Yahoo has claimed, but rather by a group of "professional blackhats from Eastern Europe" who are also suspected of stealing and reselling customer data from LinkedIn, MySpace and Tumblr, according to a new report from the security firm InfoArmor (see Yahoo Breach: The Great 'Nation-State' Cop Out).
See Also: The Alarming Data Security Vulnerabilities Within Many Enterprises
Yahoo didn't immediately respond to a request for comment on the InfoArmor report.
But a Yahoo spokesman previously told Information Security Media Group: "As we disclosed on Sept. 22, a recent investigation by Yahoo has confirmed that a copy of certain user account information was stolen from our systems in late 2014 by what we believe is a state-sponsored actor. Our investigation into this matter is ongoing and the issues are complex."
Now, however, Arizona-based InfoArmor, which sells products designed to protect against employee identity theft, claims that it's traced the Yahoo data theft to a group of hackers that it dubs "Group E." InfoArmor says the group apparently exfiltrated the data via a remote attack.
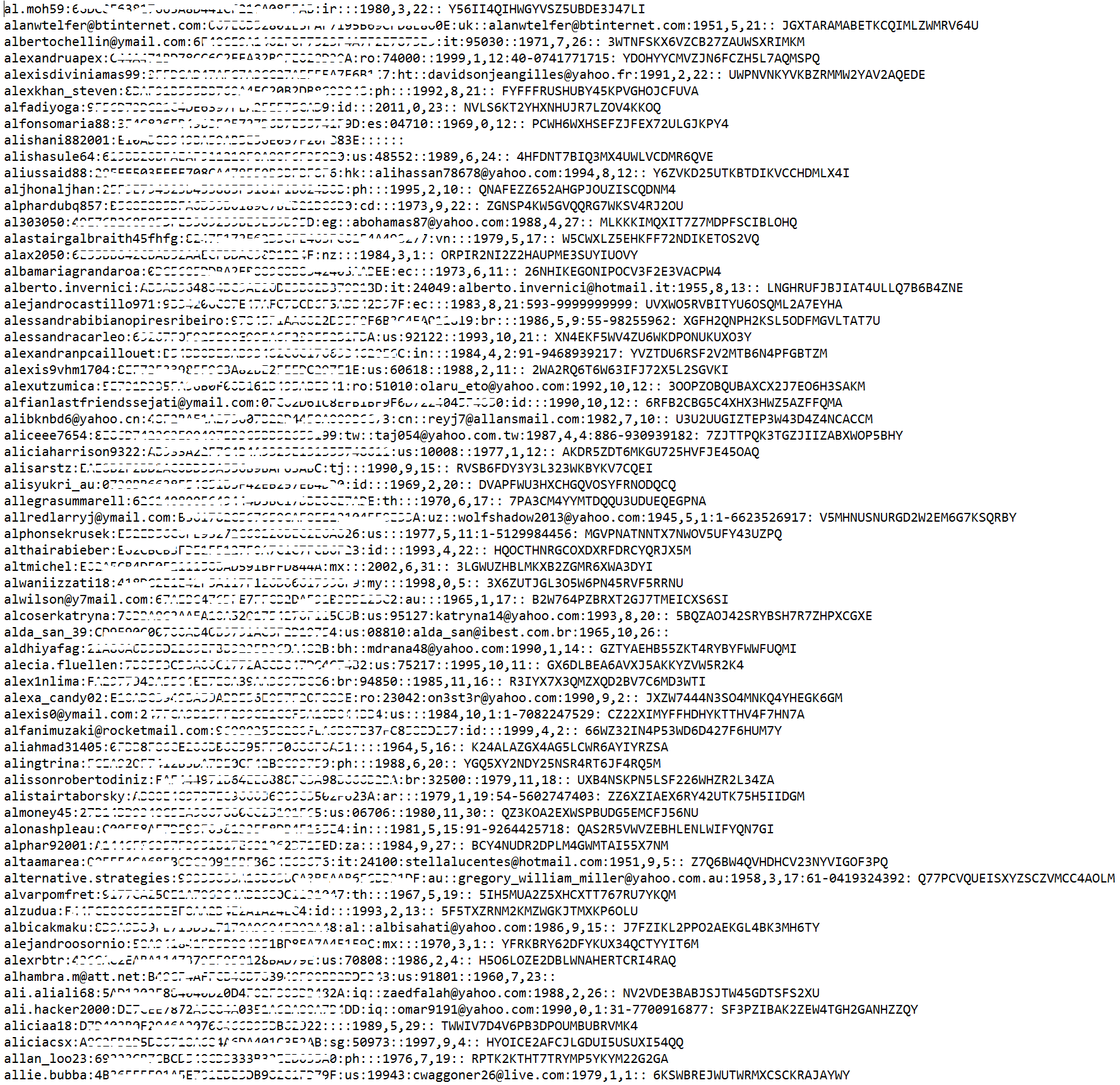
"The bad actors exfiltrated the data in segments, which is supported by the fact that the database dump is divided into over a hundred equal parts, delivered in different files that are organized alphabetically by the name of user accounts," according to InfoArmor's report.
"The actual number of Yahoo accounts affected could be more than 1 billion, but is much higher than the 500 million reported which includes dormant accounts and bot accounts," it adds.
InfoArmor appears to have access to at least some of the exfiltrated data. The Wall Street Journal reports that it gave InfoArmor 10 active Yahoo IDs and the firm successfully cracked and shared eight of the associated passwords in less than a day - reporting that the other two passwords were likely more complex and would have taken longer to crack. InfoArmor also was able to recover the correct date of birth, phone number and ZIP code associated with the eight accounts, the newspaper reports.
InfoArmor's report says the stolen Yahoo data included:
- Yahoo login (ID);
- Country code;
- Recovery email (linked with the profile);
- Date of birth;
- Hash of Password (MD5);
- Cellphone number;
- ZIP code, if it was provided by the user for password recovery.
As of Sept. 27, "the actual Yahoo data dump is still not available on any underground forums or marketplaces," InfoArmor's report says. Instead, it says the data is being monetized via a proxy for the group, "based on the sale of particular records from the dump, which can be delivered based on the specific criteria of the buyer - login, recovery e-mail, geography, etc."
No State Sponsor
Andrew Komarov, InfoArmor's chief intelligence officer, tells ISMG in an interview that Group E are professional criminals, and that they've been involved in breaches relating to MySpace, Tumblr and LinkedIn.
"We have been monitoring the group since their early hacks that happened in 2012/2013 and know the timeline of their activities along with some of their customers," he says. "They have nothing to do with any state-sponsored parties, and act as professional cybercriminals that specialize in large-scale data breaches."
InfoArmor's report claims that the stolen Yahoo data has been exclusively sold - by a Group E proxy - just three times, beginning in 2015. "We determined that one of the first deals occurred with a state-sponsored party who had interest in exclusive database acquisition," its report says. Even so, "two other transactions took place with notable cybercriminals who planned to use the data for spam campaigns against global targets, monetizing their activities through their own underground affiliate networks."
Peace of Mind: No Real Deal
The InfoArmor report also offers new insights into the activities of the darknet marketplace sellers and English-speaking "threat actors" known as Tessa88 and Peace_of_Mind, a.k.a. Peace. Tessa88 has been selling stolen LinkedIn and MySpace data. He also claimed to be selling data from Dropbox, although security expert Troy Hunt told ISMG that the latter was actually a mishmash of Tumblr and Twitter data.
On Aug. 2, meanwhile, Peace claimed to offer for sale 200 million Yahoo account credentials on the Real Deal, a darknet marketplace. But his asking price of only 3 bitcoins - worth about $1,800 - raised immediate red flags. As InfoArmor's report notes: "For any experienced threat intelligence analyst, the price of 3 [bitcoins] for 200 million Yahoo user accounts is suspiciously strange and has no rational explanation."
After Yahoo last week warned that it had been breached and that 500 million accounts had been stolen, it said that it had no proof to back up Peace's claims, after some media outlets suggested that Peace may have been responsible for the breach. "Yahoo has never had reason to believe there is any connection between the security issue disclosed on Sept. 22 and the claims publicized by a hacker in August 2016," a Yahoo spokesman told ISMG. "Conflating the two events is inaccurate."
InfoArmor has likewise dismissed Peace's claimed possession of stolen Yahoo data. "After extensive analysis and cross reference against the data breach intelligence systems of InfoArmor, it was determined that the dump is based on multiple third-party data leaks, which have no relation to Yahoo," its report says. "Presumably, the threat actor specially misrepresented this data set in order to sensationalize and sell it for the purpose of monetizing his efforts following the negative impact of his relationship with tessa88."
Congress Questions Detection Delay
Following Yahoo's data breach alert this month, Congress hasn't been silent. The Senate's ranking Judiciary Committee member, Patrick Leahy, D-Vt., wants to hold a hearing on the matter, an aide tells the news website The Hill.
On Sept. 27, a letter from six Democratic senators - Leahy, as well as Richard Blumenthal, Al Franken, Ron Wyden, Edward J. Markey and Elizabeth Warren - demanded that Yahoo CEO Marissa Mayer fully describe what Yahoo knew, and when, as well as what it's now doing to protect users. "Press reports indicate the breach first occurred in 2014, but was not discovered until August of this year," the senators noted in their letter to Mayer. "If this is accurate, how could such a large intrusion of Yahoo's systems have gone undetected?"
Sen. Mark Warner, D-Va., on Sept. 26, asked the U.S. Securities and Exchange Commission if Yahoo had fulfilled its obligations to inform investors about the data breach. "Disclosure is the foundation of federal securities laws, and public companies are required to disclose material events that shareholders should know about," Warner said in a letter to Mary Jo White, the SEC's chairwoman.
He also used the incident to call on Congress to pass a national data breach notification law. Despite discussing breach-related laws for years, Congress has failed to enact any such legislation.
Troubled by news of @Yahoo hack affecting 500+ m. It's time Congress creates a uniform notification standard to protect consumers.
— Mark Warner (@MarkWarner) 22 September 2016
Detection Delays are Common
The two-year lag between the breach occurring and Yahoo warning customers, however, isn't that unusual. According to cybersecurity firm FireEye's Mandiant division, organizations require on average 146 days to discover they've been breached. Also, 53 percent of compromised organizations first learn that they were breached only thanks to an external entity.
But there's a potential wrinkle. Allegedly, Yahoo detected the 2014 attack against it several weeks after the breach occurred, anonymous sources have told The Wall Street Journal. That means Yahoo may have failed to spot that data relating to at least 500 million accounts was exfiltrated.
Whoever stole the data appears to have kept a low profile, according to InfoArmor's report.
Dramatically underestimating the impact of a data breach also isn't unusual. LinkedIn, for example, underestimated how badly it was breached in July 2012, earlier this year revising a warning that 6.5 million accounts had been hacked, which was based on those accounts having been uploaded to an underground forum. In fact, more than 164 million records had been compromised, which became clear when they showed up for sale in May on a darknet marketplace by Tessa88. The data was later resold by Peace.
LinkedIn subsequently faced intense criticism for having failed to force all users to reset their passwords in 2012. Similar criticism is now being leveled at Yahoo, which is already the focus of breach-related lawsuits.
The impact of the breach revelations on Yahoo's pending sale to Verizon for $4.8 billion also remains to be seen.
















